Google Ads Phishing Campaign Targets Microsoft Advertisers with Sophisticated Techniques
- Google sponsored results are again used for malicious purposes, this time targeting Microsoft advertisers.
- Cybercriminals leverage traffic filtering with “White Pages” and Cloudflare human verification.
- The phishing domain for the Microsoft Advertising platform mimics the legitimate one and even uses the real domain with an added typo.
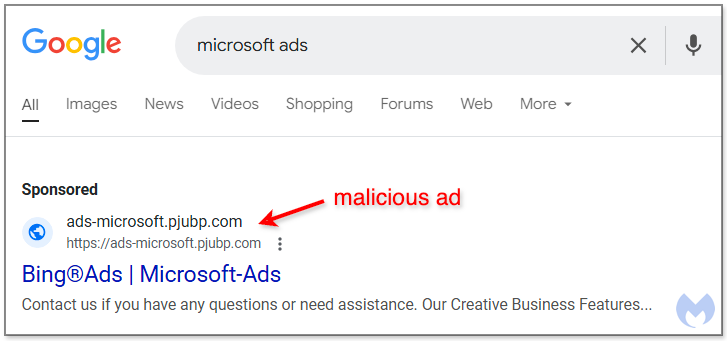
Microsoft Ads users are targeted in a newly uncovered phishing campaign aiming to steal login credentials through malicious advertisements appearing on Google Search through fraudulent Google-sponsored results for "Microsoft Ads."
The phishing scheme exploits the ad ecosystem, presenting these malicious links within ads that bypass Google's security checks, leveraging advanced techniques to avoid detection.
Instead of being directed to the official Microsoft Advertising platform, unsuspecting users are taken to a meticulously crafted phishing page that mimics the legitimate ads.microsoft.com site.
To evade security scanners, VPNs, and web crawlers, unwanted IPs are redirected to harmless pages, often appearing as generic marketing content. This masking technique ensures that the true phishing intent remains hidden from cybersecurity tools.
Genuine users are presented with a legitimate Cloudflare challenge to verify they are human. This step builds trust and misleads users further into the phishing sequence, distinguishing it from other commonplace phishing techniques like fake "ClickFix" challenges.
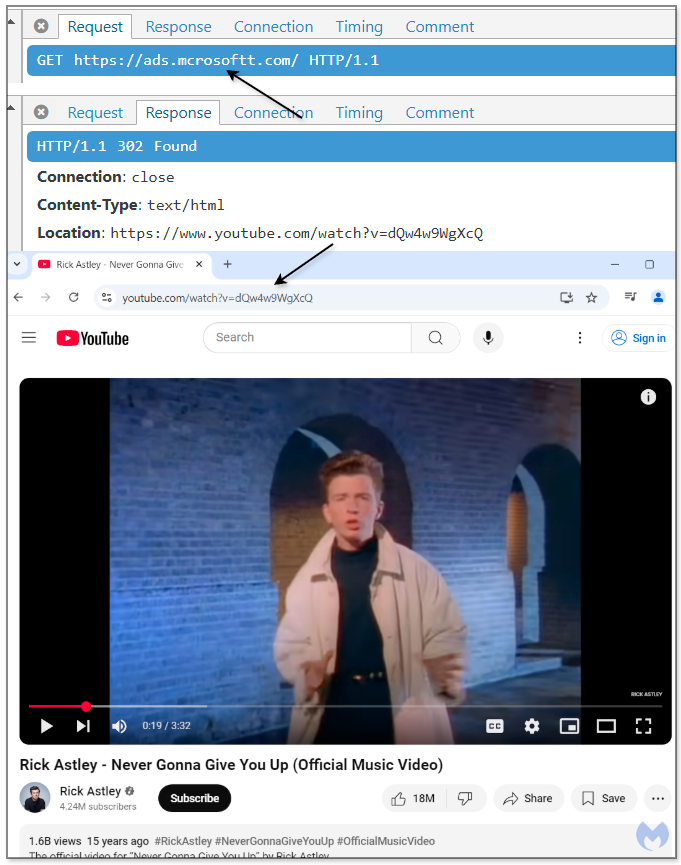
Users cleared through these tests are finally redirected to a phishing page via a deceptive URL, such as ads[.]mcrosoftt[.]com. The URL design closely imitates Microsoft’s official domain to mislead users into believing they are accessing a legitimate platform.
