Hacker Leaks Alleged Proof-of-Concept for Zero-Day Vulnerability in 7-Zip
- A hacker posted a PoC for a 7-Zip flaw linked to its LZMA decoder, which allows arbitrary code execution.
- The risk appears when malicious 7Z archive files are opened or extracted using the latest version of 7-Zip.
- Releasing PoCs for zero-day exploits without prior warning leaves systems unprotected, so this post could be leveraged by attackers.
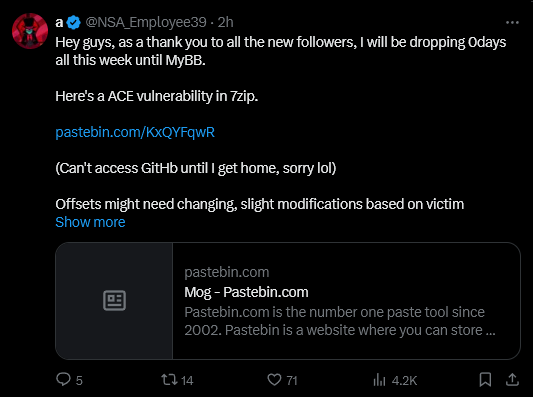
A potentially devastating zero-day vulnerability targeting the widely used file compression utility 7-Zip has reportedly been leaked online on X (formerly known as Twitter) by a hacker operating under the alias “NSA_Employee39.”
Identified as CVE-2024-11477, this exploit allows attackers to execute arbitrary code on a victim’s machine when malicious 7Z archive files are opened or extracted using the latest version of 7-Zip.
The zero-day exploit specifically targets the LZMA decoder within 7-Zip. By leveraging a malformed LZMA stream, attackers can trigger a buffer overflow in the RC_NORM function.
This sophisticated technique manipulates buffer pointers and aligns payloads to inject and execute arbitrary code on the victim’s system, bypassing any need for further user interaction.
For demonstration purposes, the hacker “NSA_Employee39” shared proof-of-concept (PoC) code on Pastebin, showcasing the potential of this attack by executing a harmless payload that launches Windows Calculator (calc.exe).
However, cybersecurity experts caution that this benign payload can easily be replaced with more malicious code, significantly amplifying the exploit’s dangers. Yet, simply opening or extracting a compromised .7z file would trigger malicious shellcode execution, leaving their systems vulnerable to infiltration.
The disclosed zero-day adds a new dimension to the operations of Infostealer malware, which is commonly deployed to steal sensitive information such as login credentials, banking data, and personal files.
Traditionally, infostealers rely on password-protected archive files as part of their social engineering strategies to evade antivirus detection. However, this vulnerability eliminates the need for such tactics, allowing attackers to infect systems simply by tricking users into opening infected .7z files.
By embedding malicious payloads within .7z files, attackers could infiltrate enterprise systems undetected.
While the 7-Zip exploit poses a serious threat, exploiting it does require a high degree of technical proficiency. For instance, shellcode must function within a constrained space of only 100–200 bytes.
The public leak of this zero-day vulnerability has sparked concerns over the responsible disclosure process. Typically, vulnerabilities reported through official channels allow developers to patch them before they can be exploited.
However, disclosing a vulnerability publicly without prior warning leaves systems unprotected, granting attackers a significant advantage. To exacerbate concerns, the user mentioned releasing another zero-day exploit targeting MyBB, a popular open-source forum software.