HP Touchpoint Analytics Client Vulnerable to Privilege Escalation Attacks
- HP’s hardware performance monitoring tool is vulnerable to severe remote execution attacks.
- The tool runs on high system privileges but doesn’t follow a proper DLL validation process.
- HP has released a fixing patch, so you should install it immediately if you’re using Touchpoint.
HP Touchpoint Analytics is a service that collects diagnostic information about hardware performance, and which HP has been offering as part of their “Support Assistant” since 2014. According to a report by Peleg Hadar, a security researcher working for SafeBreach, HP Touchpoint Analytics is vulnerable to privilege escalation and persistence (CVE-2019-6333), based on the loading of an arbitrary unsigned DLL into a service that runs as SYSTEM. If that rings a bell to you, it is because that’s the same type of vulnerability that we discussed in relation to BitDefender, and also to Trend Micro Password Manager back in August.
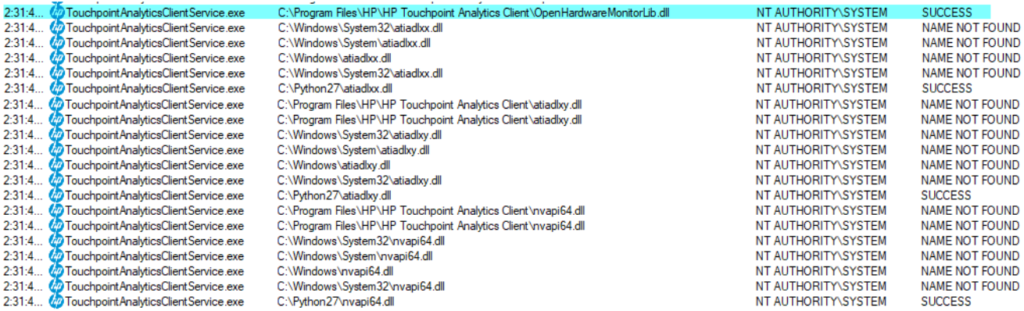
If you own an HP PC or laptop, the chances are that it comes with HP Touchpoint Analytics pre-installed. The service is executed as “NT AUTHORITY/SYSTEM”, which gives it very powerful user permissions. That is because the particular tools need to access low-level hardware such as physical memory, SMBios, MSRs, and monitor the performance. SafeBreach researchers have found a way to hijack the DLL that the software is trying to load (openhardwaremonitorlib.dll) by replacing it with an unsigned DLL file. This requires the modification of the system’s path variable to include the new directory of the ACLs, as well as the changing of the setting that won’t allow access to non-admin user accounts.
Source: SafeBreach
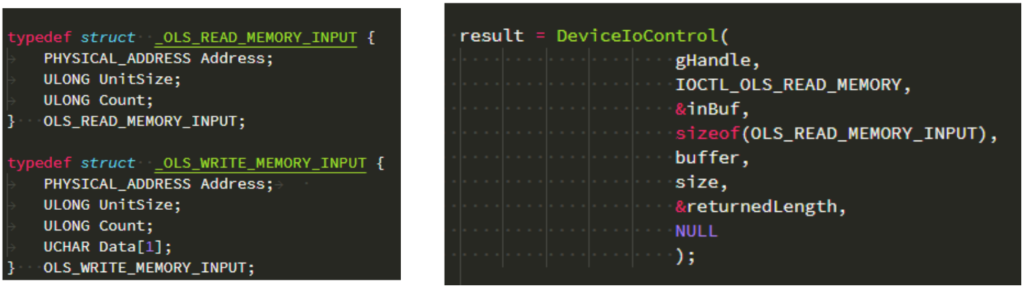
The proof of concept code that was developed by SafeBreach enables an attacker to read the contents of the physical memory of the target device, and this is only one example of how this vulnerability could be exploited. Others involve driver signature enforcement bypass, which gives an attacker system control via a kernel driver module or signed execution and whitelisting bypass, which enables an attacker to bypass signature or app validation lists. This latter can open the door to remote code execution and detection avoidance.
Source: SafeBreach
The versions of the HP Touchpoint Analytics that are vulnerable to CVE-2019-6333 are all versions below 4.1.4.2827. The researchers reported the discovered flaw back on July 4, 2019, and HP responded a week after that. On August 7, 2019, HP deployed a patch to the customers, and on October 4, 2019, they published a security advisory. What this means is that if you haven’t updated your Touchpoint Analytics client already, you should do so immediately. As we said before, there will be more revelations of this type concerning other companies and products, so stay tuned and be among the first to know.
Have something to comment on the above? Feel free to do just that in the section down below, or on our socials, on Facebook and Twitter.