Global Espionage Operation by I‑SOON’s FishMonger APT Group Unveiled
- The FishMonger group operated by I-SOON is directly responsible for a global espionage campaign under the Winnti Group umbrella.
- Operation FishMedley deployed advanced implants like ShadowPad, SodaMaster, and Spyder, usually present in China-affiliated operations.
- Targets include Taiwan, Hungary, the United States, Thailand, and France.
Operation FishMedley, a massive global espionage campaign attributed to the China-aligned APT group FishMonger focuses on highly strategic verticals, including government agencies, NGOs, and think tanks across Asia, Europe, and the United States.
An investigation unveiled by ESET researchers confirms that FishMonger, a group operated by I-SOON, is directly responsible for the campaign, working under the broader Winnti Group umbrella.
ESET researchers have provided details about the verticals targeted in this operation, which include:
- Taiwan (governmental organization)
- Hungary (Catholic organization)
- United States (NGOs and global Catholic charities)
- Thailand and France (governmental and geopolitical think tanks)
Their tools and techniques include previously undocumented implant RPipeCommander that serves as a reverse shell for executing remote commands, ShadowPad and SodaMaster backdoors – which are powerful implants customized to evade detection and maintain persistence within networks – and Spyder, a modular malware capable of operating as a backdoor while facilitating lateral network movement.
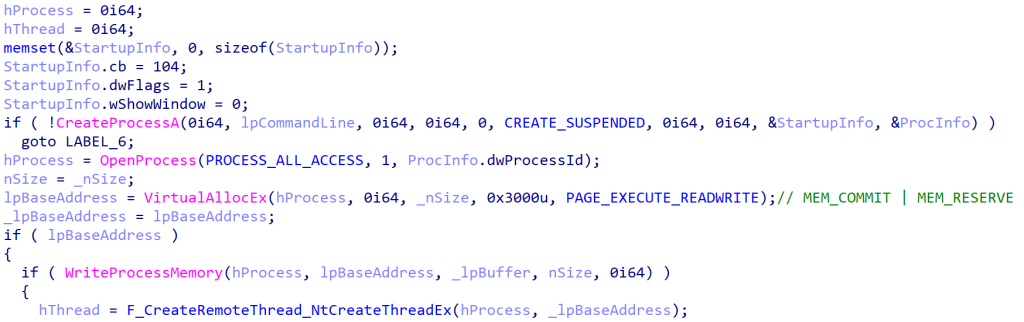
At one victim organization, they compromised administrative credentials, enabling them to deploy implants network-wide via local admin consoles. Using impersonation tools like Impacket, attackers extracted sensitive credentials, dumped operating system processes, and conducted reconnaissance to identify further exploitation opportunities.
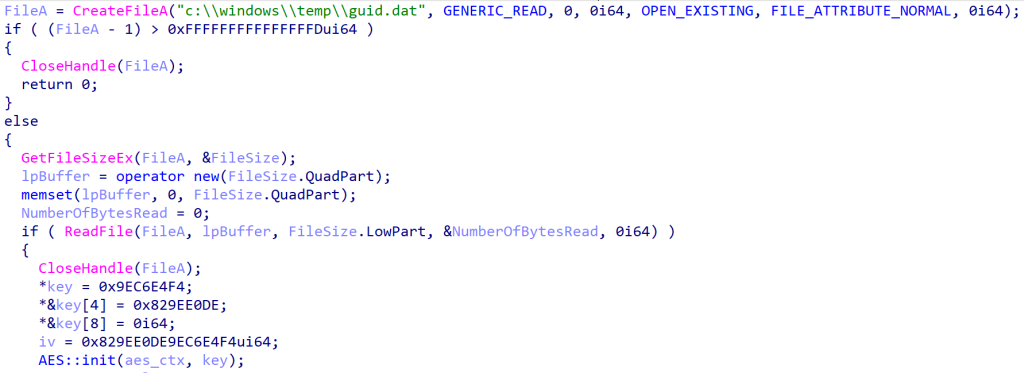
FishMonger relied on ShadowPad, a widely known modular backdoor supplied specifically to China-aligned threat actors. Leveraging tools like ScatterBee-packed loaders, FishMonger staged ShadowPad via compromised local systems and exploited legitimate executables to sideload malicious DLLs.
Similarly, SodaMaster, previously associated with APT10 (also known as Red Apollo, Cicada), was analyzed during the campaign. This backdoor, known for its capability to analyze browser credentials, operated stealthily across various compromised systems.
The U.S. Department of Justice (DOJ) recently unsealed an indictment against I-SOON employees and Chinese Ministry of Public Security officers, who orchestrated multiple espionage campaigns spanning 2016 to 2023.
The indictment aligns with ESET’s research, which clustered seven major compromises documented as part of Operation FishMedley in 2022.
ESET researchers affirm that FishMonger, responsible for Operation FishMedley, is a direct operational arm of the Chengdu-based contractor I-SOON. This conclusion is further corroborated by ESET’s analysis of leaked I-SOON documents from 2024, alongside independent attribution to the Winnti Group network.
The indictment by the DOJ represents a significant development, linking I-SOON to a persistent campaign of cyberespionage targeting critical international organizations. U.S. authorities have also added I-SOON-affiliated individuals to the FBI’s Most Wanted list for their involvement in long-term cyber warfare activities.