Iranian Cybercriminal Gang ‘OilRig’ Targeted Iraqi Governmental Infrastructure with Malware
- Iranian hacker group OilRig was seen deploying several backdoors in a complex attack on government entities in Iraq.
- The threat actor compromised the targets’ systems via emails containing malicious documents.
- The cyberattack is part of a covert cyber espionage operation.
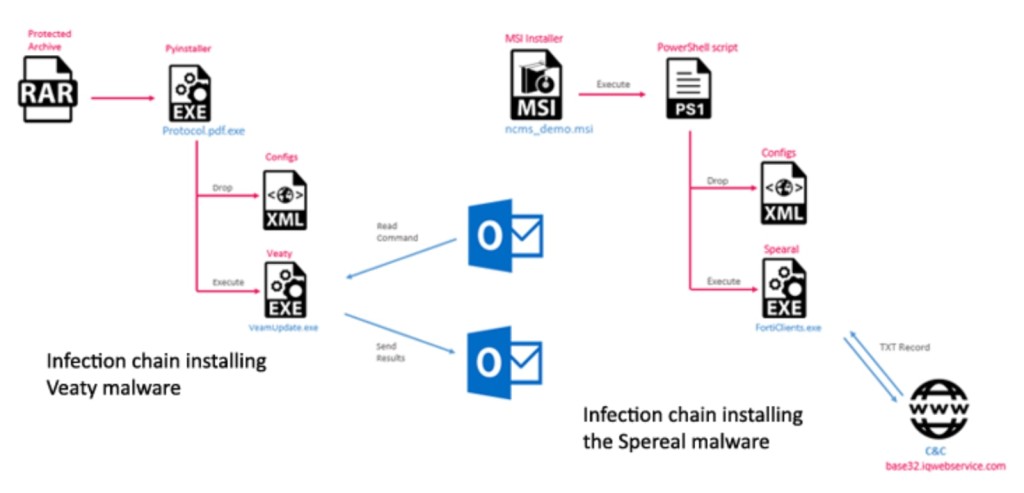
A sophisticated cyber attack orchestrated by the Iranian cybercriminal group OilRig targeted Iraqi governmental entities. The attack was executed using a newly identified set of malware, Veaty and Spearal, to infiltrate various Iraqi networks, including critical government infrastructure.
Significant overlaps exist between the methodologies used in this campaign and those associated with known APT34 malware families such as Karkoff, Saitama, and IIS Group 2. These malware families have historically been associated with the Iranian Ministry of Intelligence and Security (MOIS), suggesting a continued pattern of cyber espionage activities in the region.
CheckPoint researchers identified the samples of Veaty and Spearal, two .NET backdoors that use DNS tunneling for communication. Analysis of the threat actors’ infrastructure led to the discovery of a third backdoor that facilitates SSH tunneling.
The threat actor leveraged advanced techniques to penetrate Iraqi entities, including a passive IIS backdoor – a newer variant of the backdoor previously reported by ESET and linked to the IIS Group 2, also attributed by Symantec to GreenBug, known as APT34.
The cybercriminals also used DNS tunneling and command and control (C2) communication via compromised email accounts, facilitating covert data exfiltration and C2 communication.
A custom toolset designed for precise targeting was used, coupled with methods typical of Iranian threat actors, such as a custom DNS tunneling protocol and an email-based C2 channel using compromised accounts within the victim's organization.
They also employed malicious IIS Modules linked to previous APT34 operations, reinforcing the connection to Iranian MOIS-affiliated cyber activities.
The initial infection was achieved via a series of files that use double extensions to masquerade as document attachments, which security researchers believe were spread via social engineering.
Recently, Iranian state-sponsored threat actor Peach Sandstorm, also known as APT33, was seen deploying a new custom multi-stage backdoor in attacks targeting the U.S. and U.A.E. satellite, communications equipment, oil and gas, and federal and state government sectors, conducting intelligence gathering via the professional networking platform LinkedIn and password spray attacks.