Interpol Has Arrested Members of a Nigerian BEC Group
- The Lagos police have arrested three Nigerians in the context of an Interpol operation.
- The men were members of the “TMT” BEC group and had tricked at least 50,000 people.
- The amount of money they made and how exactly they monetized their operations is now a subject of investigation.
The Interpol has worked closely with Group-IB’s threat hunting and intelligence team and managed to trace and take down a Nigerian BEC (Business Email Compromise) group dubbed “TMT.” Three individuals were arrested by the Nigerian Police Force in Lagos as part of the “Falcon” operation.
The TMT group is thought to have compromised approximately 50,000 targets in more than 150 countries from around the globe. In their targeting scope, there were 500,000 entities in the government and private sector, so the number of victims could be much higher.
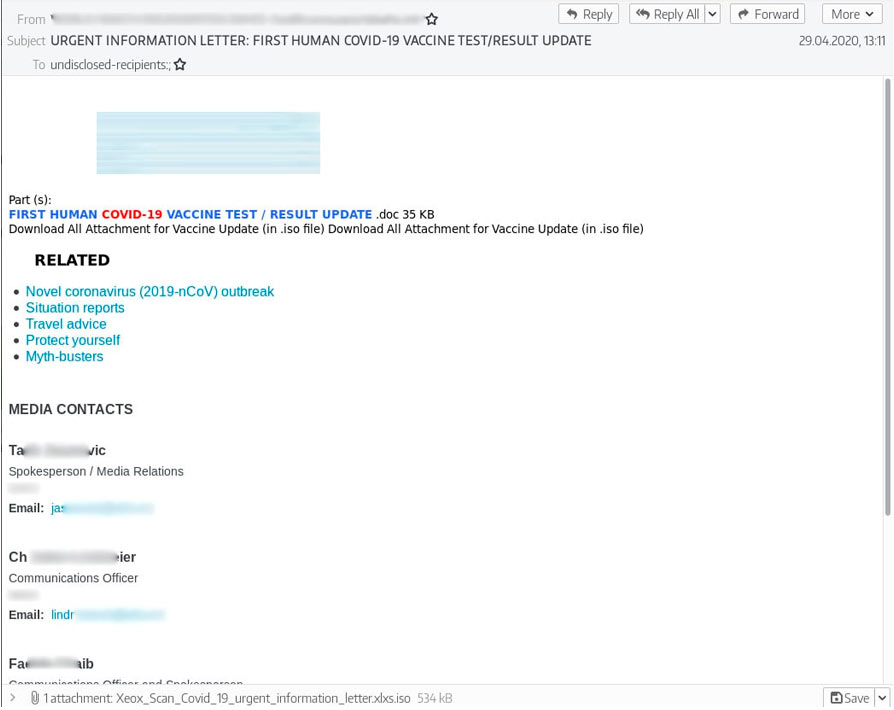
The main method of operation involves phishing campaigns that send out malware strains hiding in macro-laced documents. The actors were impersonating legitimate companies, used COVID-19 themes, or crafted files that appeared relevant to product inquiries or purchasing orders. To send out the massive amount of emails they did, TMT used tools like the Turbo-Mailer, MailChimp, and Gammadyne Mailer.
The threat actors also liked to use compromised email accounts to distribute their phishing emails to more victims, adding legitimacy and upping their success rates. Group-IB has sampled messages written in English, Russian, Spanish, and more, so the scammers maintained a pretty wide scope.
As for the malware that was used, the Nigerian hackers didn’t bother to develop any custom tools - or didn’t have the skills to do it. Instead, they bought malware strains and RATs (Remote Access Trojans) such as AzoRult, AgentTesla, NetWire, and Pony, and then used crypters to obfuscate them well enough to minimize AV detections. These tools helped TMT steal credentials and authentication data from browsers, FTP clients, and email, thus becoming empowered to move their BEC operations further/deeper.
Interpol will now interrogate the arrested individuals to figure out their exact monetization methods, as this aspect remains blurry. Likely, they tricked their victims into diverting payments to different bank accounts under their control. Selling account access on the dark web is also a possibility.
Remember, to avoid getting scammed by BEC actors, call the person who has sent you an email informing you of a sudden bank account or payment method changes. If you have received an email with an attachment, do not under any circumstance enable macros/content to view it. And finally, use an AV solution from a reputable vendor that would scan these files upon reception or download.