GiveWP WordPress Plugin Flaw Exposes 100,000 Websites to Remote Code Execution Attacks
- A flaw in the GiveWP donation plugin permitted unauthenticated PHP Object Injection.
- The vulnerability enables attackers to perform remote code execution and arbitrary file deletion.
- The now-patched plugin has more than 100,000 active installations at the moment.
A now-patched GiveWP plugin vulnerability left more than 100,000 WordPress websites exposed to potential unauthenticated Remote Code Execution (RCE) attacks, according to the latest report from Wordfence. Tracked as "CVE-2024-5932," the flaw has a CVSS score of 10.0 and impacts all versions up to 3.14.1.
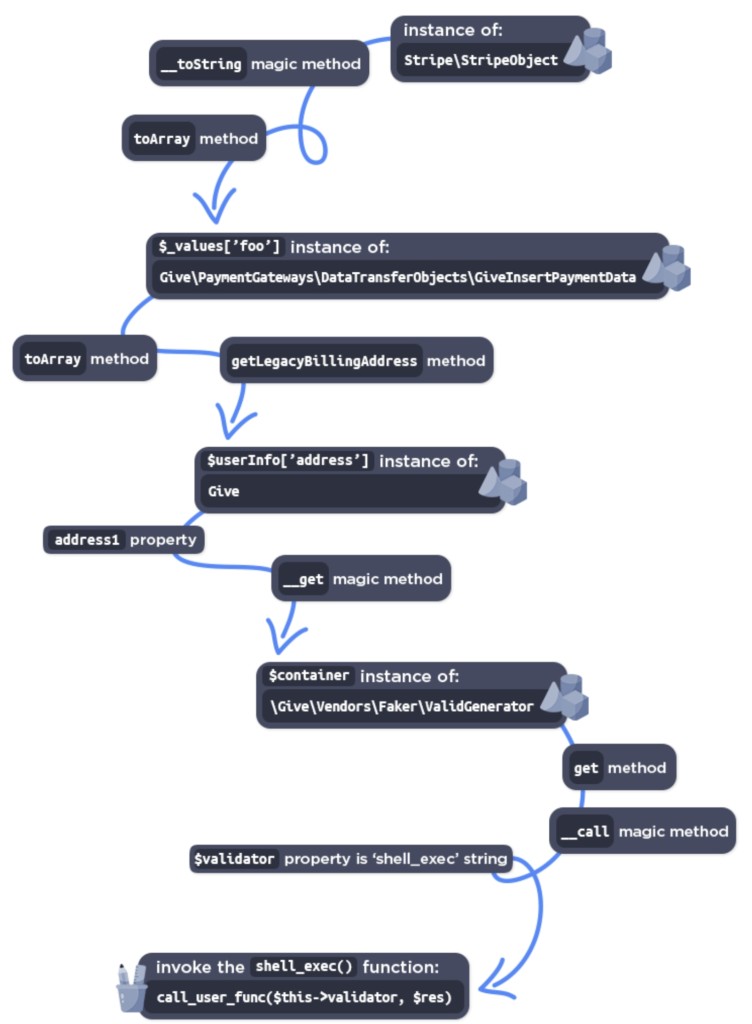
The unauthenticated PHP Object Injection via deserialization of untrusted input from the ‘give_title’ parameter leads to RCE vulnerability in GiveWP (Donation Plugin and Fundraising Platform). It can be leveraged via an existing POP chain present in the plugin to execute code remotely and delete arbitrary files.
The root of the issue seems to be the function the plugin uses to handle and process donations, which validates the post data right at the beginning, checking whether the post data contains serialized values.
PHP uses serialization to store complex data, which helps store settings in bulk, but it can also be used to store PHP objects.
An attacker controlling a serialized object passed into unserialize() can also control the properties of the created object and hijack the app flow by controlling the values passed into magic methods.
GiveWP includes features such as customizable donation forms, donor management, reports management, integration with third-party gateways and services, and much more.
The vulnerability has been fully addressed in version 3.14.2 of the plugin.
Recently, a new variation of the “gtag” credit card skimming attack called Caesar Cipher Skimmer impacted almost 80 sites in the first two weeks after its discovery. It was deployed to several different CMS platforms, infecting WordPress, Magento, and OpenCart.