Indian Military Personnel Targeted by ‘PJobRAT’ Spyware Mimicking Dating Apps
- An unknown actor is spreading fake dating apps on military forums, targeting Indian personnel.
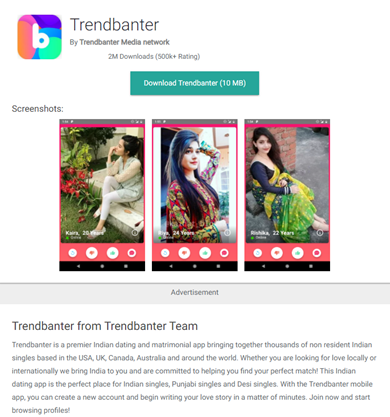
- The apps use the names “Trendbanter,” “HangOn,” “SignalLite,” “Rita,” and “Ponam,” but they’re all the same spyware.
- The functions of PJobRAT include stealing images and video, SMS, contact lists, documents, GPS data, and more.
Researchers at the 360 Core Security Lab have sampled a recent version of the PJobRAT, a spyware that has been around since at least December 2019. In its newest iterations, it appears to be disguised as an Indian dating and instant messaging app under the name “Trendbanter.” In other cases, the actors imitate “HangOn,” “SignalLite,” “Rita,” and “Ponam.” According to the researchers, the current campaign, which targets mainly Indian military personnel, has been active since January 2021, so it’s been several months already.
The spyware is being distributed via third-party app stores and not the Play Store, and it’s promoted as a platform meant to bring single Indians living abroad together. The weird stuff starts immediately after its installation, as the icon displayed on the device rarely matches the one shown in the app store. Instead, it mimics WhatsApp or something else, trying to hide in the apps list.
Function-wise, PJobRAT exfiltrates documents of the pdf, doc, docx, xls, xlsx, ppt, and pptx types, and can also obtain private data from apps like WhatsApp, including conversation messages and contact lists.
Here is the complete list of the spyware’s functions:
- Upload address book
- Upload SMS
- Upload audio files
- Upload video file
- Upload image file
- Upload a list of installed apps
- Upload a list of external storage files
- Upload WIFI
- Upload geographic location
- Update phone number
- Recording via the mic or camera
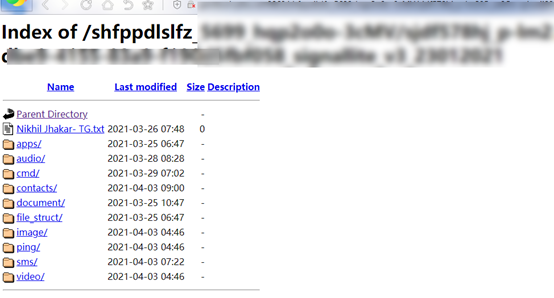
No matter what app name and icon is used, the spyware remains the same in terms of its code and also communicates with the same infrastructure. Interestingly, the researchers found that the private server which receives the exfiltrated data is publicly accessible, which is a clear indication of the carelessness of the actors.
The 360 Core Security team cannot attribute this campaign to anyone with certainty. Still, considering that the actor's goal appears to be spying on Indian military personnel, the actors could be Chinese or Pakistani hackers.
Hooking army personnel through dating and IM apps is not unusual at all, as it seems to be working very well in this context. Back in February 2020, we saw Hamas hackers deploying the same trick against Israeli soldiers, convincing them to voluntarily download powerful spyware on their phones - which then accessed camera, GPS, SMS data, browser history, and even calendar entries.