Google OAuth Vulnerability Exposes Sensitive Data Through Defunct Domain Exploitation
- Attackers who re-create email accounts of repurchased inactive domains can use the OAuth function to gain access to connected SaaS accounts.
- Potentially compromised services include communication, project management, and even interview systems.
- The flaw could impact SaaS applications like OpenAI ChatGPT, Slack, Notion, and Zoom.
This article was updated with Google's statement on the matter.
A significant flaw within OAuth (Open Authorization) via Google's "Sign in with Google" authentication process could expose sensitive user data. Exploiting a vulnerability related to domain ownership, attackers could gain unauthorized access to various apps, including critical SaaS platforms.
According to Truffle Security, the vulnerability stems from the ability to purchase domains of failed startups and re-create email accounts once used by former employees.
While this doesn’t allow access to previous email data, it does enable attackers to utilize these accounts to log in to SaaS products initially accessible with those credentials.
Other compromised platforms include communication, project management, and even interview systems, exposing sensitive business and candidate data to exploitation.
Users can grant websites or applications access to their data from other services such as Google via OAuth without sharing passwords. When using the "Sign in with Google" feature, Google shares key user claims—like email and domain information—with third-party applications to authenticate users.
Problems arise when apps rely solely on these claims for user authentication. If an organization ceases operations and its domain becomes available for purchase, attackers can acquire the domain, re-create email accounts, and use these to regain access to SaaS accounts tied to the defunct domain.
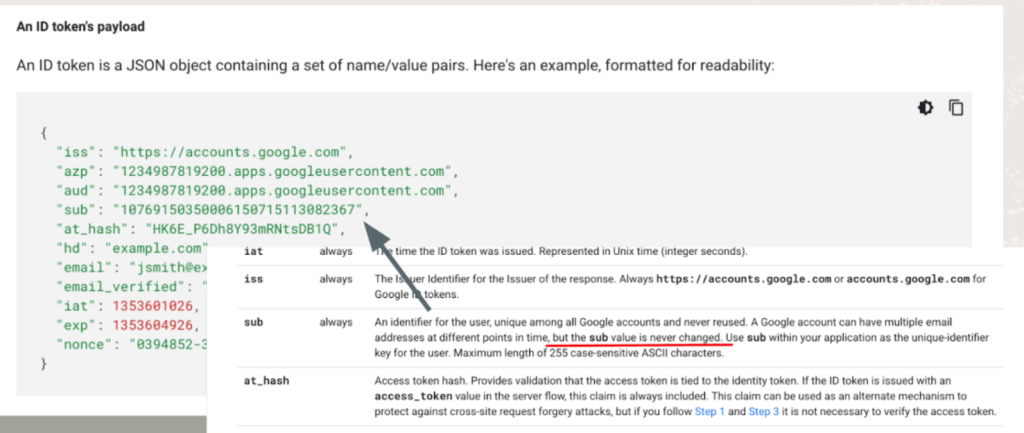
Moreover, Google's OAuth ID tokens include a unique user identifier—the "sub claim"—that could technically mitigate this vulnerability. However, Truffle found this identifier unreliable in practice. By contrast, Microsoft Entra includes both "sub" and "oid" claims, ensuring an immutable user identifier to prevent such exploits.
This vulnerability affects millions of users across widely adopted SaaS applications such as OpenAI ChatGPT, Slack, Notion, and Zoom. The potential compromise is particularly concerning for accounts linked to HR systems, exposing highly sensitive personal and financial information.
Google initially classified the flaw as "intended behavior" but reopened the bug report on December 19, 2024, after further evaluation. The tech giant awarded Dylan Ayrey a bounty of $1,337 and has labeled the issue as an "abuse-related methodology with high impact."
“We appreciate Dylan Ayrey’s help identifying the risks stemming from customers forgetting to delete third-party SaaS services as part of turning down their operation. As a best practice, we recommend customers properly close out domains following these instructions to make this type of issue impossible," a Google spokesperson reached out for an official statement. "Additionally, we encourage third-party apps to follow best practices by using the unique account identifiers (sub) to mitigate this risk.”
The message further stated that this scenario poses a risk to data stored on third-party platforms rather than by Google. Clarifications mention that "a fix wasn’t necessary because strong and appropriate protection is already in place. The sub field is the immutable identifier that the researcher is calling for – we strongly urge developers to use it to provide extra protection."
Google's official position is that their specialists have seen no evidence to support the assertion that the sub field is not an immutable and unique identifier, further adding that Google documentation for developers has been updated to make this guidance even more prominent.