‘Head Mare’ and ‘Twelve’ Hacktivists Allegedly Collaborate in Targeted Russian Attacks
- Two hacktivist groups may be working together as researchers discover overlapping methodologies.
- Security specialists believe the groups coordinate their attacks, but the exact nature of the collaboration remains unclear.
- Tools, tactics, techniques, and command-and-control infrastructure are shared.
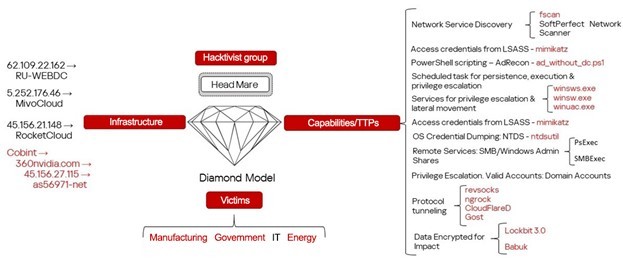
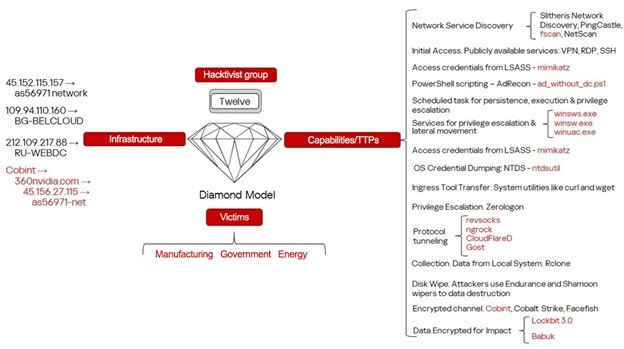
Hacktivist groups Head Mare and Twelve are believed to collaborate, as both entities carry out targeted cyberattacks on Russian organizations. The groups share tools, tactics, techniques, and even command-and-control (C2) infrastructure, suggesting coordinated campaigns.
The report by Kaspersky researchers highlights that Head Mare’s recent attacks leveraged tools previously linked exclusively to Twelve, such as the CobInt backdoor, alongside Head Mare's proprietary PhantomJitter malware.
Researchers note overlap in their methodologies, including the use of trusted relationships to breach networks, credential-collection tools like Mimikatz, and deployment of advanced persistence tactics through compromised contractors.
One prominent finding was the exploitation of unpatched vulnerabilities, including CVE-2023-38831 in WinRAR and CVE-2021-26855 in ProxyLogon, underscoring the attackers' strategic focus on leveraging outdated or unmaintained systems.
The attacks showcase an expanded and evolving arsenal of techniques, from remote access facilitated by tunneling tools like Gost and ‘Cloudflared,’ which tunnels traffic through the Cloudflare network, to lateral movement using standard Windows services.
They’ve reportedly renamed files, cleared event logs, and utilized PowerShell scripts to evade cybersecurity defenses.
Furthermore, both groups employed LockBit 3.0 and Babuk encryptor variants on compromised systems, marking consistent objectives between the two entities.
Kaspersky's research uncovered repeated use of overlapping C2 domains and IP addresses, with infrastructure such as 360nvidia[.]com appearing in campaigns attributed to both groups. PowerShell scripts, file paths, and service names used also point to shared frameworks.
Industries targeted include government, energy, and manufacturing sectors, with attackers pursuing data exfiltration, followed by encryption as their final goal.
Tools like Rclone–an open-source project for copying and synchronizing files between storages of different types–were deployed to siphon sensitive documents.