Gravy Analytics Data Leak Exposes Alarming Location-Spying Activity
- Location data of millions of users globally is revealed via apps without the consent of users or app makers.
- Android and iOS apps have ads that stealthily trace precise user locations.
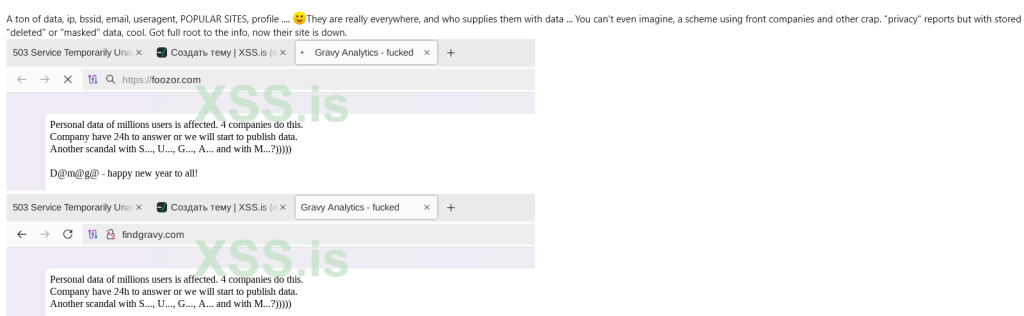
- A hacker on the Russian breach forum XSS threatens to leak IP addresses, profile data, and more.
In a startling revelation, it was found that a location intelligence company, Gravy Analytics, was storing location information from thousands of apps globally. This was done through advertisements that reflected on apps that stored users’ locations.
Oddly enough, most app companies seemed unaware or oblivious to the location spying activities conducted using their platform. The massive location data infiltration scandal came to light when a hacker posted on the dark web that they stole data from Gravy Analytics.
Following this, researchers found a post on the Russian cybercrime forum XSS boasting about the data exfiltration from Gravy Analytics. The hacker claimed to have information including but not limited to IP, bssid, email, user agent, and profile.
Reacting to the amassing of location data, the hacker exclaimed, “They are really everywhere, and who supplies them with data.. You can’t even imagine a scheme using front companies…”privacy” reports but with stored, “deleted” or “masked”.”
The hacker threatened to publish the data on XSS within 24 hours if their demands were not met.
Taking cognizance of the gravity of the location data exposure, several data analysts, and cybersecurity experts jumped to the scene to investigate the truthfulness of the claim.
They found that the data stored by app stores did not have a time stamp. However, some samples indicated that they were from 2024. The Season 5 iteration of the mobile gaming app Call of Duty, launched in May 2024, was found in the list.
Upon enquiring, a few of the named companies replied. Muslim Pro denied knowing Gravy Analytics. However, it did mention the need to float ads on apps to keep the service free for users. Likewise, Tinder also denied having heard of Gravy Analytics.
Although it is claimed that the hacker stole the geolocation data from Gravy Analytics, it could not be said with certainty whether it collected or sourced information from its client companies. It is also suspected that threat actors used Google Ads to get location data.
The number of apps named in the location data heist is estimated to be over 12,000. Popular apps include Accu Weather, Super Fast VPN Proxy-Better, Chess, Capcut, Tinder, Moovit, Temple Run, Viber, and MyFitnessPal.
The list includes apps available on Android and iOS belonging to various categories. A few of them are as follows:
VPN
- HotspotShield VPN & Wifi Proxy
- HaloVPN Lite: Fast VPN Proxy
- Japan VPN
- Offline: Files, Browser, VPN
- VPN Expert - Secure VPN Proxy
- X-VPN Unlimited VPN Proxy
- Voice VPN - Fast VPN
- vpnify - Unlimited VPN Proxy
- SecVPN Proxy Tool
- VPN - Fast Secure Proxy
- Free VPN Proxy by Planet VPN
- VPN - Super Unlimited Proxy
- U-VPN (Unlimited & Fast VPN)
- HulaVPN - Fast Secure VPN
- VPNIFY - Unlimited VPN
- X-VPN Unlimited VPN Proxy
- Voice VPN - Fast VPN
- Rapid VPN - Safe Secure Proxy
- Turbo VPN Private Browser
Games
- Run Race 3D — Fun Parkour Game
- Jigsaw Puzzle
- LUDO
- Wood Block Puzzle - Block Game
- Spider Solitaire: Card Game
- Acertijo Mental: Brain Games
- Bubble Boxes - Matching Games
- Rummy - free card game
- Life Choices: Simulation Games
- Daily Bible Trivia: Quiz Games
- Backpack Brawl
- Bible Word Cross Puzzle
- Score! Hero
- Richie Games - Play & Earn
- Subway Surfers
- Solitäre
- Angry Birds Match 3
- Bible Verse Collect - Free Bible Word Games
- Mason Craft
- Draw Puzzle Line: Brain Games
Health and Fitness
- LazyShape: Weight Loss at Home
- Lose Weight App - Fitness
- Health Recorder - Heart Rate
- BMI Log
- Drink Water Reminder & Fasting
- Lose Weight App - Fitness
- Blood Pressure - Blood Sugar
- Blood Sugar
- Blood Pressure Tracker & Diary
- Daily Yoga: Fitness+Meditation
- BP Cozy
- BP CirculationCheck
- Natural Remedies: healthy life
- Healthy Guy
- Health Kit
- Health Tracker
- HeartEntry
- Period Tracker & Diary
- Pregnancy Due Date Calculator
- MMMMental health test
Religion
- Muslim Pro
- Religion Inc. God Simulator
- Bible Verse Collect - Free Bible Word Games
- MuslimOn: دعاء القرآن الآلي
- Bible Trivia
Other Apps
- BABEL: International Chat & Dating
- BitBible 繁體 (自動讀聖經)
- Injustice: God Among Us
- Jackpotland: Casino Slots
- Java Edition Mod for Minecraft
- Learn Guitar - Real Tabs
- Laser for dogs and cats
- Indian Constitution
- Haberler.com: Türkiye ve Dünya Gündemi
- Home Flip
- Idle Streamer!
