Google Announces Private Join and Compute for Multi-Party Data Analytics
- Google wants to enable companies and organizations to get the most out of the data they collect.
- The company has created a platform for sharing and combining encrypted data sets without compromising the privacy of the people.
- This will help organizations evaluate their programs and products without exposing their users to other companies.
Google wants to enable organizations to do more with the data that is collected by the tech giant or the companies, but without compromising the users’ safety and privacy. In this context, they have rolled out Private Join and Compute, enabling third parties to conduct secure data computation and work together to squeeze every last drop of value from each data set without ever breaching the user privacy policies. This will work in a similar way to how the Checkup Chrome extension works, checking if the user login credentials have been leaked without Google ever getting to know what the credentials are.
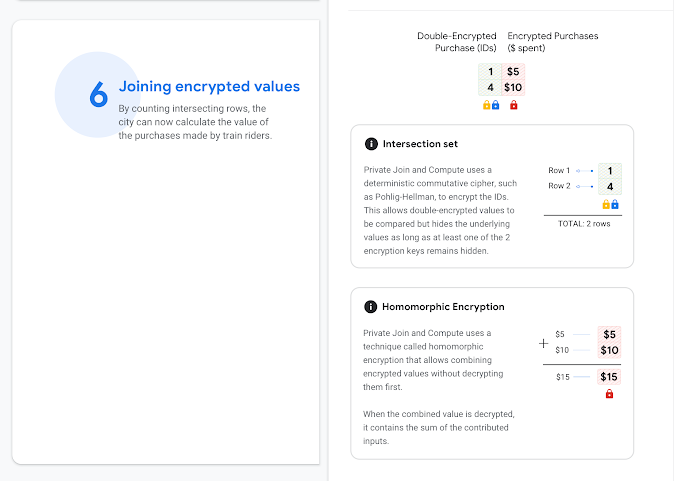
For all this to work as needed, the key ingredient is encryption. Multiple information-collecting organizations can combine their data sets and help each another draw additional and more complete conclusions while following a strict cryptographic protocol. Each organization encrypts the sensitive information of the collected data while allowing the other parties to access the data sets, but only partially, which corresponds to the information that is useful for the analysis and computation. When two or more organizations combine their data sets for a more complete result, the system formulates a type of aggregated statistics database, keeping the raw data and PII secret for everyone.
image source: security.googleblog.com
The two cryptographic techniques that are deployed are the private set intersection and the homomorphic encryption. The private set intersection enables two parties to combine their data sets and discover the identifiers that they have in common, but this is done while the identifiers remain encrypted. The homomorphic encryption allows the computation to take place on encrypted data, with all sensitive information remaining concealed. Combining these two techniques enables organizations to get the most out of the collected information without ever getting to learn anything about the people behind them.
Google presents multiple examples of how the Private Join and Compute could be used meaningfully in today’s world. From governments evaluating the impact of new initiatives, to industries getting to measure the impact of their demographic balancing efforts. Other examples involve the introduction of car safety standards and how these affect the numbers of car accidents in the following years, or the release of a new medicine and the determination of its efficacy in reducing the incidence of the targeted disease. All available as sterilized stats, without the organizations ever getting to know who crashed their car and who caught the disease.
Do you trust that the data exchange will be carried out in the safety of multi-layered encryption, or are you afraid that the risks of getting yourself exposed will only grow bigger? Let us know where you stand in the comments down below, or on our socials, on Facebook and Twitter.