Google’s Threat Analysis Experts Detected Over 120 APT Attacks Per Day in 2020
- Google reports that APT groups were very active in 2020, exploiting COVID, elections, and more.
- The company thwarted DDoS attacks, warned phishing targets via email, and terminated YouTube accounts.
- Right now, the main theme used by sophisticated attackers is the 2020 US Presidential Elections.
Google’s Threat Analysis Group has posted a report where they detail their detection and warning work in 2020, focusing on APT activity in particular. This is a special category as state-supported actors are sophisticated, hard to detect, and very dangerous for their targets.
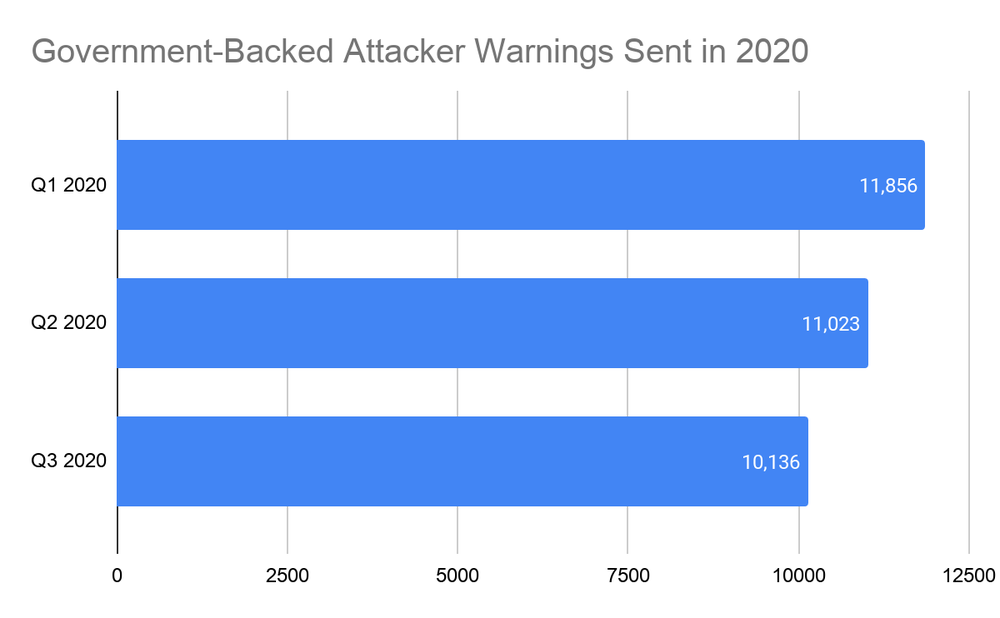
In numbers, there have been 33,015 confirmed attacks in 2020 so far (excluding October), which makes up for roughly 122 attacks per day. If we were to include the undetected APT activity, it is clear that state-supported hacking operations abound.
For whatever Google detects, the company is sending warnings to the targets via Gmail messages, so they can take appropriate action. Moreover, they share their findings with the Federal Bureau of Investigation to take legal actions against the hackers when possible.
From the beginning of 2020, the themes and lures have changed based on what’s hot at the moment. In Q1, the COVID-19 pandemic was an obvious choice, and threat actors from Russia and China engaged in impersonating the World Health Organization. In September, North Korean hackers joined this trend too.
In Q3 2020, the landscape changed to election-related themes, as the US Presidential Election is approaching. This intensified in September, and it follows an upward trend in October as expected, while the most prominent targets of these attacks are people working in political campaigns.
During this period, Google also terminated 3,000 YouTube channels that were considered to be fake news disseminators spreading false information on a range of topics. This takedown took place in Q3 2020, while the view counts and the subscribers these channels had were clear indications that they were products of spammers.
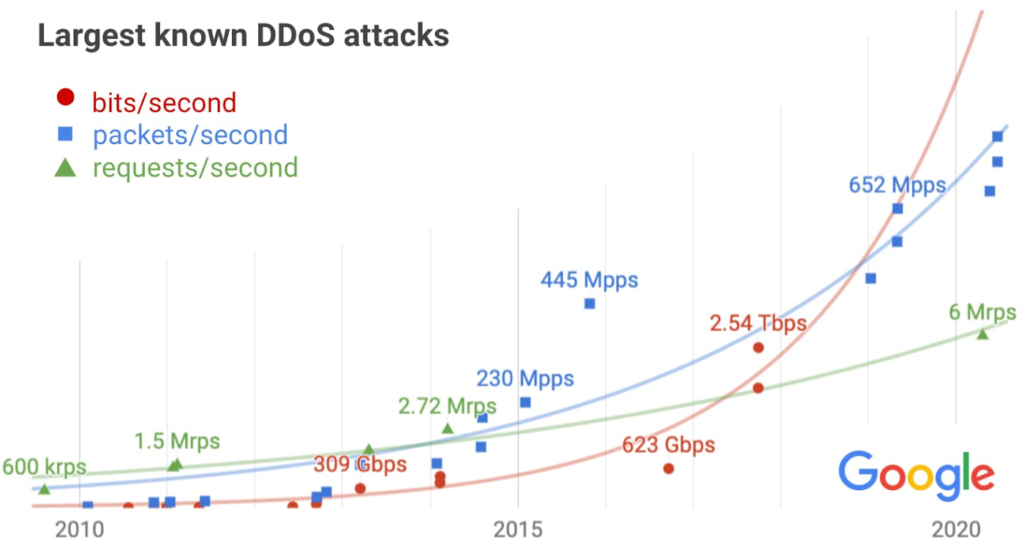
Finally, the DDoS threat is still rising, and Google has provided actual examples of the exponential growth in the field. They also revealed that in 2017, their Security Reliability Engineering team managed to stop a record-breaking (2.5 Tbps) UDP amplification attack that originated from Chinese internet service providers. APTs are igniting, supporting, orchestrating, or order large-scale DDoS attacks, and the upward trend is still present.