Hackers Have Been Actively Exploiting DrayTek Equipment Zero Days
- DrayTek equipment was under active exploitation between December 2019 and February 2020.
- The network equipment vendor has released a fixing firmware update and advised everyone to apply it.
- Two individual hacking groups exploited the flaw, one for eavesdropping and the other for backdoor planting.
Researchers of the Qihoo 360 NetLab report that at least two separate hacking groups are actively exploiting zero-day flaws that affect various DrayTek network devices. The associated vulnerability that was assigned the identifier “CVE-2020-8515” concerns the possibility of launching remote code execution (RCE) attacks as root via shell metacharacters to the cgi-bin/mainfunction.cgi URI, without having to authenticate as the admin.
DrayTek is a Taiwan-based manufacturer of CPE (Customer Premises Equipment) products that are used by companies and organizations from around the world. A security expert who searched on Shodan back in January found 710,029 Draytek host deployments globally. The affected DrayTek products include enterprise switches, load-balancers, routers, and VPN gateway devices using older firmware versions. Simply put, the attackers can exploit the flaw to eavesdrop on the network traffic, run SSH services on high ports, and create web session and system backdoor accounts.
#0-day Since 2019-12-04 08:22:29 (UTC), we have been witnessing ongoing 0 day attack targeting a network CPE vendor (not the big players, but there are about ~100,000 devices online according to public available data). The attacker is snooping on port 21,25,143,110 (1/2)
— 360 Netlab (@360Netlab) December 25, 2019
The researchers report that they first noticed these attacks on December 4, 2019, and they disclosed it on Twitter towards the end of the year without mentioning the victimized vendor. On February 10, 2020, DrayTek released firmware version 1.5.1, which plugged the RCE hole. The list of affected products with the vulnerable firmware versions is given below.
- Vigor 2960 < v1.5.1
- Vigor 300B < v1.5.1
- Vigor 3900 < v1.5.1
- Vigor Switch 20P2121 <= v2.3.2
- Vigor Switch 20G1280 <= v2.3.2
- Vigor Switch 20P1280 <= v2.3.2
- Vigor Switch 20G2280 <= v2.3.2
- Vigor Switch 20P2280 <= v2.3.2
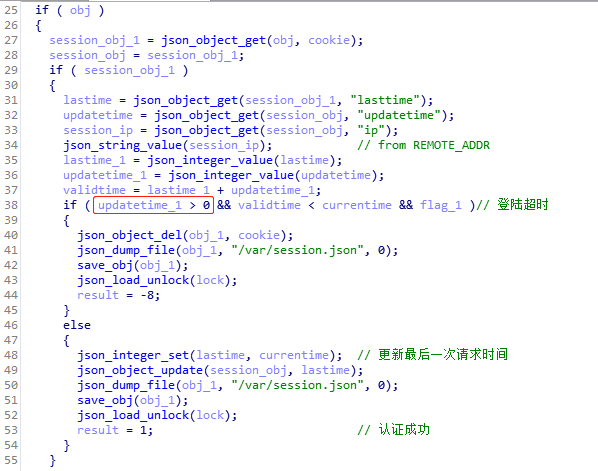
The 360 NetLabs report names the hackers as “Attack Group A” and “Attack Group B,” so there has been no specific attribution. The first actor executed a script used to eavesdrop all network interfaces on the target DrayTek Vigor device, listening on the ports 21, 25, 110, and 143. A crontab process would then upload the captured network traffic packets three times a week. The second actor went a step further, planting two sets of Web Session backdoors that never expire, SSH backdoors on TCP, and a system backdoor account. The Web Session backdoor is setting a “updatetime” parameter to “0”, and the “Auto-Logout” to “disable.”
Source: NetLab360 Blog
To mitigate this risk, you are advised to apply the firmware updates as soon as possible and then check for any backdoors in your systems. Also, the presence of a tcpdump process would indicate that you’re being exploited. If upgrading the firmware is impossible for any reason, you should temporarily disable remote admin access and SSL VPN, and use an access control list instead.