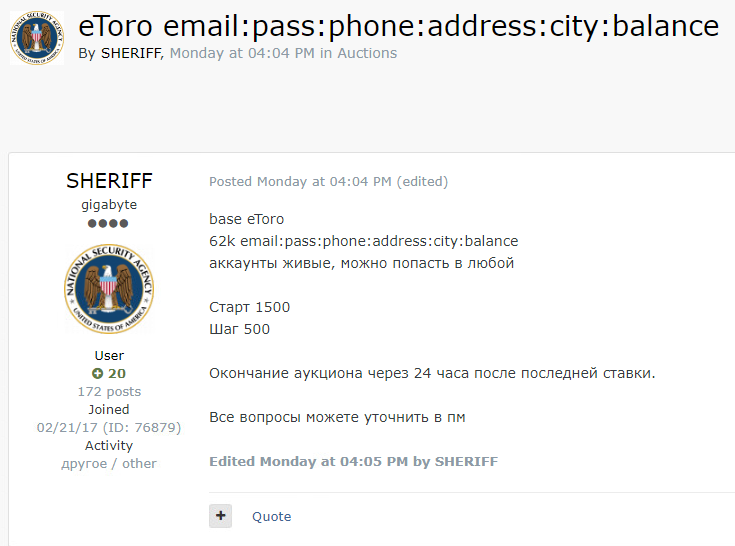
Hackers Are Selling 62,000 Active eToro Accounts on a Dark Web Forum
- An actor known as “Sheriff” is selling tens of thousands of eToro user accounts on a dark web forum.
- The sale is an auction, and the threat actor promises fully working credentials.
- “Sheriff” has been collaborating with “REvil” in the last couple of months, selling them access to corporate networks.
A new group of Russian hackers using the “Sheriff” alias have put up 62,000 active eToro accounts for sale on the dark web. The listing first appeared online on July 6, 2020, and it is an auction with bidding steps of $500 and a starting price of $1,500. The highest bidder gets that data pack exclusively, which comes with the ability to withdraw funds from 62,000 accounts. eToro is a popular cryptocurrency trading platform and stocks investment portal that has been around since 2007, serving about 6 million users from 140 countries.
Bleeping Computer
Sheriff promises that the user login credentials they offer for purchase are all working, so the accounts are perfectly exploitable. Moreover, the pack contains phone numbers, postal addresses, and available balances. For now, eToro hasn’t issued an official statement on this matter, so it is quite possible that the data is indeed valid. Sheriff has performed a few sales in the recent past and they seem to be a new threat actor, but researchers believe they have ties with the REvil ransomware operators. In fact, some believe that REvil has contracted Sheriff and paid them to attack various banks and financial institutions, which is apparently the specialization of the new actor.
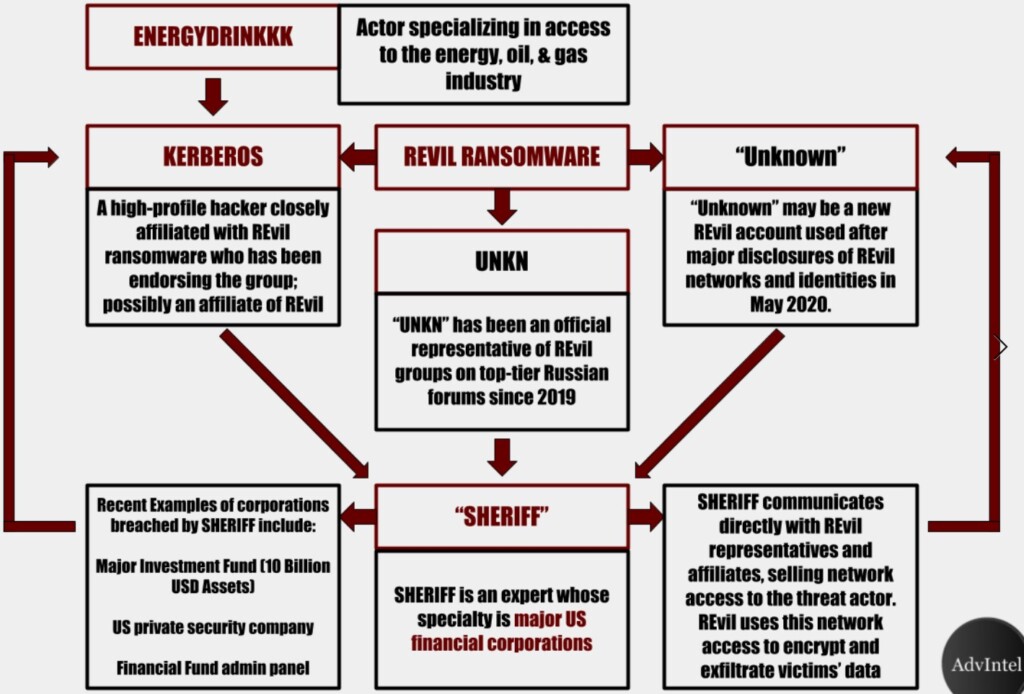
“Advanced Intelligence” has found many ties between REvil and Sheriff, with the latter rising very quickly in notoriety by managing to breach very large organizations. They then let REvil in the compromised networks, who exfiltrate all data and encrypt the files locally, initiating their typical extortion process. In some cases, Sheriff used the “UNKN” persona to collaborate with REvil, but they are both essentially the same group of hackers. The fact that the eToro user data sale is done through Sheriff is an indication that the two groups are independent.
Source: advanced-intel.com
As for the method of attack, AdvIntel believes that Sheriff is breaking in the systems of large financial institutions via brute-force attacks and by deploying credential-stealing malware tools. The group navigates the compromised networks and accesses admin panels until they find valuable data, which they then exfiltrate by using SQL injections and cross-site scripting attacks. When they work on the account of REvil, however, Sheriff limits these activities to merely providing the ransomware actors access to the networks they are looking to enter. In the past few months, Sheriff has been knocking on the Citrix RDP door, using stolen user credentials.
Read More:
- “Lion” Compromised by REvil Ransomware Actors Who Are Leaking Data
- Ransomware Actors Now Engage in Auctioning Stolen Data
- Brazilian Electric Power Company Extorted by REvil Ransomware Actors