GitHub Leveraged for Distributing Lumma Stealer, Vidar Stealer, SectopRAT, Cobeacon
- Hackers host infostealers on GitHub to avoid suspicion by leveraging the platform’s secure URLs.
- Unsuspecting users download seemingly legitimate files that ultimately exfiltrate information.
- A case study reveals two malicious EXE files with temporary certificates were downloaded from GitHub.
A malicious campaign uses GitHub’s release infrastructure as an initial access point to distribute Lumma Stealer and malware variants like SectopRAT, Vidar, and Cobeacon. By hosting these files on GitHub, attackers exploited the platform’s secure URLs to evade initial suspicion.
Victim users downloading files from these seemingly secure sources unknowingly facilitated the exfiltration of sensitive data and enabled malware execution on their systems, according to the latest security report from Trend Micro’s Managed XDR team.
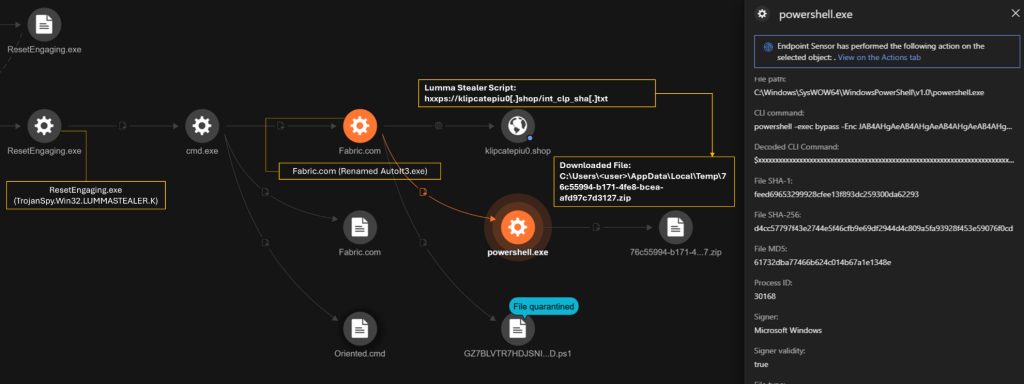
Once activated, Lumma Stealer was observed dropping and executing additional malicious tools, creating multiple directories, and staging exfiltrated data. Attackers employed advanced techniques, like leveraging PowerShell commands, for persistence and avoiding detection.
The investigation uncovered that the tactics, techniques, and procedures (TTPs) exhibited overlap with those of the Stargazer Goblin group, known for using trusted platforms like GitHub and compromising legitimate websites to host and distribute their payloads.
Two specific cases involving Lumma Stealer illustrate the campaign’s methodology. Both incidents stemmed from users downloading files hosted on GitHub’s release infrastructure.
The case study said an executable named Pictore was downloaded via Google Chrome from a GitHub-hosted release asset with a temporary URL, authenticated and valid only for 300 seconds. The file was signed by ConsolHQ LTD, but its certificate was revoked later.
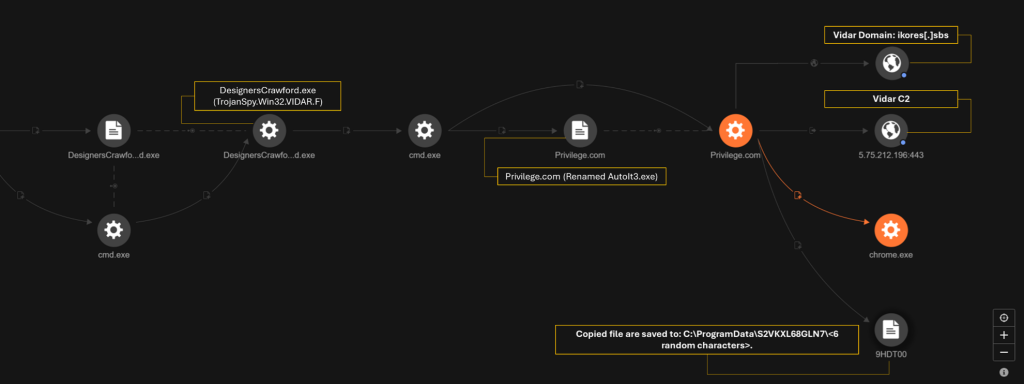
Similarly, another executable was identified and downloaded through the same mechanism. Signed by Verandah Green Limited, its certificate was also revoked after detecting malicious behavior.
Both files exhibited identical behaviors, functioning as Lumma Stealer variants designed to collect and exfiltrate system and user data. Victim systems provided sensitive information like credentials, cryptocurrency wallet data, operating system details, hostname, user directories, and temporary directory content to attacker-controlled servers.
Additionally, these files dropped multiple tools, including SectopRAT, Vidar Stealer, and Cobeacon, executing them from dynamically generated folders in the temporary directories.
Lumma Stealer and the accompanying malware variants operated in multi-stage attacks, utilizing command and control (C&C) servers to execute commands and avoid detection.
The malware documented critical data, including RAM size, display adapter details, operating system version, and user-specific paths, and exfiltrated the stolen data to attacker-controlled servers using encrypted communication channels.
Tools such as PowerShell scripts ensured persistence, alongside additional Trojans that extended the malware’s capabilities.
Trend Micro’s analysis identified a consistent pattern of redirecting users from compromised legitimate websites to GitHub-hosted payloads. These malicious files were temporarily hosted and disguised with valid-sounding file names to maximize trustworthiness.