Intel Partners With Microsoft to Fight Cryptojacking
- Intel will integrate its Threat Detection Technology (TDT) into Microsoft Defender for Endpoint.
- This will enable the security tool to receive reports about “anomalous” activity and CPU operations.
- Cryptojacking is a booming problem right now, but this collaboration brings stronger defenses against other threats too.
Cryptojacking is a persistent problem that is always on the rise when cryptocurrency values are climbing. We have reported about cryptojacking campaigns numerous times, involving XMRig malware, tools that target Docker, and explosive mixes with RATs, but in general, they’re all doing the same thing. A malware is planted on your system and takes up valuable processing resources to mine cryptocurrency that goes straight into the actor’s pocket.
Defending against this menace isn’t easy, nor always straightforward. For this reason, Microsoft and Intel have announced a new collaboration that is aimed at detecting and stopping cryptojacking.
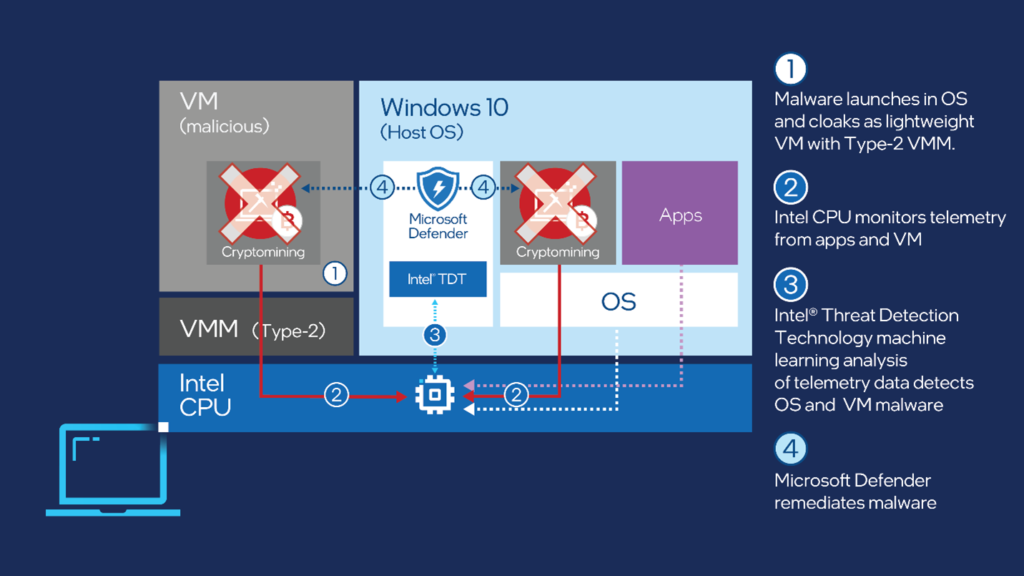
In the context of this collaboration, the Intel Threat Detection Technology (TDT) will be integrated into Microsoft Defender for Endpoint, essentially enhancing its ability to detect cryptojacking malware. Having the two products work in harmony is ideal because Intel’s threat detection tech can deploy machine learning analysis to detect malware that runs either on the OS or the virtual machine level. Then, Microsoft Defender can remediate the malware.
Although this tech specifically targets crypto-miners, it doesn’t mean that it will be limited to this threat alone. Side-channel attacks, credential stealers, banking trojans, and even ransomware attacks will also be detected and remediated, and the more capable Intel’s machine learning gets the more attack vectors will be recognized.
Intel’s TDT identifies threats by detecting anomalous activity, using a combination of CPU telemetry and ML heuristics. Each threat has unique characteristics, so the more widely Intel TDT is deployed, the faster it will grow to become more powerful.
Coin miners, in particular, cause millions in damages because of hogging system resources, and they can spread very fast thanks to their worming capabilities. Defending against this threat effectively means saving a lot of time having to clean entire networks and countless servers and connected devices.
The TDT tech is natively supported by all Intel Core processors and the Intel vPro platform, 6th gen or later, so this collaboration should bring benefit to the vast majority of systems out there.
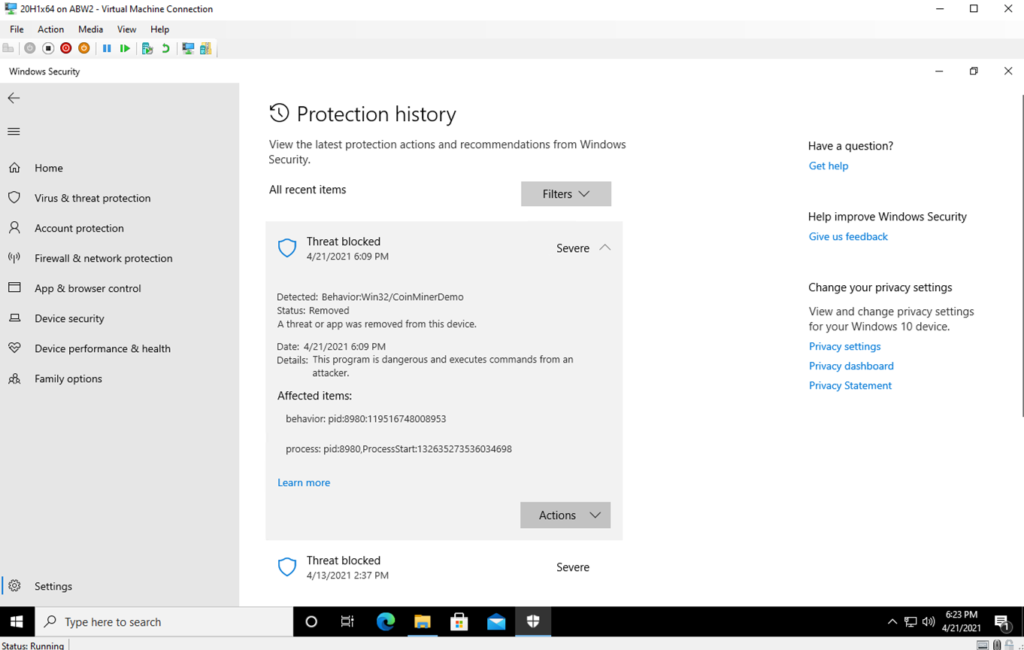
From the end user’s perspective, nothing much changes, really. When a coin-mining malware is detected and blocked, the user will get a security notification, and the incident will be logged on the ‘Protection history’ - where more details may be viewed.