Iranian-Backed APT42 Intensifies Phishing in Israel and Targets Both U.S. Presidential Campaigns
- Iranian cybercriminal group APT42 was observed intensifying the efforts it directs toward Israel and U.S. phishing campaigns.
- The same hacker gang targeted important accounts of individuals connected to both U.S. presidential campaigns.
- The threat actors try to abuse Google services like Sites, Drive, Gmail, and others to lure victims.
Iranian state-backed threat actor APT42 was confirmed to target high-profile accounts of both sides of the political spectrum connected to the upcoming U.S. presidential election, aggressively seeking to compromise both the Democratic and Republican campaigns, a new report by Google’s Threat Analysis Group (TAG) said.
The notorious cybercriminal gang, which is also associated with Iran’s Islamic Revolutionary Guard Corps (IRGC), was also seen stepping up its targeted phishing campaigns against Israel and Israeli military, government, and diplomatic organizations, as well as former senior Israeli military officials.
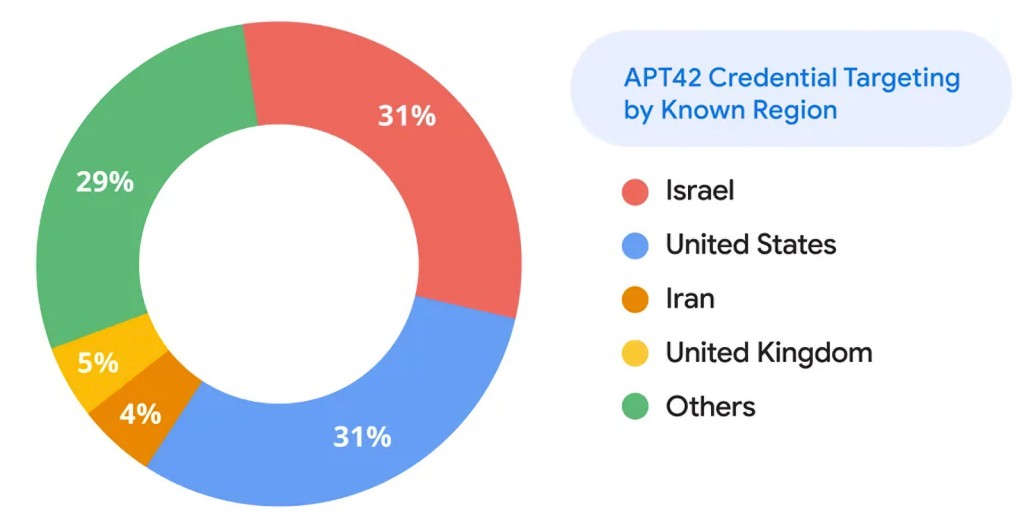
In the past six months, APT42 directed roughly 60% of its known efforts to high-profile users in Israel and the U.S., including current and former government officials, political campaigns, diplomats, think tank workers, NGOs, and academic institutions connected to foreign policy.
Iranian state actors use increasingly sophisticated tools and also try to abuse services like Google (i.e., Sites, Drive, Gmail, and others), Dropbox, OneDrive, and others.
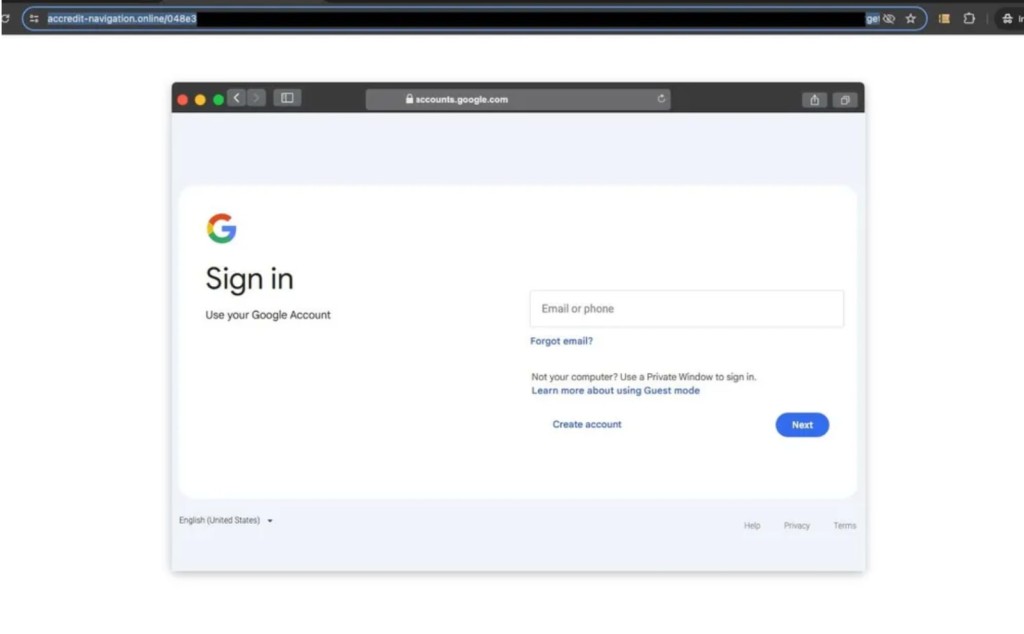
The TAG report says APT42 employs a browser-in-the-browser phishing kit often delivered via URL shorteners and a sophisticated credential harvesting tool targeting Google, Hotmail, and Yahoo users. These tools are used in malicious campaigns that often start with phishing links contained in the email body or a PDF attachment.
Sometimes, the lure is a video meeting, and a phishing page asks the victim to log in, such as fake Google Meet landing pages. Other lures include OneDrive, Dropbox, and Skype. The PDF attachment lure directs victims to platforms like Signal, Telegram, or WhatsApp, where the attackers may send a phishing kit to harvest credentials.
The cybercriminals impersonated the Washington Institute for Near East Policy in multiple campaigns since April 2024 and even the Institute for the Study of War.
APT42 targeted about a dozen people with credential phishing, including current and former government officials and individuals, and continues to attempt to compromise the personal accounts of individuals affiliated with President Biden, Vice President Harris, and former President Trump.
In May, Iranian government-backed hackers breached the account of a county-level official with minimal access permissions and, a few weeks after that, tried infiltrating the account of an important official via spear-phishing.
The U.S. State Department identified six Iranian security officials linked to the IRGC reportedly responsible for the cyberattacks on U.S. water utilities in 2023 and is offering a $10 million reward via the Rewards for Justice program for information leading to the identification or location of these individuals.