Hacking Group “Molerats” Targets the Governments of Six Countries
- The Gaza Strip hackers are engaging in a large-scale campaign with unclear motives.
- The actors are sending phishing emails that attempt to plant the “Spark” backdoor onto the victim’s system.
- The attachments are either macro-ridden documents of PDF files containing dangerous URLs.
According to a report by Unit 42 researchers, the Gaza-based hacking group known as “Molerats” has been targeting organizations and governments in six countries since at least October 2019. The targets of the hackers are governmental entities, telecommunication providers, firms active in the fields of insurance and retail, and more. While the attacks are widespread and lengthy, the researchers report that they are not very successful because the actors do not use very sophisticated social engineering practices or even industry-specific themes. This creates confusion around what their real purpose is, as Molerats is a lot more capable than what they’re demonstrating in this campaign.
The attacks begin with a phishing email, which is accompanied by a password-protected Microsoft Word document. As expected, the document contains a malicious macro, which fetches the "Spark" backdoor. This malware enables the actors to open applications on the target system or even to execute command-line commands. The actors are using the following filenames for their attachments: ‘MOFA- 031019.doc’, ‘MOFA- 061019.doc’, ‘MOFA- 101019.doc’, ‘attachment.doc’. ‘Pictures.pdf’, ‘Urgent.docx’. As for the subjects in the email, these usually include “MOFA reports”, various dates, or calls for Islamic jihad against Israel.
Source: Unit 42
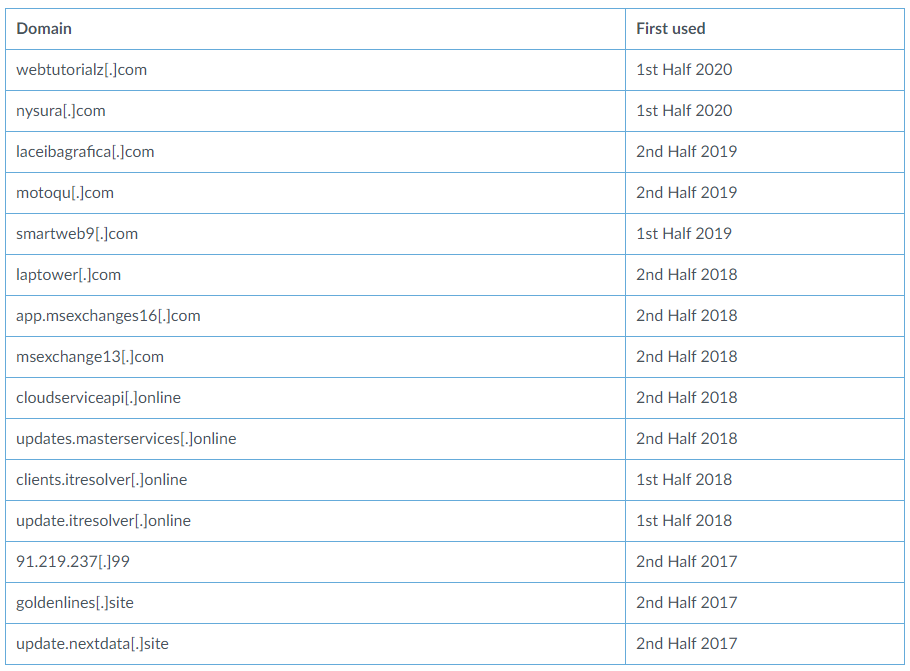
While the document files rely on malicious macros, the ‘Pictures.pdf’ attachment follows a different approach, containing a fake message and a URL link on the bottom. If the user clicks on the link, they will be taken to ‘hxxps://zmartco[.]com/Pictures.rar’, which is an archive containing an executable “photos.exe”. If launched, it plants the Spark backdoor onto the victim’s system. The persistence mechanism is established by copying the executable to the startup directory and also by creating a scheduled task through the Windows Task Scheduler. As for the rest of the campaign’s toolset, the hackers are using the VMProtect and Enigma packers, while the C2 domains that were identified by Unit 42 are the following:
Source: Unit 42
The countries that were in the crosshair of Molerats are the United States (insurance and retail), Spain (government), United Kingdom (government), the United Arab Emirates (government), and Djibouti (telecom). In the case of the small African country, the group is showing signs of more specific targeting as they are using religious calls as bait. Djibouti is an Islamist country with a “Not Free” ranking by the ‘Freedom House’, so its people would be more willing to join jihad operations. Other than that, though, the specific goals of Molerats this time are somewhat blurry.