The iOS Pasteboard is Entirely Transparent and Apple Says That’s Ok
- Any app can potentially access information that is stored on the iOS pasteboard without necessarily having the permissions to do so.
- The information can include documents, location data, passwords, IBANs, audio, URLs, and more.
- Apple has received a report on this but responded by saying that there’s nothing wrong with this functionality.
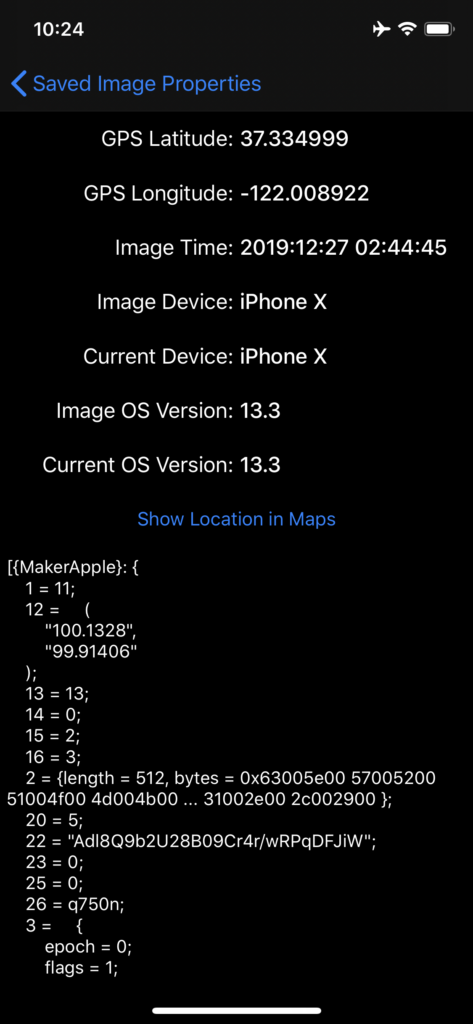
Researchers at Mysk report an alarming issue that concerns the pasteboard used in iOS and iPadOS, which enables one app to copy data that has been saved there by another. Since the pasteboard is system-wide and doesn’t work on any app-level restrictions, the user could have their sensitive data compromised. An example given by Mysk is to take a photograph using the Camera app, which copies it to the pasteboard. When another app is launched, it could potentially access the location information contained in the image metadata that the user captured previously. No user consent is required for this, and in fact, the user will most probably not realize it at all.
Source: Mysk Blog
This problem affects all Apple devices running iOS and iPadOS v13.3, which is the most recent available version. To demonstrate the problem to Apple, Mysk created a simple tool named “KlipboardSpy”, and which can fetch data from the iOS pasteboard without restrictions, just like any other iOS app potentially can. By using this tool, they could infer the following data by merely grabbing it from the pasteboard:
- GPS coordinates
- Photograph timestamp
- Device used for the photograph
- Device used right now
- OS version used during the capturing
- OS version used currently
The purpose of comparing iOS versions and device IDs is to determine the reliability of the location data. Recent images that have been taken by the current device on recent iOS versions can give reliable location data. Otherwise, they may be saved on the pasteboard that comes from other users who sent them over chat apps or downloaded from the internet.
While the researchers focused on figuring out the location of a person in their demonstration, the pasteboard may contain other sensitive data too. Examples include entire files like PDFs and spreadsheets, URLs visited previously, IBANs, emails, contacts, notes, audio files, and even passwords. To make matters worse, Apple has unified the pasteboards of iOS and macOS a couple of years ago, so if the user has enabled the “Universal Clipboard” an iOS app could potentially steal macOS data too.
Weirdly, Apple received Mysk’s notice with the “Klipboard Spy” code included on January 2, 2020. After analyzing the submission, they responded by saying that they see nothing wrong there. Apple doesn’t accept that there’s any privacy risk, as they feel that whatever apps they certify to enter the App Store aren’t engaging in malicious-data grabbing from the pasteboard, and only access info when needed to increase their usability and usefulness. In any way you approach this, iOS is providing users with granular control over data access permissions for each app, but the way the pasteboard works is defeating the purpose of having these settings.