Notably, attempts to directly access the phishing domain without passing through the ad click trigger a humorous “rickroll,” an internet meme designed to divert undue attention and discourage further scrutiny.
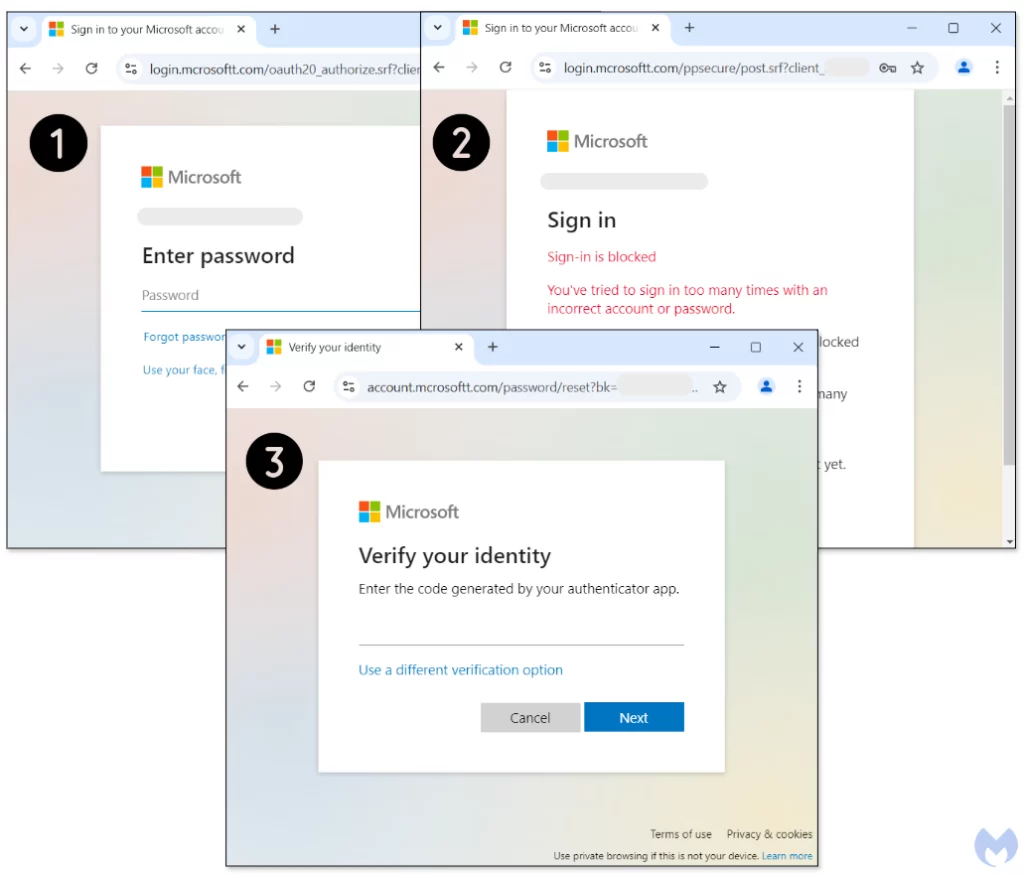
The final phishing page is designed to push users into entering their credentials by showing a fake error message that prompts a password reset.
The attackers aim to trick users into surrendering sensitive information, including bypassing two-factor authentication (2FA), a feature now standard in phishing kits due to the growing adoption of 2FA measures worldwide.
The stolen credentials could potentially be used to access Microsoft Ad accounts, enabling threat actors to exploit these accounts for further malicious campaigns or financial gain.
Evidence suggests that this campaign is not isolated. The phishing infrastructure dates back at least a couple of years, as identified through patterns in the web artifacts such as "favicon.ico" hashes.
These artifacts trace back to additional infrastructure hosting malicious domains, many of which are associated with Brazil’s regional ".com.br" top-level domain.
Though the full extent of this phishing operation remains unclear, its scale could reach far beyond Microsoft Ads, potentially targeting other major platforms like Facebook Ads and additional advertiser ecosystems.
This discovery comes just days after a similar campaign was seen targeting Google Ads accounts.