- Home Plumbing System Guide
- IPTV ZEUS
- Money Rush
- Motivational Quotes
- Messages: Phone SMS Text App
- MindSync: AI Photo Editor
- Mp3 Music Download @Downloader
- My Talking Hello Kitty
- My Schedule
- NewsBreak: Local News & Alerts
- Mp3 Song Downloader App
- My Diary - Daily Diary Journal
- MPP - the social predictor
- Mosquito io
- Video Downloader for Twitter
- Find phone by claps
- Vector
- Cricball - Sports Live
- Crypto Miner: Bitcoin Factory
- Cyber Cleaner
- Disney Magic Kingdoms
- Deliveries Package Tracker
- Poly.AI - Create AI Chat Bot
- AVG Cleaner – Storage Cleaner
- Hollywood Story®: Fashion Star
- Bitcoin Pusher
- Car Trade Dealership Simulator
- Live Talk - Live Video Chat
- SPOX Sportnews
- Road Trip: Royal merge games
- FoxFM - File Manager
- GPS Map Camera: Geo tag Stamps
- Gallery - Photo Vault
- File Explorer
- Driving School 2017
- ET Markets : Stock Market App
- Todo List
- Tata Cara Ruqyah Lengkap
- かんたんゲームプレイヤー byGMO
- WSM - Women's Soccer Manager
- Voice Recorder Pro
- NDTV News App
- Sandbox - Physics Simulator
- KungFu Academy
- Match Academy : PVP Match3
- Bus Simulator Indonesia
- Disney Frozen Free Fall Games
- US Taxi Car Parking Simulator
- QR Code & Barcode Reader Plus
- DWG FastView-CAD Viewer&Editor
- Police Pursuit
- iScanner: PDF & OCR Scanner
- Grindr - Gay chat
- MetroZone
- Traffic Buster: Parking Escape
- Criminal Case
- Police Car Driving - Motorbike Riding
- The Weather Network: Local Forecasts & Radar Maps
- Speed Test & Wifi Analyzer +
- All Email Connect
- Document Reader: PDF, Word Doc
- Supermarket Simulator 3D
- Robux Easy Scratch
- Password Master
- WordBit Tedesco (German for Italian)
- Public Transport Simulator
- Wattpad - Stories you'll love
- Remote Play Controller for PS
- Radio Turkey - FM Radio
- Rakuten TV- Movies & TV Series
- EA SPORTS™ UFC® Mobile 2
- InDating — Dating and Chat
- Canal Constructor
- Golf Rival
- SHAREit: Transfer, Share Files
- Pixlr – Photo Editor
- Bitcoin Spin
- BuzzFeed - Quizzes & News
- AppLock
- Driving Zone: Germany
- CamScanner-PDF Scanner App
- Times Of India - News Updates
- Video downloader - Story Saver
- Portable ORG Keyboard
- Ynet
- Quick QR Scan
- CCleaner – Phone Cleaner
- King James Bible - Verse+Audio
- Currency Converter Plus
- Moovit: Bus & Train Schedules
- Pixel Art - Color by Number
- Pi Network
- My Calendar - Period Tracker
- Gas Station Idle
- Airport Security
- Moneywalk Step Counter&Rewards
- Snowball.io
- EMERGENCY HQ: rescue strategy
- Amerigo File Manager
- Weather Radar - Meteored News
- imo-International Calls & Chat
- Vinted - Buy and sell clothes
- Happy Color®: Coloring Book
- CHAM - Meet Random People
The list includes almost all the types of apps an app store could have in different languages, including VPNs that serve the purpose of hiding your online identity.
It is worth noting that a huge number of the apps were related to games, VPN, and recreation, pointing toward the intent of the culprit, who was looking to trace players across the globe.
Researchers found millions of mobile phone service coordinates in the U.S., Russia, and Europe.
Gravy Analytics accesses mobile phone location data received from its sources and sells to the US government and other companies.
In December 2024, the Federal Trade Commission banned a host of companies from accessing user location data. Some of these companies also worked with U.S. law enforcement agencies. The FTC banned Gravy Analytics and Venntel, its subsidiary, from selling, sharing, or accessing location data barring a few circumstances.