Hackers Actively Target FortiGate and Pulse Secure VPN Credentials
- An urgent warning to update your FortiGate and Pulse Secure VPN products is doing a final circulation.
- Actors are now using a publicly available exploit code and actively search for vulnerable systems.
- The consequences of getting attacked are dire, as the exploit leads to full network penetration.
ArsTechnica warns that hackers are actively trying to steal encryption keys, passwords, and user credentials from two corporate VPN (Virtual Private Network) products, namely the Pulse Secure SSL VPN and the FortiGate SSL VPN. The revelation about this activity came earlier in the month during Devcore’s Black Hat conference presentation that showed data about the scanning that is going on, and the crooks’ effort to find vulnerable servers. Collectively these two products are installed on a total of 530 thousand machines, so the problem is a large scale one right now.
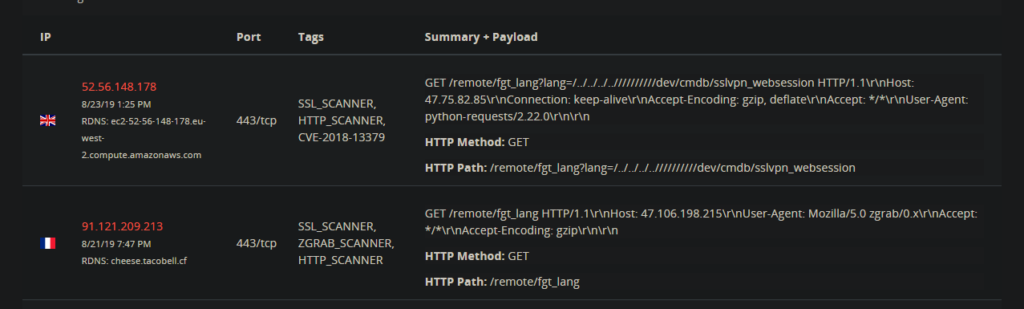
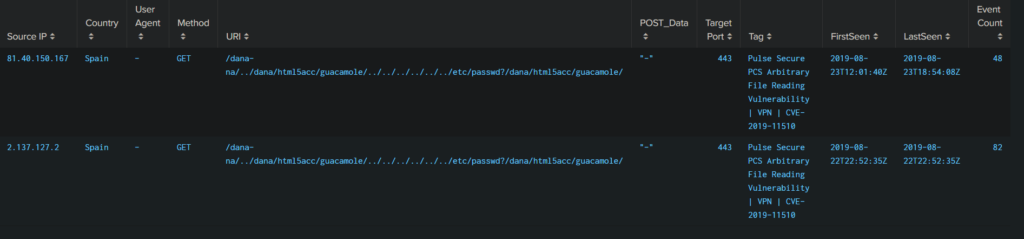
The Devcore researchers identified the exploits that are used by the actors, which are already indexed as CVE-2018-13379, CVE-2019-11539, CVE-2018-13383 (magic backdoor), and CVE-2019-11510. This means that the flaws have been fixed thanks to patches that were released by the product vendors, but as many machines remain unpatched, actors have a reason to continue their scanning and exploitation efforts. As one researcher told Ars: “These scans are targeting endpoints that are vulnerable to arbitrary file reading leading to sensitive information disclosure of private keys and user passwords. They're exploiting this vulnerability to read the contents of the `etc/passwd file to steal credentials. These credentials can then be used to conduct further command injection attacks and gain access to the private network allowing for further malicious activity.”
The group of researchers used a honeypot provided by BinaryEdge to log some attacks in order to figure out how the vulnerabilities are being exploited. The IP address of the attacker that they captured was one belonging to a known actor that has been reported for abuse over 90 times. The code that was used for exploitation has become publicly available on Packet Storm since August 21. The honeypot server caught more IPs of course, as the spraying efforts have culminated over the past two days.
image source: arstechnica.com
image source: arstechnica.com
Stealing hard-coded keys could potentially enable remote attackers to change server passwords, with full network penetration remaining the central risk in this situation. Simply put, if you’re using a FortiGate or Pulse Secure VPN product and you have not updated it yet, make sure to apply all available patches as soon as possible. As we mentioned, there are numerous malicious actors who are actively seeking for vulnerable systems out there right now, and you really don’t want to risk it anymore. For added security, enable full log audit and send to an out-bound server, enable multi-factor authentication, and also client certificate authentication.
Have you already implemented the above safety measures? Share your comments with us in the section down below, or join the discussion on our socials, on Facebook and Twitter.