Hacker Is Selling Live Server Access to an OTP-Generating Telco
- Someone is selling access to a webshell planted onto the servers of a large telco.
- The sale also includes exfiltrated data containing millions of OTPs for various online platforms.
- The firm has been informed about the case but denies having suffered any breaches.
A hacker is selling real-time access to the one-time-password system of numerous entities on the dark web, implying the ability to bypass two-factor authentication needed to take over Google, Facebook, Amazon, Apple, Microsoft, Signal, Telegram, Twitter accounts, and any other entity trusting the OTP-generating vendor.
This is really scary and far-reaching, but it’s the natural consequence of having access to servers that handle OTP generation requests from users of online services.
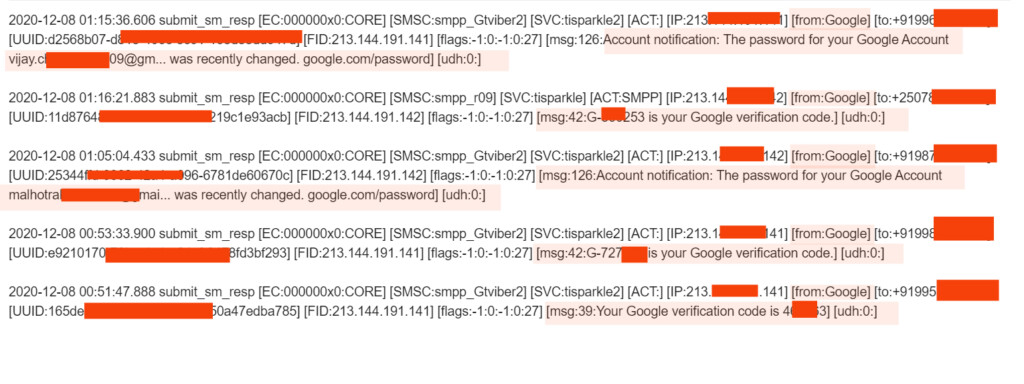
The tip about this came to us from independent researcher Rajshekhar Rajaharia, who has shared some details about the listing he saw on the dark web marketplace. The listing offered 50 GB of exfiltrated data and also webshell access to the unnamed OTP-generating platform. The access price was set to $5,000, dropped from the initial tag of $18,000. The firm’s name was mentioned in the listing, but we won’t share it yet for security reasons.
The researcher checked the samples and confirmed that there are one-time codes in there. This doesn’t mean that all of them are usable or valid today, but depending on the platform and its policies, the pack buyers could find working stuff in there. The most dangerous aspect, though, is the use of the planted webshell that could potentially incur very damaging results.
Other types of data included in the sold pack are SMS logs, mobile numbers, email addresses, SMPP details, customer documents, and more. The data dates from 2017 until now, so it's pretty extensive.
The seller has taken the listing off of the dark web marketplace where they posted it a couple of days ago, but the sale continues on Telegram. Based on the latest details we could get, there are ten million OTPs included in the pack, while the number of buyers is unknown.
Rajaharia tells us:
The telco responded to the reports on social media, and claimed that they have suffered no data breaches, and their systems remain secure. Moreover, they said that the authenticity of the alleged data could not be verified. They did, however, mention that they are working with a third-party expert to help them audit their systems, so if there’s still a webshell there, they will find and uproot it.