‘GoodSender’ Malware Found in Telegram Bot API
- Telegram chatbots similar to those implemented by Facebook and WhatsApp were found to contain malware.
- The malware known as ‘GoodSender’ is a common Windows malware that was discovered last year.
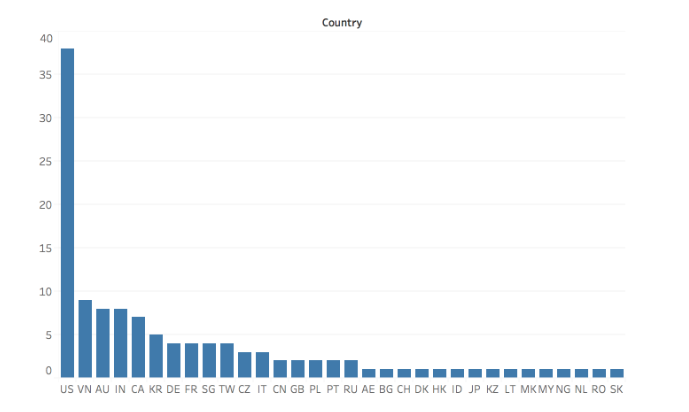
- The malware has affected 120 users so far with US users being the most targeted.
Telegram is known of its high-end security and encryption but it seems like the popular messaging app’s bot API can be compromised by the Windows ‘GoodSender’ malware. Firstly, not all users have been affected by the malware as the bot is used only by a small number of Telegram users. An estimated 120 users have been affected globally.
Telegram’s bot API is used to automate communications like news, updates and other more by teams and businesses. For the vulnerability to be exploited a man in the middle attack is needed with attackers intercepting communications between the bot and users. The telegram has already been informed by the vulnerability by Forcepoint.
Image Courtesy of Forcepoint
According to researchers from Forcepoint “Malware that uses Telegram as a command and control channel typically uses the Telegram Bot API for communications. In the course of an investigation into one piece of malware, we discovered a significant flaw in the way Telegram handles messages sent through its Bot API.”
The information that can be intercepted includes usernames, passwords and even the IP addresses of the victims. The Bot API is also not secured using Telegram’s own encryption protocol. Instead, it uses Transport Layer Security (TLS) protocol that is seen in HTTPS. With most data shared between bots and users being non-confidential in the first place, there is not much to be worried about and most enterprise users will not be affected by it.
Users can avoid being in groups or channels which have bots present to avoid any security risks until the messaging app resolves the issue. It is also recommended to have a good anti-malware software on your system to avoid the Bot from being exploited. While bots are made by third-party developers using the platform’s own API, it can be remedied if Telegram changes the security protocol from TLS to MProto.
What do you think about the malware found in the Bot API? Let us know in the comments below. Also, to get instant tech updates, follow TechNadu’s Facebook page, and Twitter handle.