Google Project Zero Reveals Staggering iPhone Hacking Operation
- Project Zero revealed an iPhone 0-day exploiting operation that was active since September 2016.
- The implanted binary exfiltrated sensitive data from the devices of the victims and also tracked their GPS coordinates.
- The researchers believe that there are many undiscovered campaigns of this kind out there right now.
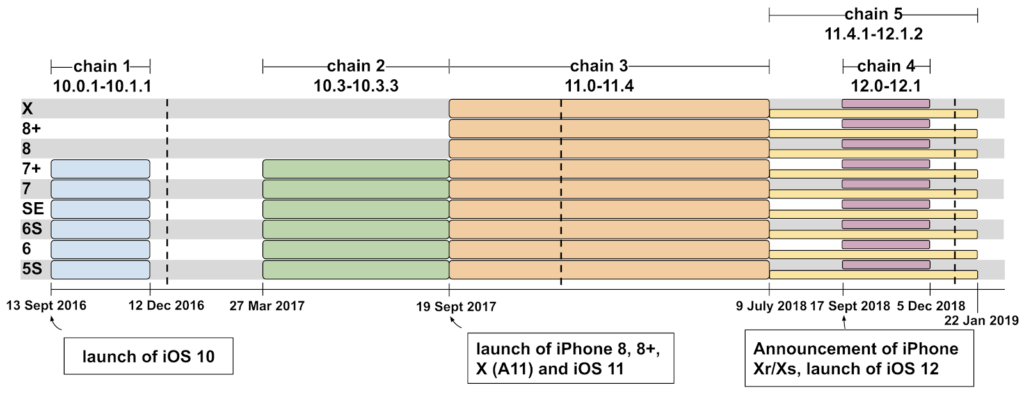
Project Zero has unveiled a stunning case of an iPhone hacking operation that has been going on since 2016. Apparently, Google’s Threat Analysis Group discovered a small set of websites that were conducting watering hole attacks against all of their visitors. The 0-day exploits that were used by these websites targeted iOS devices, so if a person visited them through an iPhone or iPad, they would be compromised. The notable fact is that upon further analysis, the researchers figured that the exploit chains covered almost every version ranging from iOS 10 to 12, while some were unpatched at the time of their discovery.
Source: googleprojectzero.blogspot.com
Google's researchers have discovered a total of fourteen vulnerabilities across five exploit chains, targeting the iPhone web browser, the iOS kernel, and even sandbox escapes. Two of the privilege escalation chains that were given the identifiers CVE-2019-7287 and CVE-2019-7286 were patched by Apple on February 7, 2019, six days after the Project Zero team informed them of the flaws. As the write-up of the researchers points out, this campaign was just one that they were lucky enough to discover, and that other groups of malicious watering hole sites are bound to be out there.
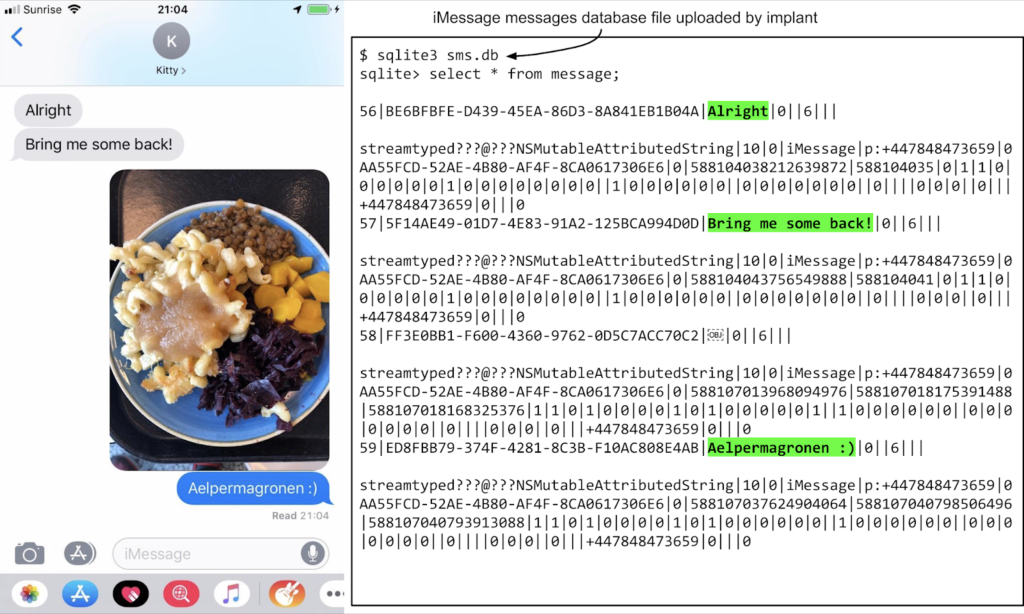
The goal of the attackers in the discovered campaign was to drop a binary in the “/tmp” directory, which then runs in the background with root privileges. The victim sees no visual indication of this, and there’s no process entry in the list to reveal that the implant is running. The role of the binary is to steal files from the device as well as to upload the GPS location data to the C2 server every minute. The implant even pries into databases that are used by private communication apps like Whatsapp, iMessage, and Telegram. Other data that is exfiltrated include Gmail messages, contact lists, and photos.
Source: googleprojectzero.blogspot.com
Now, what all of this means is that you could have this malicious binary working silently inside your iPhone device for a long time already, and you wouldn't realize a thing. The websites that acted as the watering hole points for this campaign were not revealed by Project Zero team, as their owners didn’t take part in the operation knowingly but were instead infected by actors who planted their code. However, the researchers clarified that they were moderately popular websites that received thousands of visitors per week.
Do you blindly trust iOS, or do you take extra security measures on your iPhone? Let us know in the comments beneath, or on our socials, on Facebook and Twitter.