Historic Malware Proxy Network ‘VIP72’ Goes Offline Without Notice
- The 15-year-old proxy service ‘VIP72’ has remained offline for two weeks now and isn’t showing signs of life.
- The service has gone through a period of scaling down in the previous months, and now it’s gone.
- Some users report being able to still use their nodes, and others got scammed by cloning actors.
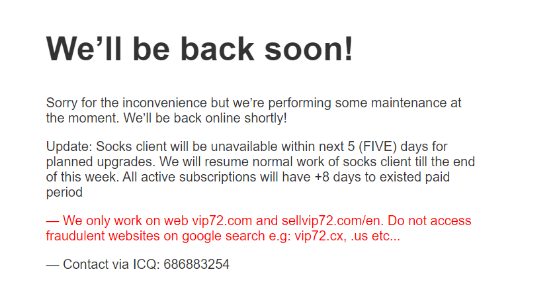
The dark web has been filled with messages of “R.I.P” for VIP72 during the last couple of days, as the 15-year-old malware proxy network has gone offline without notice for two weeks already and isn’t showing any signs of returning online despite some confusing messages that talked about planned upgrades. These were supposed to take five days to complete, but this mark has long passed without an update on the matter.
Already, fraudulent clones have appeared trying to take advantage of the situation as those who were replying upon VIP72 for their malware operations are already looking elsewhere. Some report that the software is still working for them, but others are advising them to abandon ship as they could be entrapped in a law-enforcement honeypot now.
VIP72 was established all the way back in 2006, offering malware campaigners anonymity through a reliable proxying service that obscured their true location. The service was basically using compromised computers that route customer traffic through them, so through a large number of network bounces and relays, the location and identity of the malicious actor’s infrastructure were essentially hidden from the law enforcement authorities.
Recently, VIP72’s powerful DNS leaks checker, “Check2IP,” went offline, so people started assuming that something was going on. Now, with the main proxying serving going down too, it is clear that something serious has happened. The registry expiry is good for another year, so this could be a case of law enforcement. VIP72 was a U.S.-hosted service, something pretty unusual these days, so it’s not unlikely that the FBI has got them finally.
Another scenario laid out by Brian Krebs is that VIP72 has given up against the rising competition from more sophisticated proxy services that emerged recently. As the investigative journalist explains, VIP72 always had a large number of compromised systems available for rent, and in recent months, that number shrunk to about 5% of the typical levels. That was a clear sign of something not working right in the “break-in” process or the operators gradually giving up.
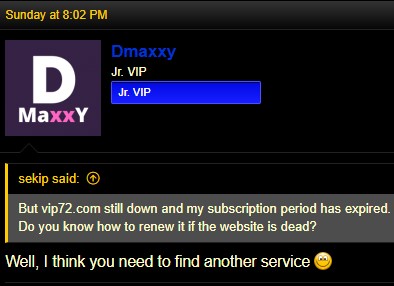
The fact that some VIP72 users still enjoy the service can be attributed to compromised hosts still being infected with the proxy malware, so these may go on indefinitely, but it doesn’t mean that VIP72 is still alive. Finally, many people report being scammed upon trying to renew their expired subscriptions on the service, heading to a new domain to do it.