Hackers Exploit Browser Kiosk Mode to Harvest Google Credentials
- Hackers were observed deploying malware that exploits browser kiosk mode to steal Google credentials.
- The user's actions are restricted to a single, non-closable window displaying the Google login page.
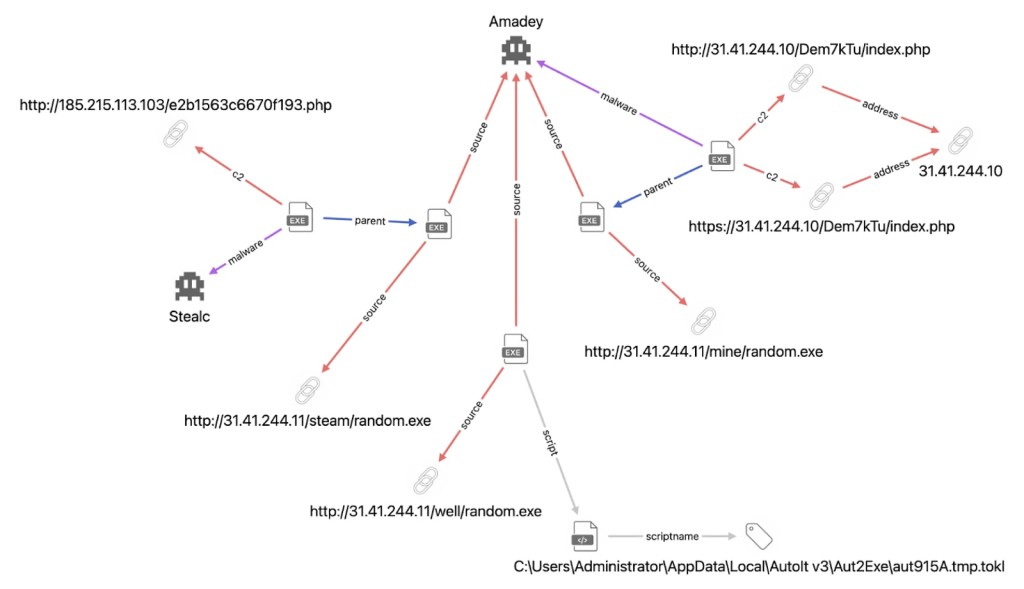
- The campaign mainly relies on Amadey, a malware loader, info-stealer, and system reconnaissance tool.
An unusual attack vector was used to compromise user credentials in a novel malware campaign discovered by OALABS’ security researchers. This sophisticated malware locks users into their browser's kiosk mode as part of its strategy to steal Google credentials.
The malware's modus operandi involves initiating a lock on the user's browser directed at Google's login page. The tactic is designed to frustrate users into entering and saving their Google credentials, believing that doing so will restore regular access.
This lock is cunningly crafted, disabling the "ESC" and "F11" keys, preventing users from exiting the browser or navigating away.
Upon saving the credentials in the browser, the StealC information-stealing malware swiftly harvests them. This malware extracts login details from the browser's credential store and transmits them back to the attacker.
The hackers employ Amadey, a malware loader, info-stealer, and system reconnaissance tool, which has been operational since 2018, and an AutoIt script to instigate the credential flushing process.
The malware scans the infected system for browsers and launches the targeted one in kiosk mode, redirecting it to a pre-specified URL. It launches the browser in kiosk mode, directing it to Google's login page without conventional UI elements, such as toolbars or navigation buttons.
The campaign has reportedly been active since at least August 22, 2024.
Recently, a widespread campaign was seen luring victims via fake download sites looking like Roblox FPS Unlocker, YouTube, VLC, or KeePass to distribute Trojans that install malicious web browser extensions to steal sensitive user data.
In June, a ‘Fake Browser Update’ campaign infected vulnerable sites to show malicious pop-ups promoting a Web browser update that downloads malware when clicked. However, it hid behind a legitimate WordPress plugin to evade discovery by file scanners, as it’s usual for plugins to store data in the WordPress database.