Intel CPUs’ New Flaw Permits Branch Target Injection Attacks Exposing Sensitive Data
- Some high-end Intel CPU generations are vulnerable to branch target injection attacks.
- A new security report reveals these attacks can manipulate the prediction of indirect branches.
- These could precisely redirect sensitive information to a malicious target address.
A vulnerability of the Indirect Branch Predictor (IBP) and the Branch Target Buffer (BTB) in high-end Intel CPUs like Raptor Lake and Alder Lake permits high-precision Branch Target Injection (BTI) attacks, security researchers say. BTIs can breach security in cross-process and cross-privilege scenarios and break Address Space Layout Randomization (ASLR).
BTI attacks exploit the branch prediction hardware in modern CPUs to manage a program's control flow. The predictor handles the target address of indirect branches via a combination of global history and branch address, and the new study uncovers new attack vectors that can bypass defenses and compromise modern CPUs.
The report says the efficient and high-resolution iBranch Locator tool can locate any indirect branch within the IBP by finding the IBP index and then searching for tag aliasing.
An IBP injection attack leveraging the iBranch Locator tool lets the attacker locate any victim IBP entry and inject a multi-target indirect branch. The BTB attack evicts the victim from IBP and injects BTB with a single-target indirect branch, using only iBranch Index Locator as the attacker's indirect branch injects malicious targets into the victim BTB entry and uses a misleading BTB prediction.
The full study examines Intel's hardware defenses, such as IBPB, IBRS, and STIBP, and reveals “previously unknown holes in their coverage.”
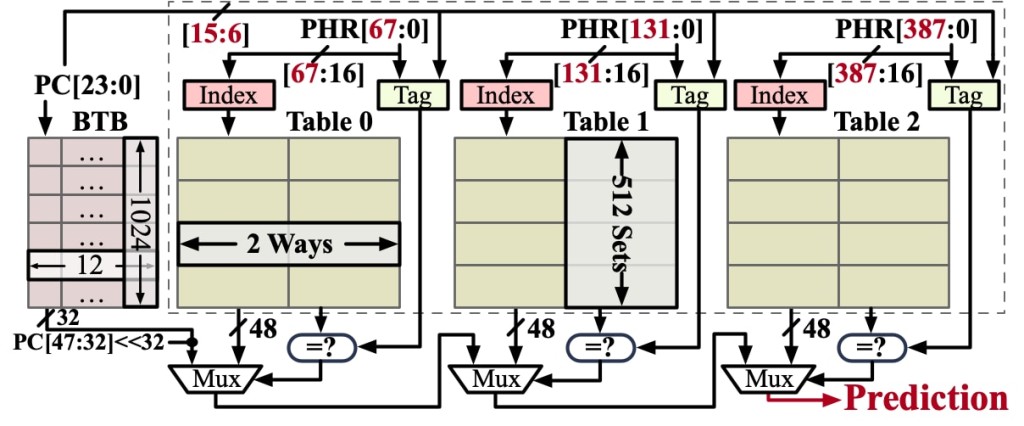
The IBP computes the index and the tag into each table based on the PHR and the branch instruction address via a hashing function crucial for launching precise BTI attacks that was found used by the IBP in modern Intel CPUs. The exploit can manipulate the IBP functions and precisely redirect the control flow of a program to a malicious address.
The report also provides risk mitigation solutions for these attacks, including using IBPB more aggressively and a secure BPU design, but the chip giant says no new mitigations are required to address them.