The Ginp Banking Trojan Returns with Fake Incoming SMS Tactics
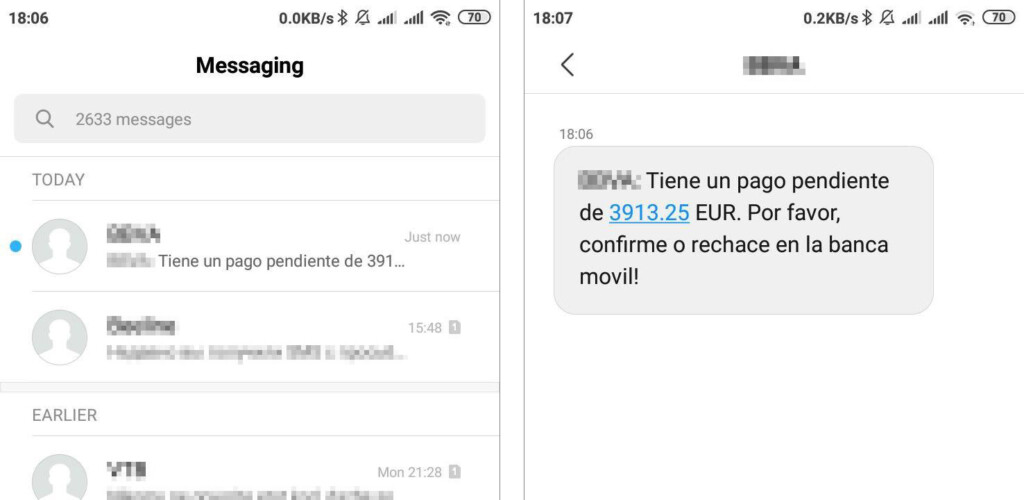
- Ginp can now generate SMS messages locally on the phone and spoof any sender and any content.
- While the numbers that are used are legitimate, the messages were never sent from them.
- The text messages contain links that lead to phishing overlays that steal credit card data.
Back in November 2019, we discussed a new malware called “Ginp” which was capable of stealing banking information from Android devices. The researchers of Threat Fabric who made the discovery warned the public about Ginp being under active development, so whatever applied at that time could easily change or get enriched in the near future. As Kaspersky researchers report now, this is precisely what happened with the most recent versions of Ginp, as the mobile banking Trojan is now capable of faking incoming SMS messages to trick its victims.
The researchers began noticing this tactic since the start of this month. Ginp started generating SMS messages with any content it wanted, and with any sender that needed to be faked. In most of the cases, the spoofed sender was a bank or Google. These SMS messages warn the recipient of suspicious transactions that have taken place on their account and offer a link that opens a fake web overlay that is phishing people’s card details and online banking user credentials. Since the fake SMS messages use the real phone numbers of the spoofed bank, if the victim tries to call them back they would falsely confirm that they really come from the institution.
Source: Kaspersky Blog
Ginp’s developers have previously experimented with notifications, but they now prefer SMS because they seem to add a crucial element to the legitimacy of the trickery. Users tend to disregard notifications since they can be generated by any app on the phone and are usually unimportant. Text messages on the other side come from actual numbers, so the victims are bound to read them sooner or later. However, as we see now, these messages aren’t always real and checking the phone number isn’t enough on its own to prove if they were generated locally or not.
The best way to mitigate the risk is to avoid following any links contained in text messages. Banks never send links to online banking platforms via SMS, and if you need to check something they’ll urge you to do it by firing up the bank’s official app. That said, you should avoid installing apps from outside the Play Store, regularly review the permissions of the apps that are already running on your phone, and use a mobile protection solution from a reputable vendor. Remember, Ginp is still under active development, so this won’t be the last trick up its sleeve.