Indian APT Targets Maritime Entities in the Indian Ocean and Mediterranean Sea with Malware
- A tracked APT was seen targeting various ports and maritime facilities in the Mediterranean and Indian waters.
- The India-aligned group known as SideWinder, Rattlesnake, and Razor Tiger abused a few known Microsoft Office flaws.
- The spear-phishing attack involved malicious documents appearing to come from organizations known to the intended targets.
An Indian nation-state APT group (advanced persistent threat) sent malware-ridden documents via a spear-phishing campaign with updated infrastructure and new tactics and techniques toward ports and maritime facilities in the Indian Ocean and Mediterranean Sea, as per the latest report by Blackberry. The actors exploited a few known Microsoft Office vulnerabilities.
Tracked as SideWinder, Rattlesnake, and Razor Tiger, the espionage and intelligence gathering APT gang launched new cyberattacks on various maritime entities in Pakistan, Egypt, and Sri Lanka but also targeted Bangladesh, Myanmar, Nepal, and the Maldives.
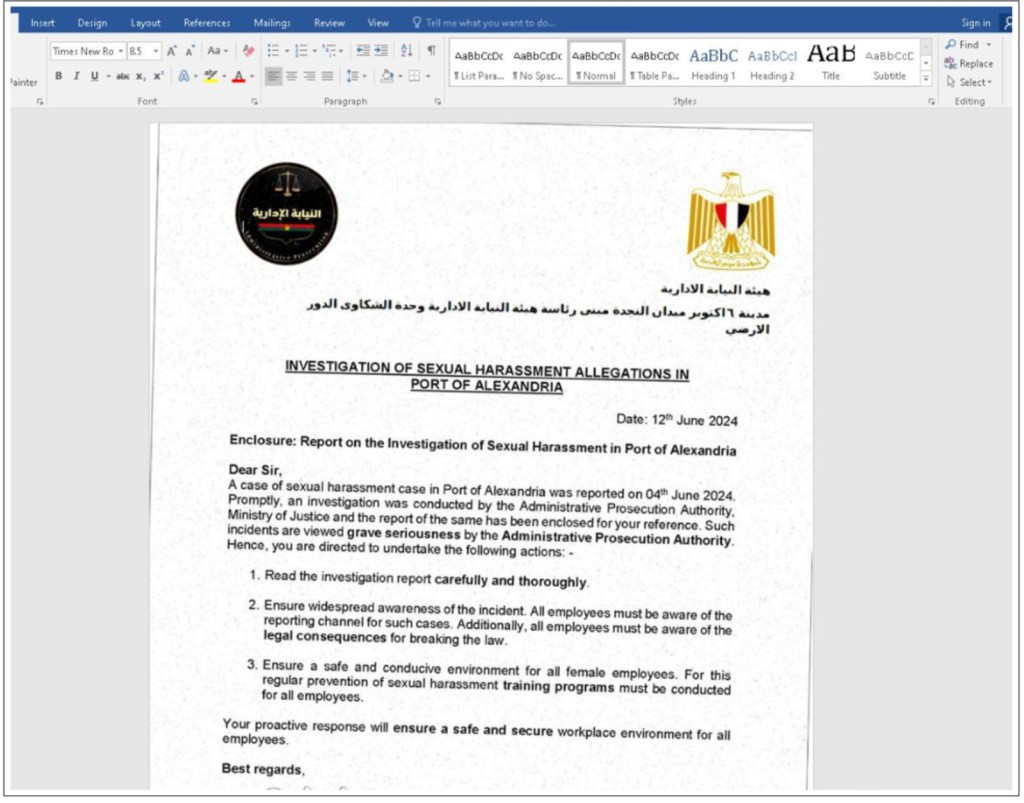
The attackers sent spear-phishing emails using three visual decoys that lured the victims with titles that aimed to incite fear and anxiety, increase the sense of urgency, and divert the recipient’s attention from the scam.
The emails contained malicious documents, crafted to trick the intended targets into believing these were legitimate files coming from known organizations, such as the Mediterranean Sea Port of Alexandria and the Red Sea Port Authority.
A widely exploited remote code execution (RCE) vulnerability (CVE-2017-0199) in Microsoft Office was exploited, which allows an attacker to control a compromised system and its data, install programs, or create new privileged user accounts.
The document contained a plain text URL directing to an attacker-controlled site. Then, a rich text format (RTF) file fetched a document, abusing another known flaw in Office (CVE-2017-11882) to execute a shellcode that decrypts and runs JavaScript code.
The stage two command-and-control (C2) utilizes an old Tor (The Onion Router) node for obfuscating network analysis.
The APT has been active since at least 2012 and focuses on government, military, and businesses in Pakistan, Afghanistan, China, and Nepal, for cyberespionage.
This month, the Chinese APT17 cybercriminal group targeted companies and government entities in Italy with its 9002 RAT, employing malicious URLs to download a custom Skype for Business MSI package that harbored malware.
Also, spear phishing campaigns targeted institutions in Ukraine with HATVIBE and CHERRYSPY malware via a compromised employee email, using a Microsoft Word attachment with a malicious macro as a lure, which looked like a copy of a legitimate previously sent document.