Ginp is a New Dangerous Banking Trojan for the Android Platform
- Ginp is a new banking credential and card details stealer targeting Spanish Android users.
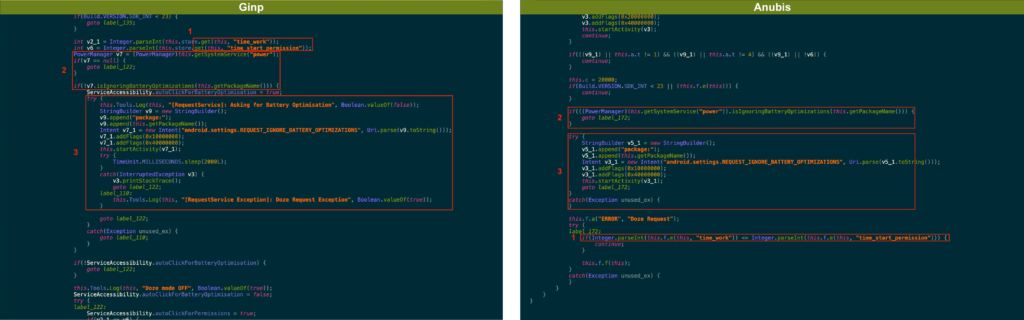
- The Trojan was built from scratch but also features code parts from the Anubis malware.
- Currently, it serves overlays in a careful and systematic manner, while hiding its icon from the user.
Researchers from Threat Fabric warn the public about the existence of a new malware called “Ginp”, and which targets Android devices. This new strain focuses on the stealing of banking information from its victims, and it’s currently under active development with many new versions spewing out every month. While Ginp is thought to have been created from scratch, it features code parts from the infamous and highly successful Anubis banking Trojan. Ginp is mainly directed to Spanish users and Spanish banks, trying to steal login credentials and credit card details through deceptive overlays.
Source: Threat Fabric blog
The most recent version of Ginp came out this month, and it introduces the capability to grant the malware app the device admin permission. In addition to this, there’s a new endpoint that opens the way to download more payloads or new configurations for the Trojan. In the present version, the targets list includes the 24 applications of the following Spanish banks: Caixa bank, Bankinter, Bankia, BBVA, EVO Banco, Kutxabank and Santander. Upon its first launch, the Ginp malware asks the user for the Accessibility Service privilege which only opens the way for the app to grant itself more permissions as required for the overlay attacks.
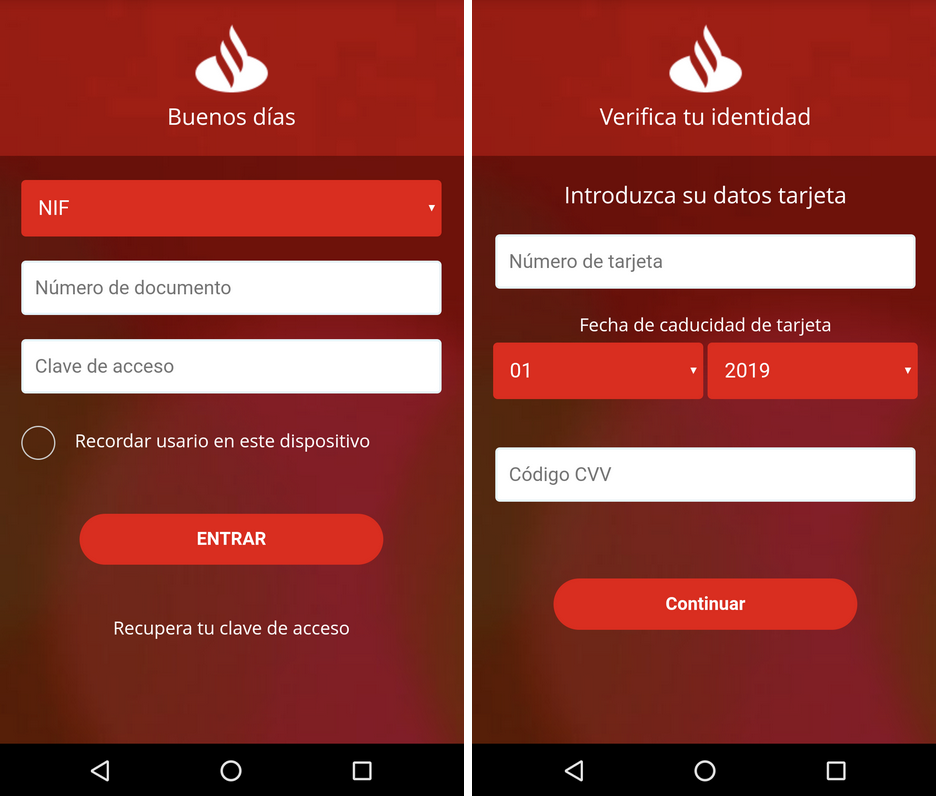
Ginp is taking full control of the SMS communication on the infected device, harvesting message contents, listing them, sending messages, and even forwarding any to the C2 infrastructure. The malware can also forward calls, steal the victim’s contact list, and more. To stay clear from removal, the app icon is hidden while the overlays are not popping up at random times. This helps reduce the victim’s suspicion, and at the same time, increase the rate of success for the actors. The overlays are loaded on an HTML page that is provided directly by the C2. As shown below, the actors are not only trying to steal the login credentials but also the credit card details as well.
Source: Threat Fabric blog
All versions of the Trojan come with a generic card details grabber to load on unidentified cases. This one can potentially trick even the non-Spanish victims since it poses as the Google Play Store app. In the older versions, the malware also targets Facebook, WhatsApp, Skype, Twitter, Chrome, Instagram, Snapchat, Viber, so beware. Ginp is under active development, so it will continue to get more powerful and more tricky in the following months.
Have you fallen victim to the Ginp Trojan? Let us know of the details in the comments section down below, or on our socials, on Facebook and Twitter.