Hacker Leaks Data of Ecuador’s Public Telco Stolen Last Month During a Ransomware Attack
- A forum user has posted a link to the dataset that was stolen from CNT during a ransomware attack last month.
- CNT (Corporación Nacional de Telecomunicaciones) hasn’t acknowledged the data breach yet and continues to ignore it.
- The data is now shared for free with a much wider audience than previously, so the implications have now become severe.
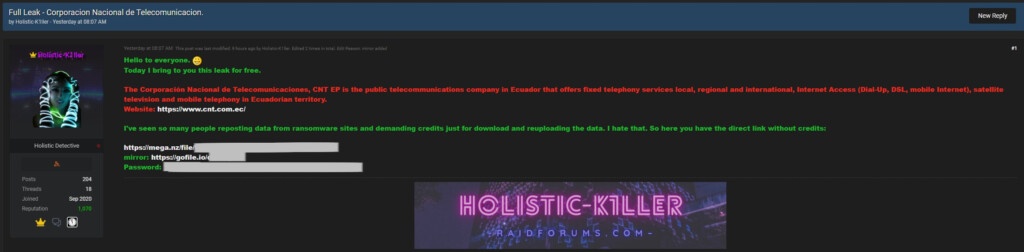
A hacker named ‘Holistic-K1ller has leaked the entire 11.23GB of the data set that was stolen from CNT (Corporación Nacional de Telecomunicaciones) last month from ransomware actors and is now sharing it for free via a Mega link posted on RaidForums. The forum listing confirms that the data is the same, and although the ransomware actors, ‘RansomEXX,’ initially claimed to have stolen 190 GB, they ended up posting 11.23 GB in 23 parts.
The attack became evident via a disruption of CNT’s operations and, more specifically, the company’s payment portal and customer support service. On July 16, 2021, the state-run telecommunications carrier published a statement to inform its customers of an attack on their computer systems. On the same notice, CNT assured the public that no data had been accessed or stolen and that their internet connectivity, TV, and telecommunications services will remain unaffected.
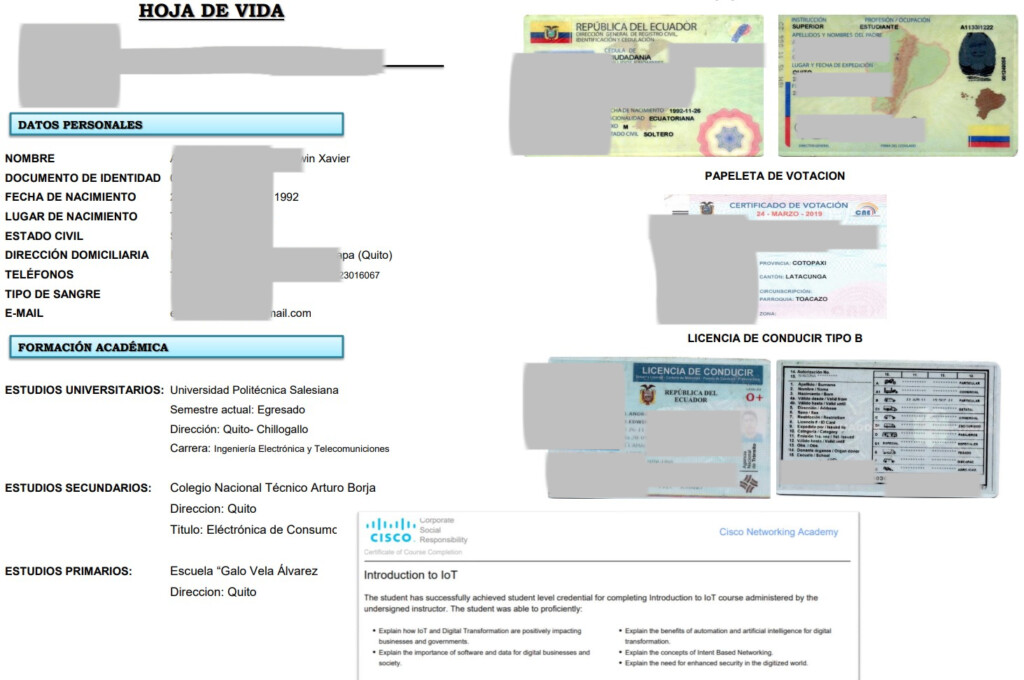
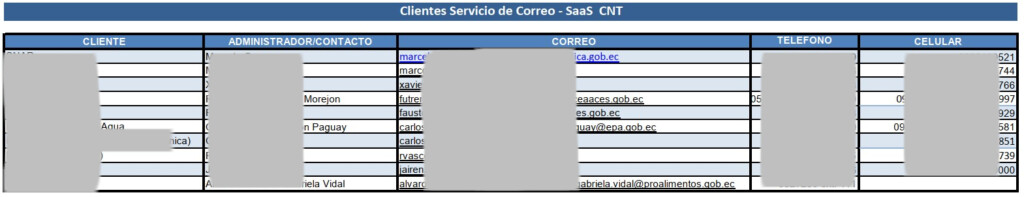
However, the RansomEXX posted the first samples of the data on July 21, 2021, when the initial negotiations for the payment of the ransom showed their first signs of a stall and eventually let it all out when it became clear that the firm wouldn’t pay them a dime. The leaked data includes documents containing sensitive information on CNT employees, names and contact details of clients, confidential documents like contracts with third parties, and even ID or driver’s license scans.
Although this data set has already been posted by the ransomware gang almost a month ago on the Tor extortion portal, seeing it shared for free on RaidForums makes a qualitative difference in the data breach incident. Not everyone knows how to access a Tor site, or is open to visiting a web page on the dark web, so even if the data was leaked there, they didn’t reach the wider audience that has access to a clearnet site like RaidForums. As such, the implications of the ransomware incident for CNT, its employees, and its clients have just taken shape on their actual proportions.
We have reached out to CNT to ask them about their plan on how to mitigate the effects of this data leak and the risks that arise for their customers, but we haven’t received a response from them yet. Unfortunately, the company is yet to confirm the data breach in the first place, so they’re still several steps behind the actual situation.