Google Sheets Used as Command and Control Center in Campaign Impersonating Tax Authorities
- A novel malicious email campaign impersonating various tax authorities worldwide distributes Voldemort.
- The malware is used for intelligence gathering and additional payloads, adding cyber espionage to the mix.
- Its customized functionalities include exploiting Google Sheets to issue commands for the malware.
A sophisticated malware campaign targeting over 70 organizations globally in sectors such as insurance, aerospace, and technology uses a novel method of leveraging Google Sheets as a command-and-control (C2) mechanism, as per the latest report by cybersecurity researchers at Proofpoint.
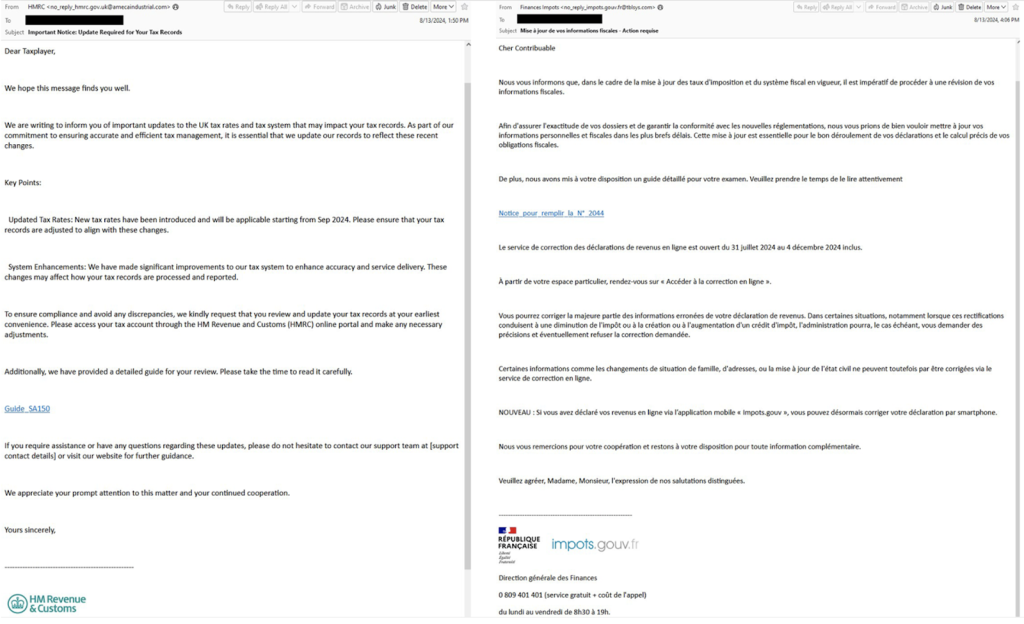
Active since August 5, 2024, the email phishing campaign impersonates tax authorities from the U.S., the U.K., France, Germany, Italy, India, Japan, and other countries that allegedly inform the recipients about supposed changes to their tax filings. At the moment, there are six confirmed victims, including one sandbox or a known researcher.
The emails appearing to be from the U.S. Internal Revenue Service, the UK HM Revenue & Customs, France’s Direction Générale des Finances Publiques, Germany’s Bundeszentralamt für Steuern, Italy’s Agenzia delle Entrate, India’s Income Tax Department, and Japan’s National Tax Agency contained Google AMP Cache URLs leading to a landing page hosted on InfinityFree
Later on, the messages linked directly to the landing page, which includes a "Click to view document" link that checks the browser’s User Agent. The page prompts Windows-based users to execute a shortcut file (directly a LNK file or contained in a ZIP archive) disguised as a PDF, which eventually leads to the download and execution of the Voldemort backdoor.
If the system is not Windows-based, the browser redirects to an empty Google Drive URL that allows the threat actor to track browser and network details for victims who were not served any malicious content.
Executing the LNK triggers PowerShell to run Python from a WebDAV share. The threat actors harvest details such as the computer name, username, domain, Windows version information, and CPU details.
After a password-protected ZIP file called test.png or logo.png is downloaded from OpenDrive, it extracts the legitimate WebEx-related CiscoCollabHost.exe, which sideloads CiscoSparkLauncher.dll – the Voldemort payload.
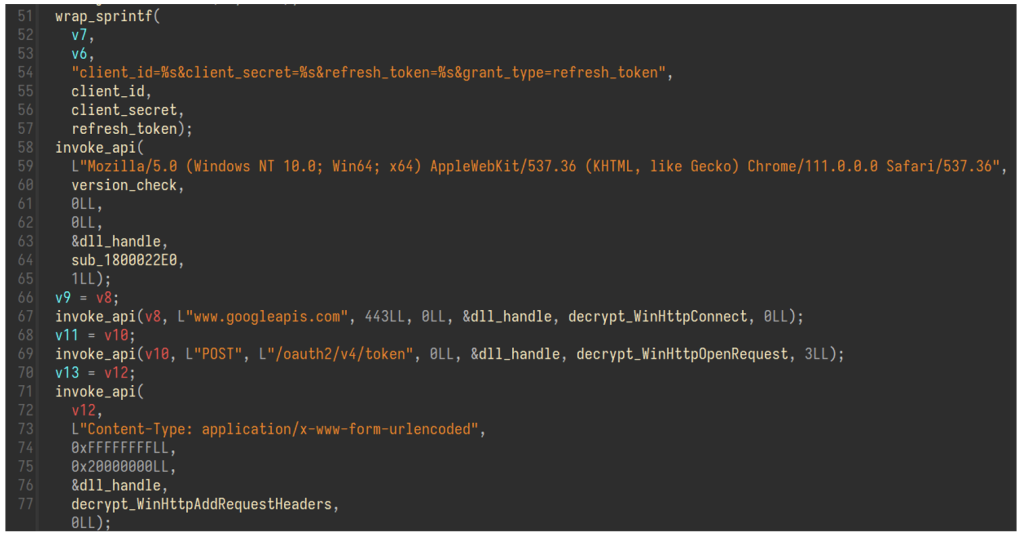
Employing Google Sheets infrastructure for C2, data exfiltration, and command execution. The malware uses Google Sheets with a client token and needs to authenticate first.
The client ID, client secret, and refresh token value are taken from the decrypted configuration and sent to receive an access token, which the malware uses to read the six commands for the bot.
Proofpoint researchers recently observed an increase in the abuse of Cloudflare Tunnels, specifically the TryCloudflare feature that allows an attacker to create a one-time tunnel without an account.