Hackers Use Malicious 3ds Max Plugin for Cyber-Espionage
- Bitdefender has discovered a novel group of mercenary hackers, and their target was a prestigious architect firm.
- The hackers managed to break in by using a specially crafted 3ds Max plugin, which plants a backdoor onto the target.
- The malware would take screenshots and steal credentials from web browsers, but it would go to sleep if the user opened the Task Manager.
Researchers of Bitdefender have been following the activities of a previously unknown hacker-for-hire group that uses a novel method to compromise companies. According to a report that the security company published today, the actors are using a third-party plugin for Autodesk 3ds Max to corrupt the program and run malicious code on the target system.
The plugin is named “PhysXPluginMfx” and can propagate to other MAX files, like other computers in the target firm. Autodesk was informed of this problem since two weeks ago and published a relevant security advisory about it.
The actors appear to be based in South Korea, or at least this is where their C2 infrastructure lies. As for the targets, Bitdefender mentions an architect company that is involved in billion-dollar real estate projects in New York, London, and Oman.
The 3ds Max is a professional 3D graphics software used by architects to create building models, so this is a highly targeted cyber-espionage operation. Usually, mercenary hackers are based on phishing emails, but in this case, we have a tailored payload that can even bypass the target’s security solution.
Source: Bitdefender
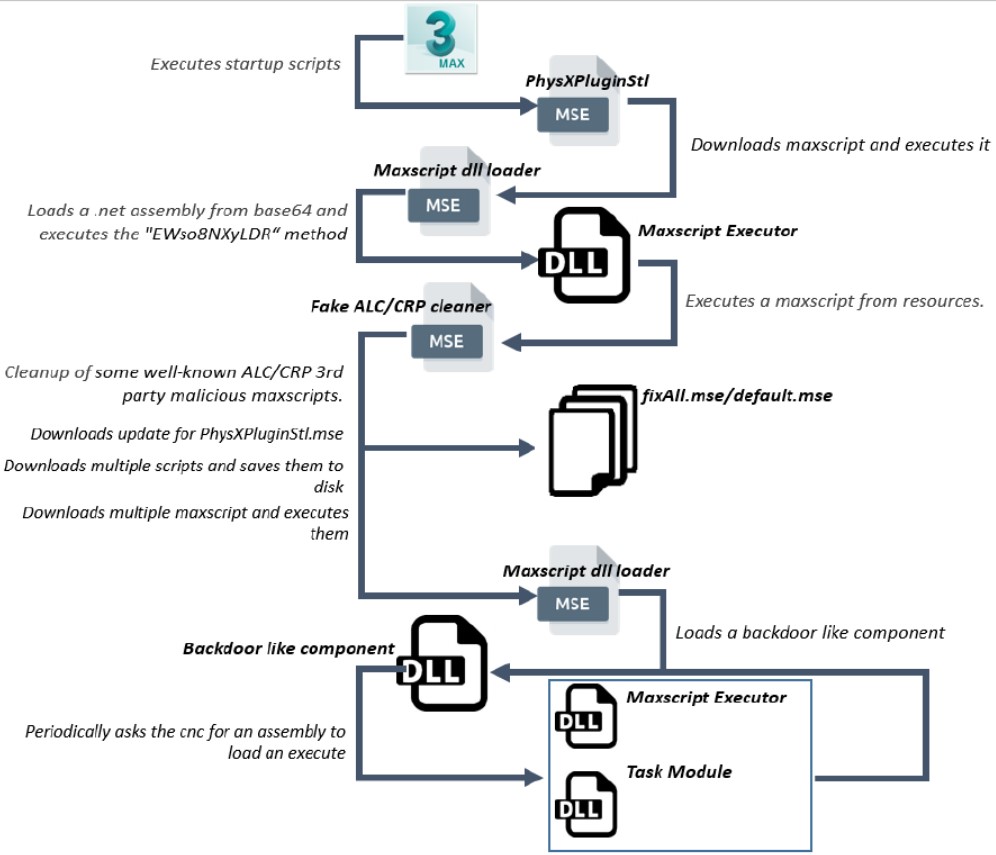
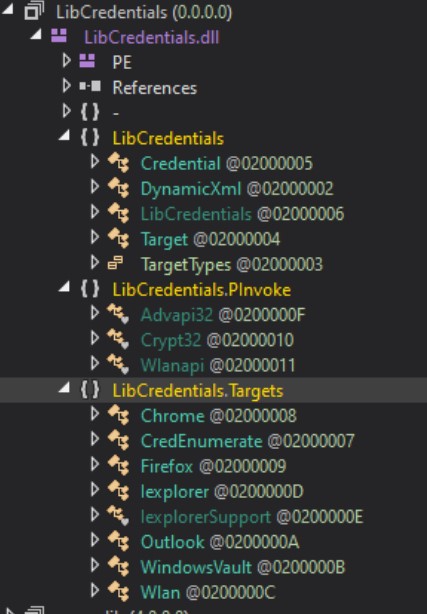
The malicious plugin basically downloads a series of maxscripts that are saved to the local disk, drops DLLs, starts HTTP posts requests directly from memory, creates periodic cleaning jobs, and eventually plants a backdoor component. From there, the malware could take screenshots from the compromised system, and also collect credentials that are stored in Chrome, Firefox, IE, WLan, and Outlook.
Additionally, the malware can collect the username, IP addresses of network adapters, .NET Framework version, hardware information, and eventually upload everything to the C&C server.
Source: Bitdefender
If the victim opened the Task Manager or the Performance Monitor, the backdoor binary would automatically enter “sleep” mode so as the CPU resources consumption would drop, and the associated process wouldn’t be visible on the list. This is just another detail that underlines the sophistication of the actors and their tools.
As Bitdefender points out, the particular group may have been active for more than a year already, having managed to fly under all security teams’ radars thus far. The researchers are now looking deeper into the connections made to and from the mapped infrastructure, trying to figure out if the group launched more attacks, if they rented their services to others, and hopefully, who they are.
Read More:
- Chinese Vendor of OLT Devices Loads them with Firmware Backdoors
- The “Turla” Group Has Updated Its ComRAT Backdoor to Work Smart Through Gmail
- At Least 1,200 iOS Apps Constitute a Privacy Risk for Users