Greek Hemodialysis Unit Operator Hit by Ransomware Gang That Threatens DDoSing
- The Avaddon ransomware gang has compromised a Greek operator of five hemodialysis units.
- The crooks are already leaking out sensitive employee documents on their dark web portal.
- The firm is investigating the incident, but the documents appear to result from a data breach on their systems.
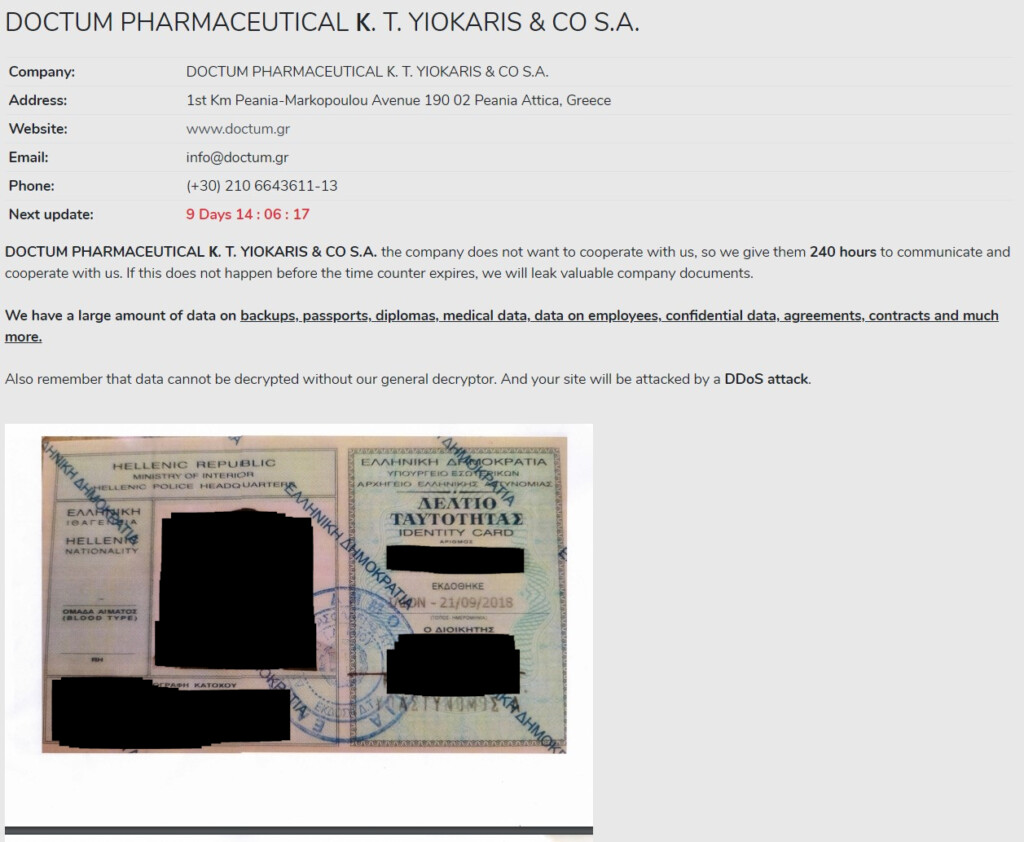
If you’re looking for yet another example that underlines how unethical and inconsiderate ransomware groups are, you have come to the right place. Avaddon gang's actors claim to have hit ‘Doctum,’ an Athens-based healthcare specialist that operates five large hemodialysis units in the Greek capital, manufactures and resells pharmaceutical products, artificial kidney solutions, disinfectant solutions, immunotherapy vaccines, and various critical medical products.
The actors have given the company ten days to comply with their demands; otherwise, they threaten to start launching DDoS attacks. If that happens, the process of booking hemodialysis appointments could be disrupted, and generally, human lives could be put at risk.
On the Doctum website, we can see that the company’s units offer dialysis services to 600 patients, and several contractors rely on its products and services to help their nephrology patients. So, all in all, threatening to DDoS this company is no joke.
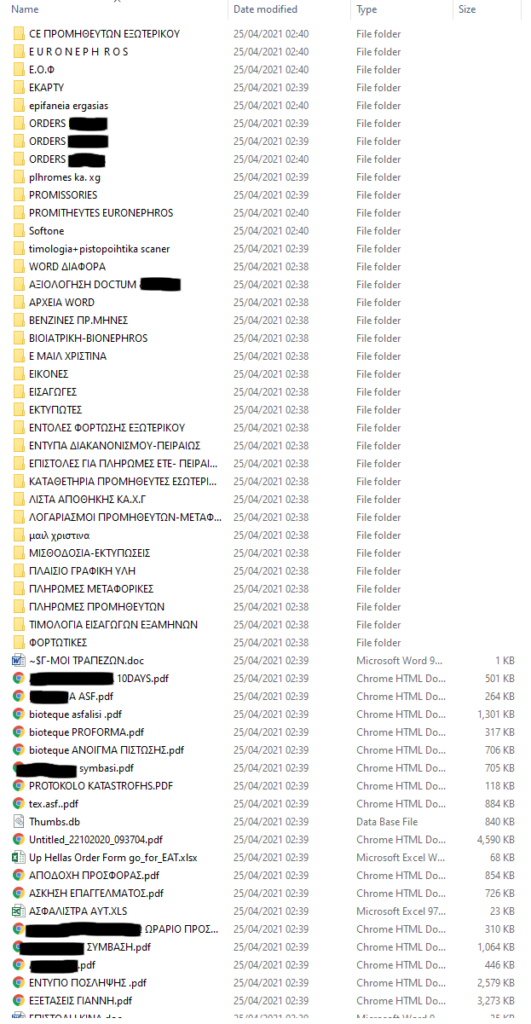
The Avaddon group says Doctum doesn’t want to cooperate with them, which probably means they have failed to establish communication. In response to that, they are already leaking sensitive documents on the extortion portal, such as national ID card scans, contracts, degrees, tax declaration documents, medical details, employee details, filesystem snapshots, IBANs, and more.
The threat is to leak everything when the time’s up, which could involve patient data too, although we cannot see any relevant folders in the leaked screenshots. What we can see are payrolls, supplier info, payment letters, and more.
We have called the company to ask about the possibility of client data leak, and a spokesperson told us that they are currently investigating the incident and have no comments to make at the moment. However, the validity of at least some of the information on the leaked documents that appeared on Avaddon’s portal has been confirmed, so the data breach appears to be real, even if not confirmed by the victim yet.
Avaddon appears to have a preference for targeting smaller entities that can still yield significant ransom payments. Only a few weeks back, we discussed why the particular group decided to hit the small Italian town of Villafranca in northern Italy. As for the way in, there have previously been confirmations about the use of Excel macros arriving onto the inbox of employees of the target companies, carrying malicious XML macros that initiate the infection process.