iOS Kernel Zero-Day Vulnerability Exploited in Sophisticated ‘Trigon’ Hack
- A new exploit targeting Apple iOS devices was dubbed Trigon by security researchers.
- It leverages an integer overflow vulnerability in the XNU kernel’s virtual memory subsystem.
- Hackers use a forged parent memory entry to access physical memory mapping and launch an IOSurface spray attack.
The sophisticated Trigon kernel exploit leverages a vulnerability in the XNU kernel’s virtual memory subsystem and has been linked to the "Operation Triangulation" spyware campaign previously uncovered by Kaspersky.
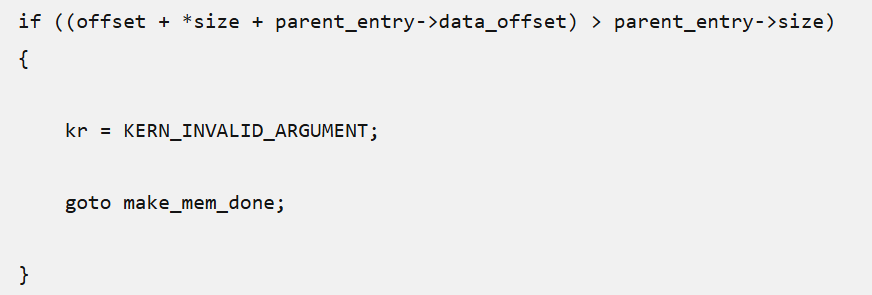
The vulnerability, tracked as CVE-2023-32434, is in the mach_make_memory_entry_64 function of the XNU kernel. The exploit operates in three stages: privileged memory entry forgery, physical memory mapping, and kernel read/write.
Attackers initiate the exploit by crafting a forged parent memory entry in PurpleGfxMem. Hackers gain access to physical memory mapping using an oversized entry of 18,000 petabytes.
Lastly, by launching an IOSurface spray attack, the exploit bypasses Page Validation Hash (PVH) protections, providing attackers with arbitrary kernel read/write access.
Devices powered by A10(X) chips, such as the iPhone 7 and iPad 6th Generation, running iOS 13–16.5.1, are vulnerable. However, newer devices with A12 and A11 processors, featuring hardware-enforced mitigations like Pointer Authentication Codes (PAC) and Configurable TRR (CTRR), remain protected.
Trigon’s deterministic nature presents an unparalleled challenge to Apple’s existing security model, even though Apple patched the vulnerability with iOS 16.5.1.
The exploit, co-developed by Alfie CG, @staturnzz, and @TheRealClarity, has been made open source on GitHub—a move that significantly raises the stakes for iOS users still exposed to this security flaw.
Kaspersky plans to release a comprehensive review of an arm64e-compatible variant of the exploit, hinting at ongoing threat evolution targeting newer Apple systems.
Recently, threat actors impersonating known entities found a way around Apple’s iMessage protection mechanism that automatically disables links from unknown senders by asking users to reply to the phishing text to re-activate the flagged URLs.