Highly Dangerous sLoad 2.0 (Starsloard) Malware Discovered & Reported by Microsoft
- The newly discovered malware breed uses highly sophisticated methods of infecting Windows PC while avoiding detection.
- Called sLoad, this malware is capable of talking to C&C servers, collecting information from the infected systems, and downloading additional payloads.
- Microsoft’s Defender ATP Research Team is investigating sLoad and reporting about new versions as soon as they appear online.
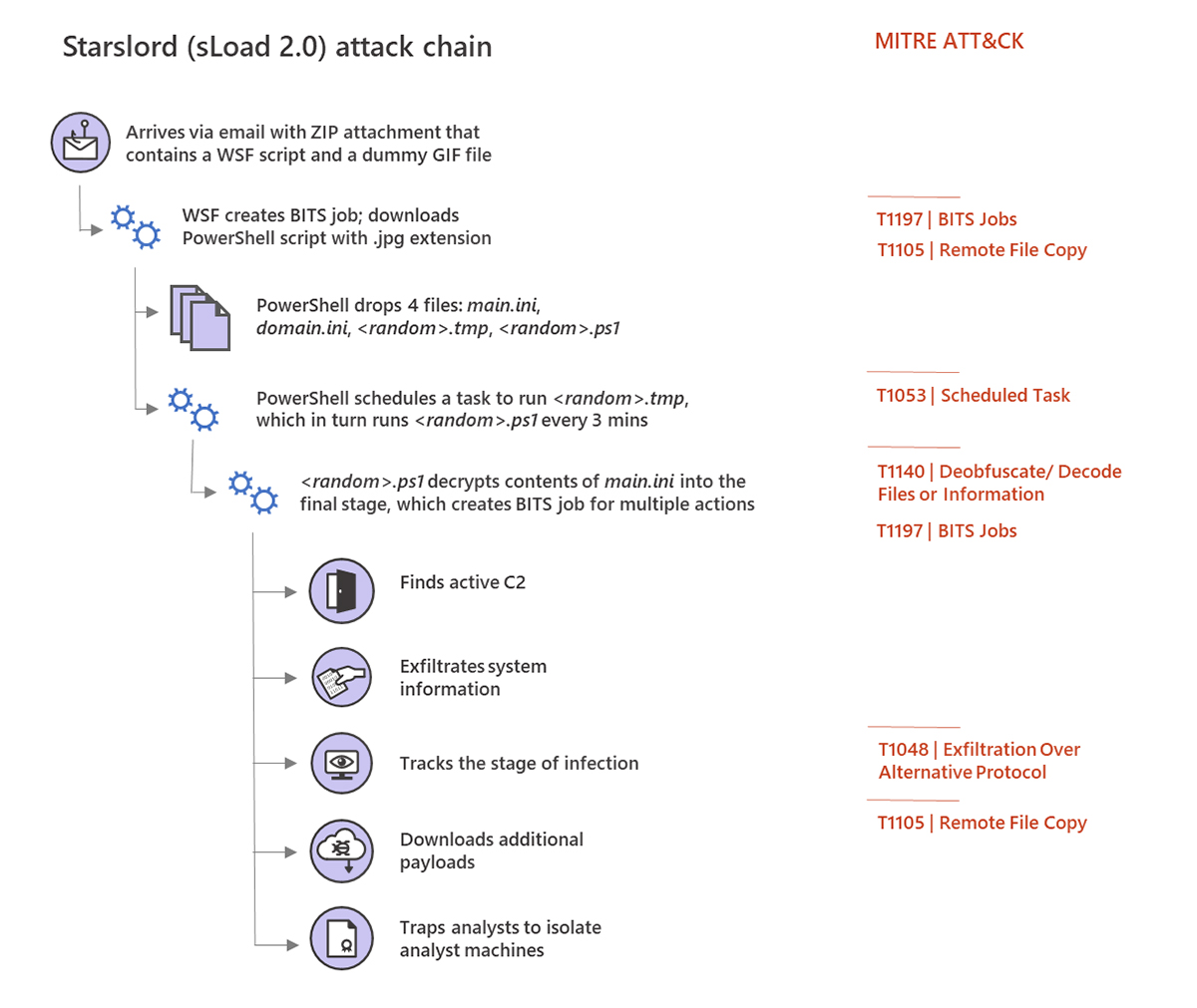
Last month, Microsoft published a detailed report about sLoad, notifying the rest of the cybersecurity community about the hazardous effects of this breed of malware. As could have been expected, this action has forced the creators of sLoad to evolve the malware in a rapid manner, giving us an indication of how malware can quickly evolve and adopt new technologies these days. All of this is explained in Microsoft’s freshly published report, detailing sLoad 2.0 and its capabilities.
In its essence, sLoad acts as a delivery system for more comprehensive types of malware. More precisely, aside from infecting Windows PCs, it’s capable of collecting information about the infected systems and sending that information back to command-and-control (C&C) servers. This is when the creators of the malware can instruct sLoad to download and install a second malware payload – which happens as a background process, without the user even being aware of what’s happening. As such, sLoad can be paired with different types of malware, where the most recent report includes the Retefe banking Trojan.
What’s interesting about sLoad is that it relies on the Windows BITS (Background Intelligent Transfer Service) for malicious activities. This system is primarily used by the Windows Update service, which can identify your network connection usage patterns. Differently said, Windows Update can see when you’re not actively using your network connection to download Windows updates, without disrupting your workflow. Of course, Windows’ BITS service can also be used by third parties as well.
As explained in Microsoft’s report, sLoad automatically creates BITS scheduled tasks that are executed at regular intervals. This means that sLoad talks to the command-and-control server, and then sends data back to the server and downloads new files as well. Interestingly enough, the original sLoad malware was capable of taking screenshots as well, which is a feature not found in the second version.
In addition to using the BITS service, sLoad also heavily relies on the PowerShell scripting language. It runs completely in the RAM, without storing any files on disk. This makes it very challenging for anti-malware solutions to identify the problem.
Image Courtesy of Microsoft.
The second version of sLoad still uses Windows’ BITS service and relies on PowerShell. It didn’t change its primary purpose – but it made core changes that further evolve the malware. It now uses WSF instead of VB scripts during the infection process, and it also checks whether malware analysts are looking at the code. And finally, sLoad 2.0 comes with a system that tracks the stages of an infection (which can be used for debugging or organizing sLoad hosts into sub-groups).
One thing is sure – sLoad 2.0 is a highly sophisticated malware breed, which has the potential to create a long-lasting impact. However, the good news is that Microsoft is keeping its eye on this malware breed, which gives us hope that other vendors will be quick to implement this knowledge as well.