Fake Sites Distribute Trojans That Install Browser Add-Ons to Steal Private Data
- Hackers distribute malicious Web extensions via fake versions of several download sites.
- Once installed, the add-ons change the compromised Web browser’s default search.
- Unfortunately, the malware cannot be removed, and antivirus solutions do not flag it.
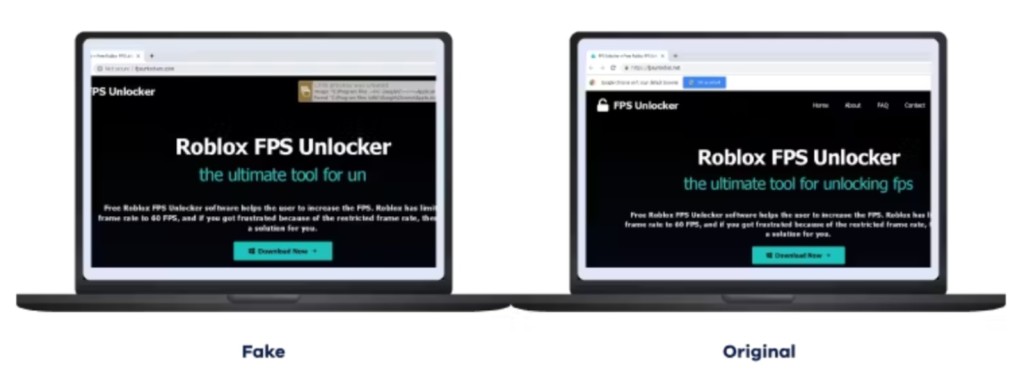
A novel widespread campaign lures victims via fake download sites looking like Roblox FPS Unlocker, YouTube, VLC, or KeePass to distribute Trojans that install malicious web browser extensions to steal sensitive user data, the latest report from ReasonLabs Research Team says.
The Trojan debuted in 2021 on fake download websites with extensions focusing on games and videos, affecting at least 300,000 Google Chrome and Microsoft Edge users. It has different deliverables, including adware extensions that hijack searches and sophisticated malicious scripts that deliver local extensions.
The executable files acquired from the websites impersonating popular brands do not deliver the advertised program, only the malware. However, researchers say that newer versions download legitimate programs from a Google storage link via API.
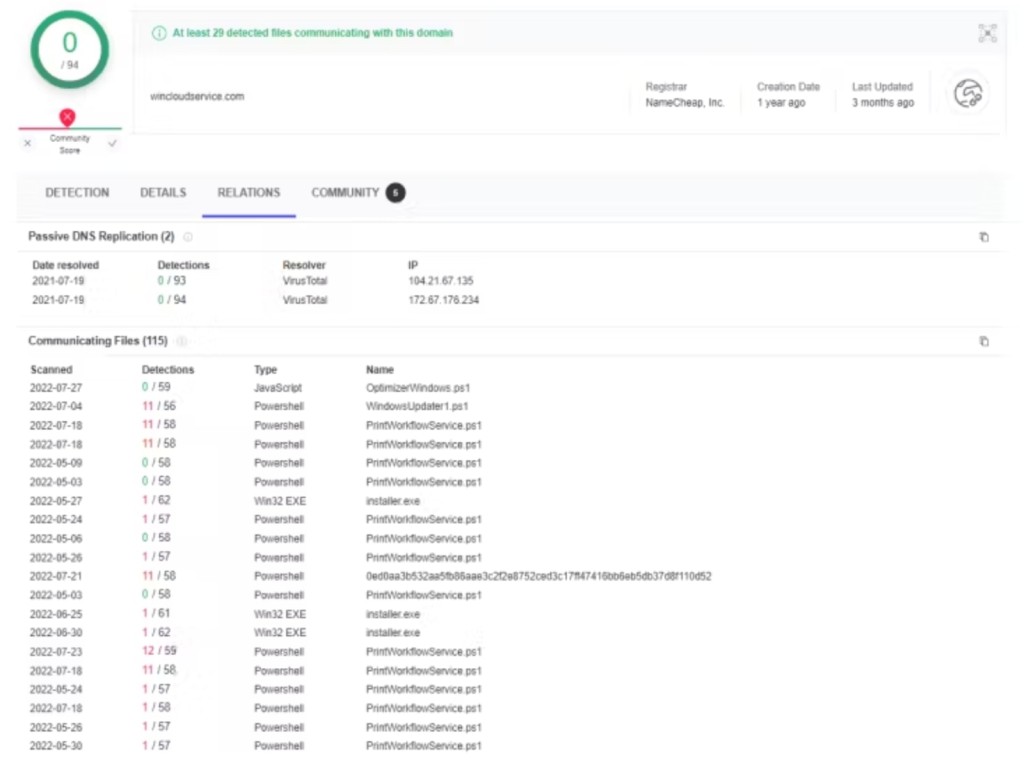
Once the victim runs the malicious program, a PowerShell script written to the system32 folder downloads a payload from a remote server and executes it, triggering a second-stage script.
A third-stage script locates browsers’ DLLs and changes specific bytes to hijack the default search from Bing or Google to the hackers’ search portal. A Chrome and Edge extension that hijacks browser search is installed, as well as a local extension that downloads all of the files from the C2.
The Trojan adds registry values to force the installation of extensions from the store, loads a local extension via tampering with browser “.lnk” files, and alters the Chrome/Edge browser DLL, while newer versions of the script remove browser updates.
The extension steals search queries, redirects them through the hackers’ search, and cannot be disabled by the user. Detecting it is made harder because it does not appear on the “Extensions” page. Even turning on the Developer Mode results in a message saying the user’s organization manages the browser.
Even worse, most antivirus (AV) solutions do not detect the installer or extensions. The security researchers notified Google and Microsoft, which are taking the appropriate measures.
Lately, cybercriminals have been seen distributing malware via tools masquerading as known generative AI assistants spread via misleading ads, phishing sites, and browser extensions, impersonating ChatGPT and Midjourney to steal user data.
Also, ads for crypto giveaways and YouTube videos that appear to be tutorials for popular software distribute various info-stealing malware and eBooks torrents spread ViperSoftX data-stealing malware.