Hackers Spread Ransomware to the IObit Forum Users
- DeroHE ransomware actors have compromised the IObit forum and one of the firm’s email accounts.
- The actors then sent fake promotional messages to forum members, tricking them into downloading and installing ransomware.
- The extortion now goes against both the individual users and the firm, asking $100 and $100,000, respectively.
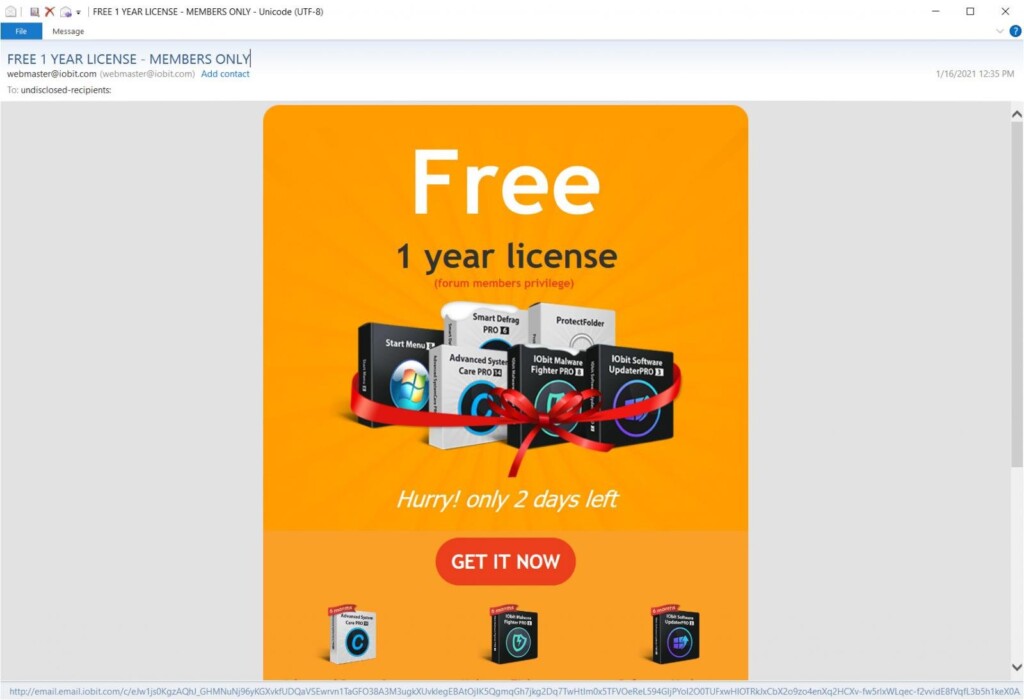
Members of the IObit forum started receiving some weird messages from the firm’s official email address over the weekend, which seemed phony to those careful enough. The emails offered a free 1-year license to IObit products, which are generally system optimizers and security solutions for Microsoft Windows operating systems.
Those who clicked on the “Get it Now” button were redirected to a ransomware distribution page that is currently offline. The file downloaded from there is a ZIP containing the DeroHE ransomware. Unfortunately, quite a few users fell for this and installed the contained app, thinking it was a legit promotion message.
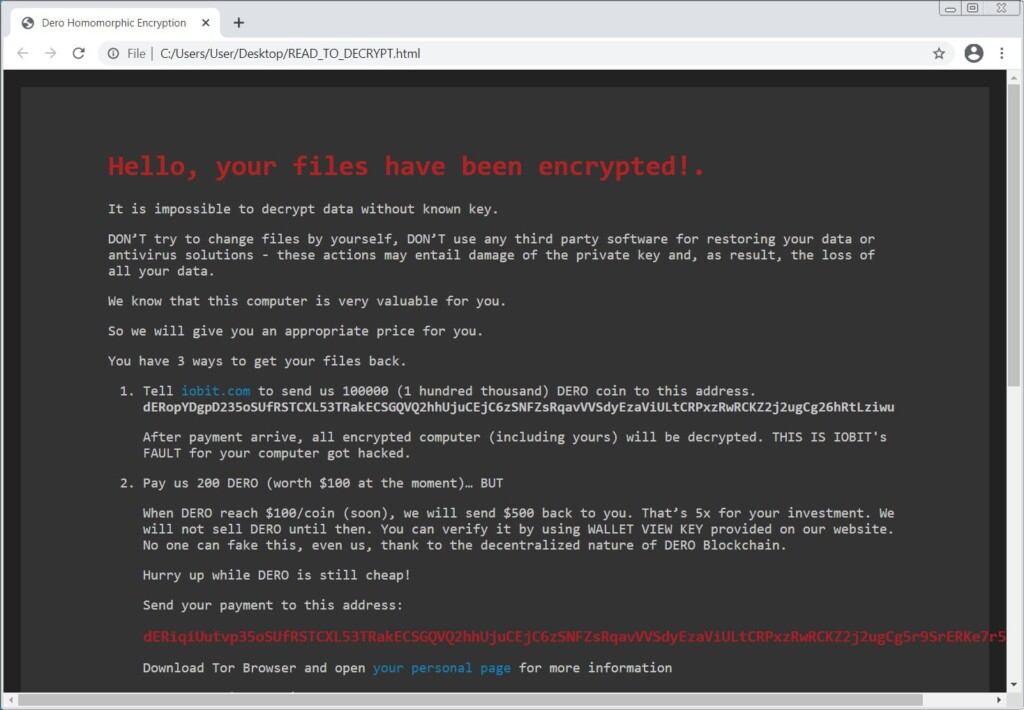
The result was a nasty infection locking down all files and appending the “.DeroHE” extension, corrupting file headers and breaking them down into fragments, further reducing the possibility of a successful recovery. Funny enough, the victims are coerced into investing in DERO, and the actors are even giving a promise to return $500 to them when the coin's value rises.
As it appears to be the case, this large-scale attack had financial motives, as the actors are targeting both the users and the IObit platform. While people got a ransom note which asks about $100 from them, paid in DERO, the attacker's Tor site enlists IObit as a victim too, demanding a payment of $100,000. If the platform covers the amount, the actors will supposedly decrypt all of the users’ systems.
Those using AV tools didn’t see much difference when they attempted to execute the malicious file, as Virus Total reports a detection rate of only 23.53%. The reason for this failure is the fact that the authors of the malicious package have used signed certificates, and this helps the ransomware pass most AV checks. The executable even adds Windows Defender exclusions as required for the next stage to run, so the tricked user is left helpless.
The particular ransomware family remains impossible to decrypt for free as there are no available decryptors for it. If you’re a victim of this attack, you’d better disconnect from the internet, wipe your disks clean, reinstall the OS, and then restore from backup. If you don’t have a backup of your data, let this be a lesson to keep regular backups in the future. Whatever you do, do not pay the ransomware actors, as there’s no guarantee they’ll send you a working decryptor. Even if they do, there’s no guarantee it'll work to restore all your files.
Until now, IObit hasn’t clarified what exactly has happened, but it looks like someone has managed to take over an admin account on the forum site. BleepingComputer has even found more malicious redirections and scripts on the IObit forum site, so the problem appears to be extensive right now.