iPR Software Exposed Thousands via a Humongous Corporate Data Leak
- A marketing & digital publishing company has exposed the data of hundreds of high-profile entities.
- The data remained publicly accessible for at least a full month after the owner was notified.
- The consequences of this incident are very serious, as the type of data that was leaked is very sensitive.
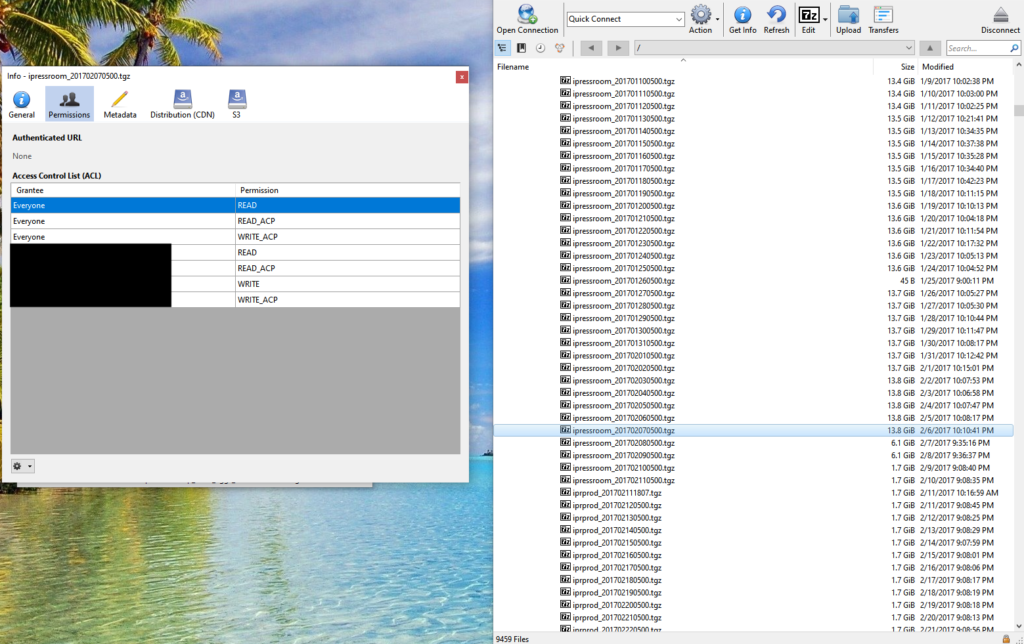
The UpGuard Research team is disclosing a massive data leak originating from iPR Software - a digital publishing, digital asset management, and custom integrated solutions provider. The data collection that was found in an unprotected Amazon S3 storage bucket, contained thousands of sensitive corporate data. More specifically, 477,000 media contacts, business entity account information, 35,000 user password hashes, assorted documents, and even system administrator credentials (for Google, Twitter, and MongoDB). The total size of the collection reached a terabyte, and the data concerned high-profile clients of iPR Software such as General Electric, Xerox, CenturyLink, Forever21, Dunkin Donuts, Nasdaq, California Courts, and Mercury Public Affairs.
UpGuard researchers discovered the bucket that was named "cms.ipressroom.com" on October 15, 2019, and found out who the owner is on October 24, 2019. When they notified iPR Software via email and phone, the firm confirmed that they were aware of the issue and were already working to secure the database. The only thing that happened in the period that followed was to change the structure of one folder in the data collection. The bucket was secured on November 26, 2019, a full month after the initial notification was sent to them.
Source: UpGuard
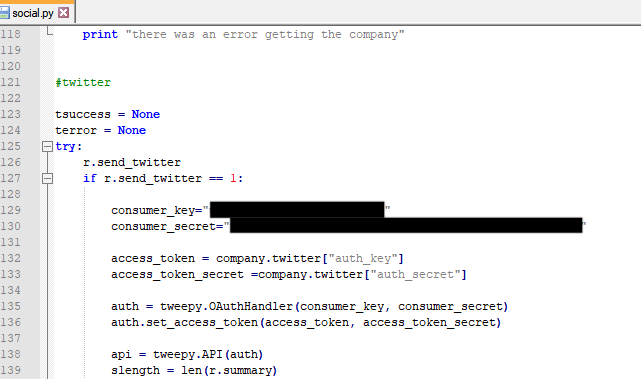
The consequences of the particular exposure are pretty dire, to say the least. Due to the type and amount of data that has been leaked, actors could very easily indulge in website defacing, social media account takeover, impersonation, private messages, scamming, phishing, stuffing, extortion, you name it - and it’s been made possible by this incident. It is important to clarify that not all entries were equally rich, but most of them were very generous. As there were MongoDB backups in the collection too, there are entire sub-collections of emails, full names, usernames, login data, and password hashes in there.
Source: UpGuard
This is yet another case that highlights the dangers of having a single entity manage huge and highly sensitive data belonging to a set of companies. Each of these companies serves many thousands if not millions of people, so a single exposure of this type compromises a large number of users who don’t even possess the knowledge of who’s holding their data. PR and marketing providers are at the epicenter of this problem, as these firms are often called to play the role of the data manager, juggling collections that derive from numerous sources. We have seen this happening again, and again, and it’s always on a large scale. It is crystal clear that we can no longer rely on the accountability of these firms, so a lot more stringent rules need to apply.
Have something to comment on the above? Feel free to share your thoughts with us in the section down below, or join the discussion on our socials, on Facebook and Twitter.