Indian Bank Users Targeted with Malicious WhatsApp APKs to Steal Sensitive Data
- The Aadhaar, PAN, and ATM and payment card PINs are targeted by hackers via a sophisticated malware campaign.
- SMS permissions granted by Android users in India are exploited for intercepting one-time passwords
- This malware family has unique methods to exfiltrate SMS-based credentials: SMS forwarding and Firebase-exfiltration.
A newly identified cybersecurity threat, named “FatBoyPanel”, is targeting users of multiple Indian banks in a sophisticated malware campaign aiming to steal sensitive financial and personal data.
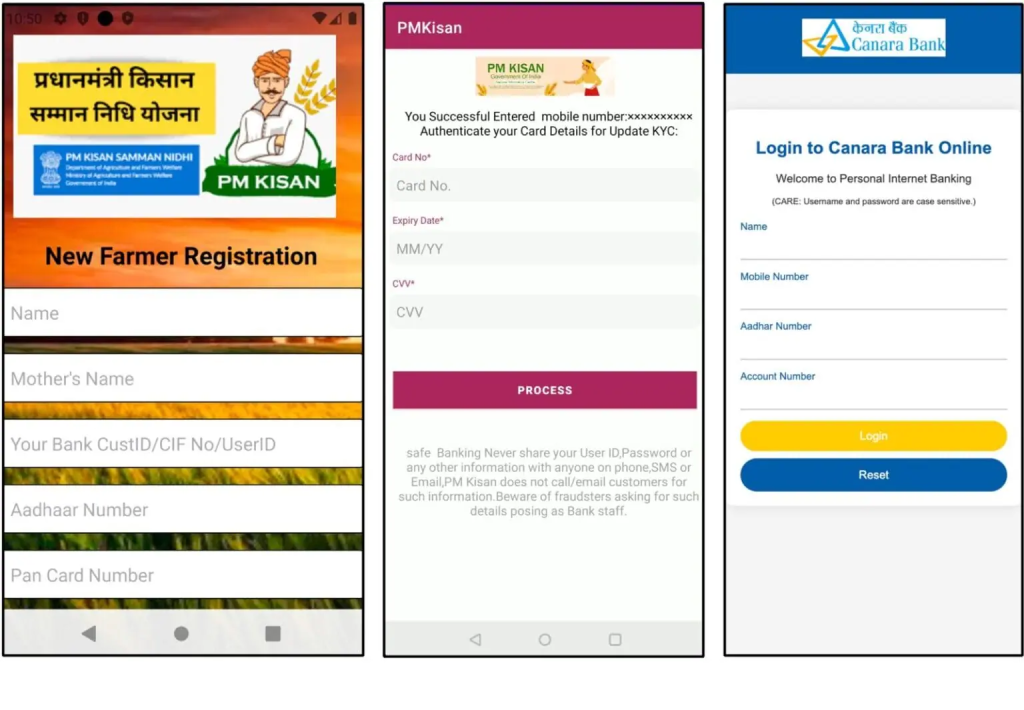
The campaign comprises approximately 900 distinct malware samples. These malicious programs are designed to exploit unsuspecting Android users, extracting data such as Aadhaar numbers, PAN cards, ATM PINs, and credit card details.
The malware campaign uses WhatsApp to distribute APK files disguised as legitimate government or banking applications. Once installed, these malicious apps mimic the user interface of actual banking applications, deceiving victims into entering sensitive credentials.
Researchers from cybersecurity firm Zimperium have identified that the malware exploits SMS permissions granted by users, enabling it to intercept critical information, including one-time passwords (OTPs).
With OTP access secured, attackers can facilitate unauthorized financial transactions, compromising victims’ bank accounts and digital wallets.
The FatBoyPanel malware family comprises three distinct variants, each employing unique methods to exfiltrate SMS-based credentials: SMS forwarding, Firebase exfiltration, and a combination of both strategies.
This variant captures SMS messages, including OTPs, and forwards them to an attacker-controlled phone number. The other approach exfiltrates messages to a Firebase endpoint, a cloud-based backend acting as a command-and-control (C&C) server.
The malware's key strength lies in its ability to exploit SMS permissions for intercepting and exfiltrating critical information. For instance, in the Hybrid variant, SMS messages are double-exfiltrated via phone numbers and Firebase endpoints, ensuring robust data capture even if one channel is disrupted.
This malware relies on sophisticated C&C servers to orchestrate its attacks.
Malicious WhatsApp campaigns have been hackers’ favorites in the past months, and Meta’s app has even enabled cybercriminals due to a flaw that did not warn users when downloading dangerous files.