How “UltraRank” Monetized Credit Card Data Through “ValidCC”
- "UltraRank" differentiated itself from the typical Magecart monetization models by launching a card shop.
- The actors actively protected their platform and its reputation, making thousands of USD each day.
- In total, it is thought that UltraRank managed to compromise almost seven hundred websites.
Over five years, the group of Magecart actors known as "UltraRank" has managed to compromise 691 websites, 13 third-party suppliers from across the globe, design an intricate monetizing model through the "ValidCC" shop, and make between $5,000 and $7,000 per day. Group IB has been following the operations of the particular Magecart group, and they report on their unique affiliated card shop business model.
Typically, hackers who steal credit card data buy stuff from online shops and then resell it, or they just sell the details to other carders who undertake the exploitation process. UltraRank did neither. Instead, they sold the data via "ValidCC," a card shop that sits on the same infrastructure that the group's C2 relied upon. Because these cards are sold exclusively there, they are "fresh" and valid, so the shop built a reputation for itself.
Source: Group IB
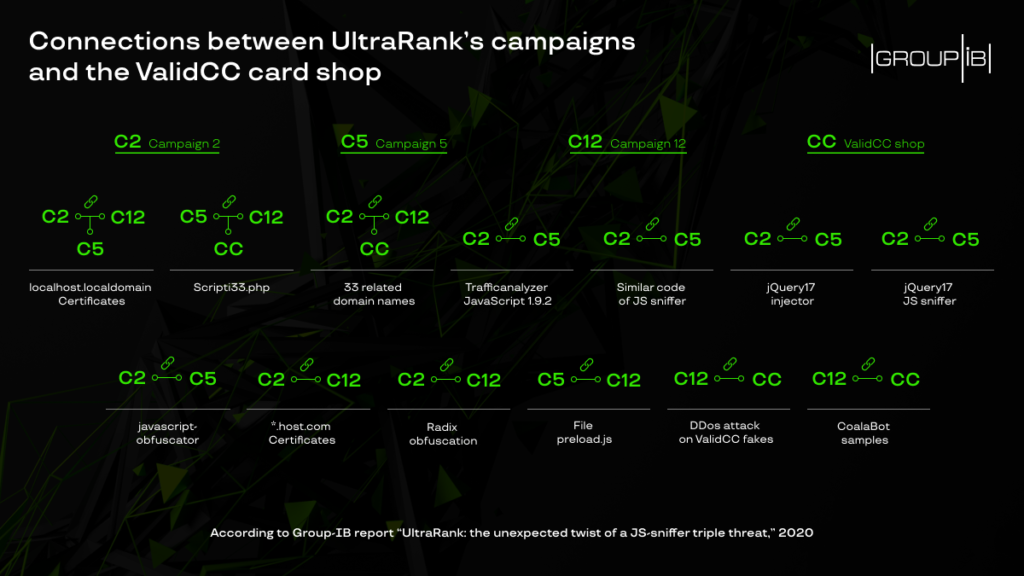
According to what the shop's official representative ("SPR") has written in Russian-speaking dark web forums, the cards were collected through the deployment of JavaScript sniffers. While Group IB didn't immediately make the connection between the different sniffers they noticed on various websites, they soon figured it out by looking at the server details and the domain registration patterns.
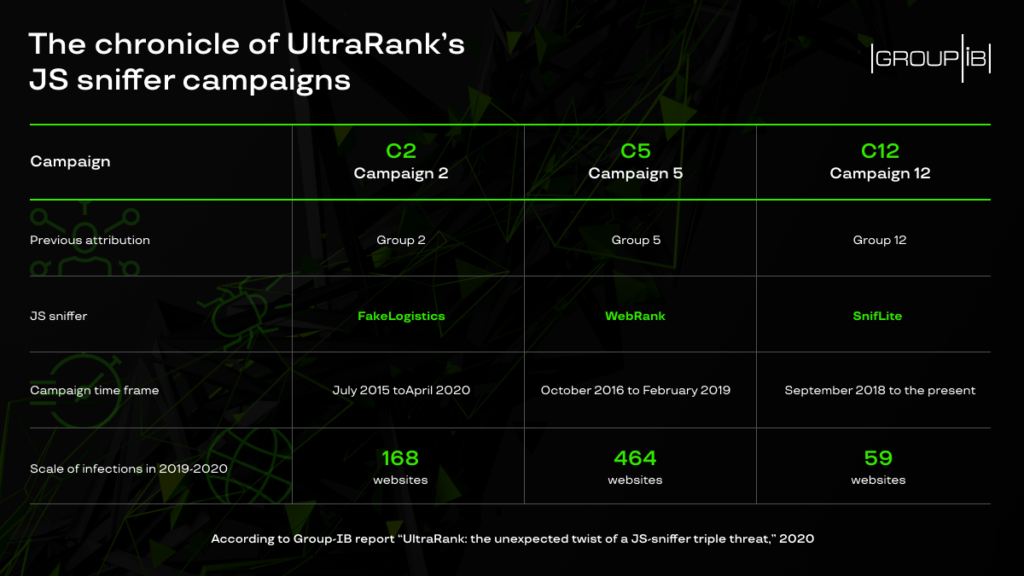
The following image shows which sniffer was used each time, with the most deployed one being "WebRank," which compromised 464 websites.
Source: Group IB
"UltraRank" didn't hesitate to infect a website if they stumbled upon one that had been already compromised by another Magecart group. Moreover, when the group noticed that someone set up a fake "ValidCC" website for phishing purposes, they bought DDoS services and launched attacks against it. This is how much UltraRank cared for the reputation of ValidCC, and they went to great extents to protect it.
As Group IB's Threat Intelligence analyst Victor Okorokov comments, JavaScript sniffers remain a huge problem because webshop admins are simply not paying attention to their platforms' cybersecurity aspect. They still use outdated content management systems that are plagued by numerous vulnerabilities, and they don't bother scrutinizing their code.
Moreover, they rarely visit their inbox to read any user reports about the existence of JS sniffers on the site, and they generally leave these online shops on "auto" (money-making) mode. Magecart actors love this approach and take advantage of the overall negligence.