An Indian IT Firm Was Spying on Politicians From Around the Globe
- A small team of Indian hackers was selling “phishy” cyber-intelligence services to their clients.
- The targets of the group include journalists, activists, politicians, and high-ranking employees.
- The US DOJ is already preparing a case against the firm, who unlawfully took over email accounts and accessed corporate networks.
A small and mostly unknown Indian IT firm named “BellTroX InfoTech Services” has engaged in a large-scale spying operation that targeted government officials and other high-ranking individuals from around the world. The New Delhi-based company managed to spy on 10,000 email accounts over the last seven years. According to a Reuters report, the Indian hackers compromised investors in the United States, politicians in Europe, gambling tycoons in the Bahamas, employees of “KKR” and “Muddy Waters,” and many more.
The US Department of Justice is already preparing a case against Sumit Gupta, the owner of “BellTrox InfoTech Services,” but nothing has been unsealed yet. Reuters claims information that involves clients, so the hacking and spying were done on account of others. The team of people working for “BellTrox” appears to be the same as the one that a Citizen Lab report names as the “Dark Basin”. The company is apparently maintaining a website and a LinkedIn page where they promote email penetration, exploitation, corporate espionage, and “phone pinger” services. Some of those who had the audacity to endorse them on Linkedin are users who claim to be former FBI agents and official government investigators from the US and Canada. Of course, private investigators are also openly buying these services.
Sumit Gupta, Source: Reuters, Credits: Alasdair Pal
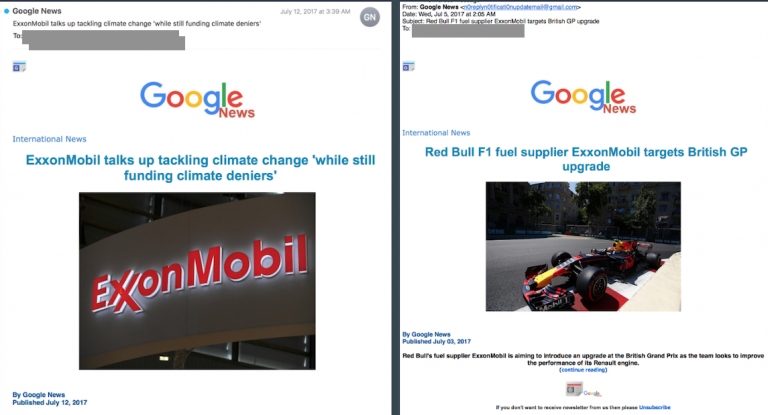
As for the targets, these include journalists, senior government officials, political candidates, bankers, high-ranking employees working in pharmaceutical companies, and various advocacy organizations dealing with climate change and net neutrality. Reuters looked into a cache of data shared by their anonymous sources, and it seems that the main method of compromise was to bombard the targets with phishing emails imitating friends, relatives, or colleagues. In some cases, the firm used fake Facebook login requests, or messages that would supposedly confirm an unsubscription from porn or horoscope websites. The hacking team was trying all possible ways, and in most cases, they achieved their goal. In a matter of targeting a climate change awareness campaigner, they even sent fake Google News.
Source: Citizen Lab
In some cases, the Indian hackers got to learn these useful details about their targets from their clients. In other instances, they conducted their investigation or even went through the trouble of compromising someone close to the potential victim in order to increase their chances of success. Once they stole credentials through phishing, they used VPN tools to access these accounts and then moved deeper or laterally. If you are interested or personally concerned, CitizenLab has uploaded a list with the indicators of compromise by the BellTrox team on GitHub.