Google Play Store Was Hosting 25 Italian Spyware Variants for Two Years
- A new case of extensive spyware presence in the Play Store has emerged, and the actors behind it could be the Italian authorities.
- The researchers can’t confirm the people responsible, but they have identified the creators of the spyware.
- The number of Italians who got spied is very low (a couple of thousands), but significant nonetheless.
A new case that shows the inadequacy of Google’s app filtering has just emerged, involving the Italian government, a surveillance cameras company named “eSurv”, and 25 malware apps for the Android platform. The discovery of the apps was made by the “Security Without Borders” non-profit organization who have identified 25 malware apps getting continuously re-uploaded to the Play Store, disguised as mobile operators service applications. As the apps were targeting Italian citizens, they were decoying local services and were downloaded by a couple of hundreds each.
image source: securitywithoutborders.org
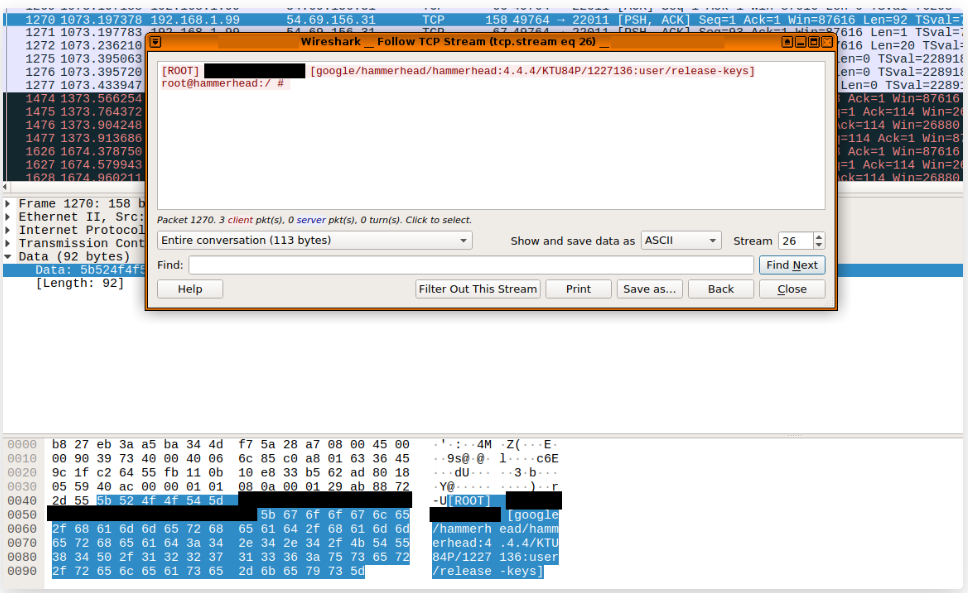
The researchers have named the two stages of the spyware as “Exodus One” and “Exodus Two”, while they noticed that the apps featured similar decoying and operation methods. The first stage served as a dropper, while it collected basic device data such as the phone number and the IMEI code, and sent it to the C&C server. The second stage brings the primary payload which is a “JAR” file, as well as several utilities (in the form of multi-architecture binaries), all neatly bundled together in a single Zip archive. The execution of the primary payload implements the data collection and exfiltration of the spyware.
Interestingly, the spyware tries to erase its trace from the battery consumption statistics screen, while it manipulates “protectedapps” to keep itself running in the background even when the user turns their screen off. The data that is collected by the spyware covers a wide spectrum of apps and sensitive phone information such as: the Viber messenger app data, the WhatsApp logs, the Wi-Fi passwords, the WeChat data, the GPS coordinates of the phone (live), the Facebook Messenger conversations, the address book, the Facebook contacts list, the calls log, the Calendar app events, the Gmail app information, and the cellular tower information. Moreover, it can record phone calls, retrieve browsing history and bookmarks from Chrome, and record ambient audio using the device’s microphone.
image source: securitywithoutborders.org
By analyzing various samples from 2016 to 2019, the researchers have traced the creators to be eSurv, an Italian surveillance cameras company. The C&C server points to an IP address that shares the same favicon as the company’s legitimate services, which concern the CCTV management business. Now, the shady part is the eSurv appears to collaborate closely with the Italian law enforcement agencies, so it’s possible that these spyware apps were developed on order of the Italian government, but this cannot be confirmed at this point.
There’s an indication through tentative evidence that shows that eSurv was ordered by the State Police to develop a “passive and active interception system”. Could Exodus be it? Security Without Borders cannot confirm this hypothesis, but it’s possible. Whatever the case, the evidence should be enough for Italian investigators and the representatives of justice to conduct their investigation, as the spyware’s functionality goes well beyond what’s allowed by the current legislation.
Do you live in Italy? How does this story resonate to your privacy protection expectations? Do you think that eSurv should be prosecuted by the country’s juridical system? Share your opinion in the comments section below, and don’t hesitate to do the same on our socials, on Facebook and Twitter.