Hidden Text Salting Phishing Techniques Saw a Surge in the Past Months
- Security researchers saw an increase in cybercriminals poisoning the HTML source of an email.
- Hackers embed non-visible elements within the source code of emails that pretend to be from legitimate brands.
- Hidden text salting has been utilized to mislead language detection systems or bypass detection engines.
A significant rise has been observed in the use of hidden text salting, also referred to as "poisoning," in email-based threats during the second half of 2024. Threat actors employ this approach in brand impersonation, language detection manipulation, and HTML smuggling.
Among the brands threat actors impersonate are Norton LifeLock, Wells Fargo, and Harbor Freight.
This technique is being increasingly used by cybercriminals to bypass detection mechanisms, confuse spam filters, and evade email parsers, posing a considerable threat to organizations relying on traditional defenses, a Cisco Talos cybersecurity research division report said.
Hidden text salting leverages the features of Hypertext Markup Language (HTML) and Cascading Style Sheets (CSS) to embed non-visible elements within the source code of emails.
These inserted elements are deliberately hidden from the recipient when the email is rendered by their email client. However, these elements can disrupt email parsers and security frameworks, enabling malicious emails to evade identification.
Such techniques include adding HTML comments, irrelevant content, invisible elements, or characters like Zero-Width Space (ZWSP) and Zero-Width Non-Joiner (ZWNJ). These additions appear gibberish or entirely hidden within the email source code but are comprehensible to parsers, undermining their accuracy.
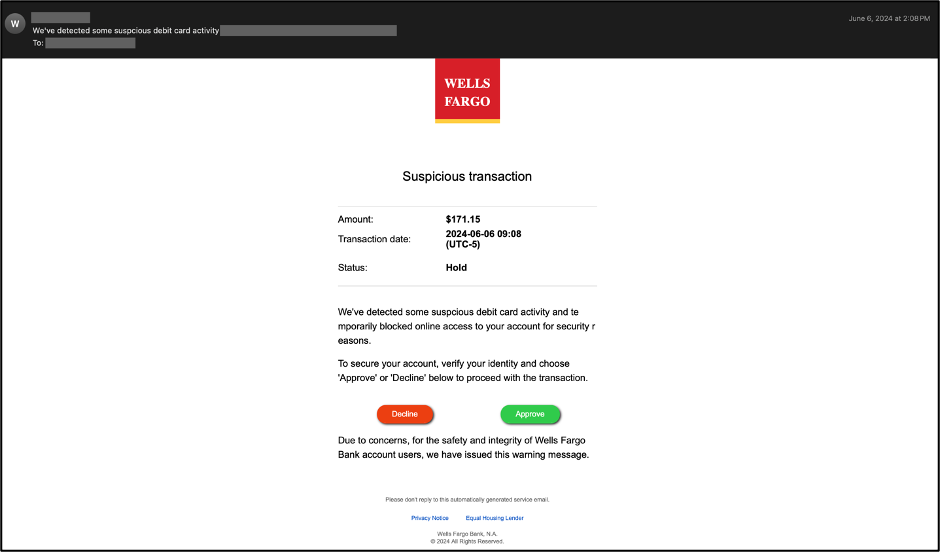
One phishing email disguised itself as coming from Wells Fargo. The attackers used CSS attributes such as "display:inline-block" and "overflow:hidden" to hide malicious content, ensuring it was invisible to the recipient but readable to parsers.
Similarly, in another phishing attempt, threat actors impersonated Norton LifeLock by embedding invisible characters, such as ZWSP and ZWNJ, between the letters of the brand name. While undetectable to the human eye, these characters disrupted parser functionality, helping the phishing email bypass spam and keyword detection.
Hidden text salting has also been utilized to mislead language detection systems. For example, in a phishing email mimicking the Harbor Freight brand, attackers included hidden French language text within the HTML source.
This caused Microsoft's Exchange Online Protection (EOP) to misclassify the email language as French despite the visible text being in English. The technique deceives anti-spam systems that rely on language-based filtering.
Talos has further identified hidden text salting used in conjunction with HTML smuggling to bypass detection engines. Attackers inserted numerous irrelevant comments and spaces between base64-encoded characters within HTML attachments.
This rendered the task of reassembling and decoding the content challenging for file attachment parsers, masking malicious payloads.
Tools relying on automated keyword detection, brand name recognition, or standard language identification struggle to counteract this evolving technique. Experts warn that hidden text salting is not only a current concern but is likely to evolve into even more sophisticated forms.