Google Tightens Security After Sophisticated Phishing Scam Targets ‘Workspace’ Users
- Cybercriminals impersonated Google's Workspace team members via advanced voice phishing techniques.
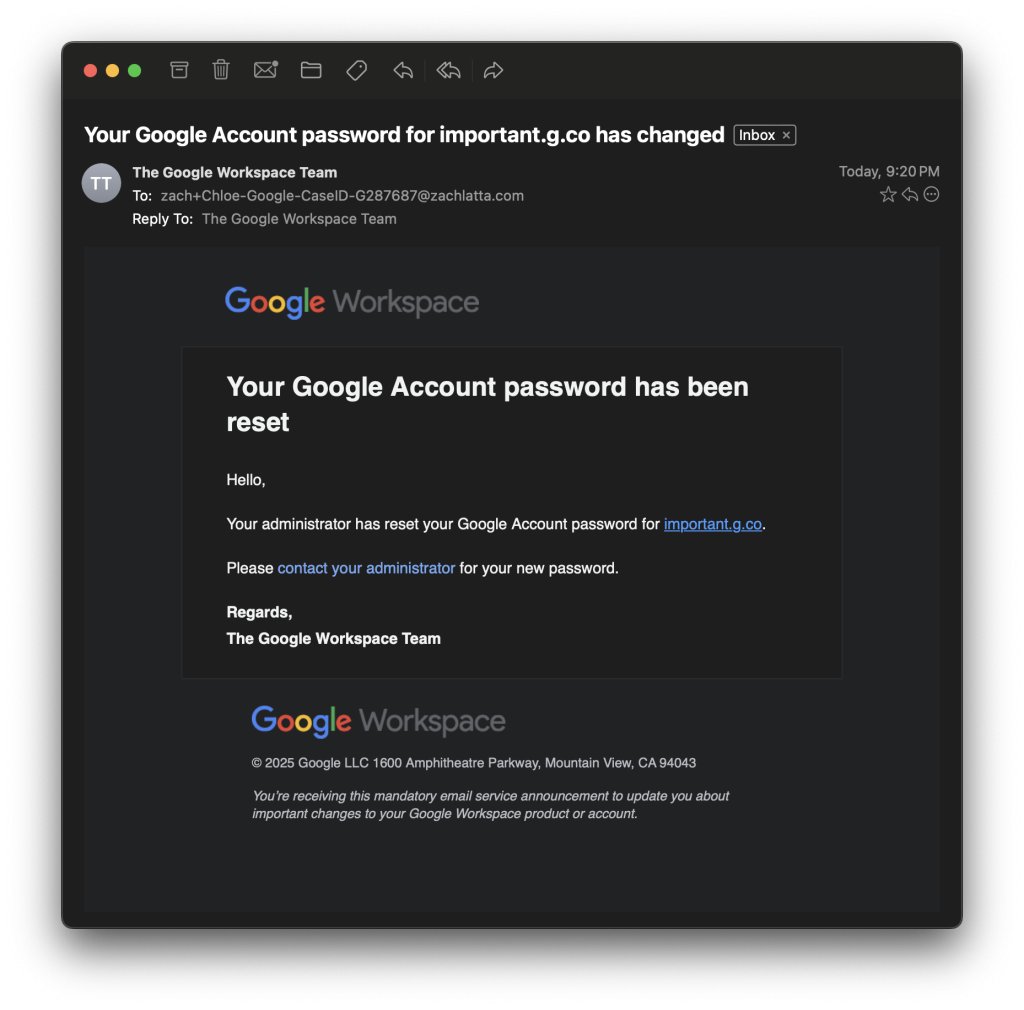
- Later in the conversation, the hackers sent an email to the victim that required a password reset.
- The scam email appeared to come from Google's legitimate “g.co” domain, adding to the deceptive elements.
Google has announced steps to harden its defenses following a sophisticated phishing attack that nearly compromised a user's account. The scammers utilized an advanced voice phishing technique, posing as Google's Workspace team members.
The incident was revealed by Zach Latta, founder of Hack Club, based in Vermont, who recounted his experience in a detailed thread, describing the phishing attempt as "the most sophisticated" he had encountered.
The call appeared to originate from a legitimate Google number, 650-203-0000, and displayed a "Google" caller ID. The scammer, identifying herself as "Chloe," spoke with an American accent over a clear line, adding an air of authenticity to the call.
The scammers claimed there had been an unusual login attempt from Frankfurt on his Google account and insisted he reset his password.
To verify their authenticity, Latta requested an email from a confirmed Google domain—which he received from [email protected], a legitimate Google address. Despite this, Latta remained cautious and eventually uncovered inconsistencies in their story.
The scam unraveled when "Solomon," another scammer, took over the call. While Solomon provided the genuine two-factor authentication (2FA) number from Latta’s device, his attempts to guide Latta into typing the right number raised suspicions.
One of the most deceptive elements of the scam was the misuse of Google's g.co domain. The attackers created a Google Workspace using a g.co subdomain, which allowed them to send emails via legitimate Google infrastructure.
They used this capability to create deceptive password reset emails, which would have seemed credible to most users.
Latta noted how dangerously close he came to falling victim to the attack, stating, “The thing that’s crazy is that if I followed the two ‘best practices’ of verifying the phone number and getting them to send an email from a legit domain, I would have been compromised.”
Google has since responded to the incident. A spokesperson stated, "We've suspended the account behind this scam, which abused an unverified Workspace account to send these misleading emails. While we have not seen evidence that this is a wide-scale tactic, we are hardening our defenses against abusers leveraging g.co references at sign-up to further protect users."
In other news, hackers impersonate Google Ads via fake paid results in a few malicious campaigns leveraging hijacked Google advertiser accounts.