Ghostwriter APT Threatens Ukrainian and Belarusian Opposition Organizations
- Ghostwriter APT shifted its interest towards the Ukrainian government and Belarus opposition organizations.
- The malicious lures often contained publicly accessible information, creating an appearance of credibility.
- Analysts confirm the phishing campaign’s alignment with Belarusian state interests.
The Ghostwriter advanced persistent threat (APT) recently began targeting Belarusian opposition activists and Ukrainian government entities, leveraging weaponized Excel documents to deliver malware payloads – including a new variant of the PicassoLoader downloader.
Previous exploits focused on tactics like weaponized Excel files containing malware such as PicassoLoader and Cobalt Strike, according to a recent SentinelLABS security report.
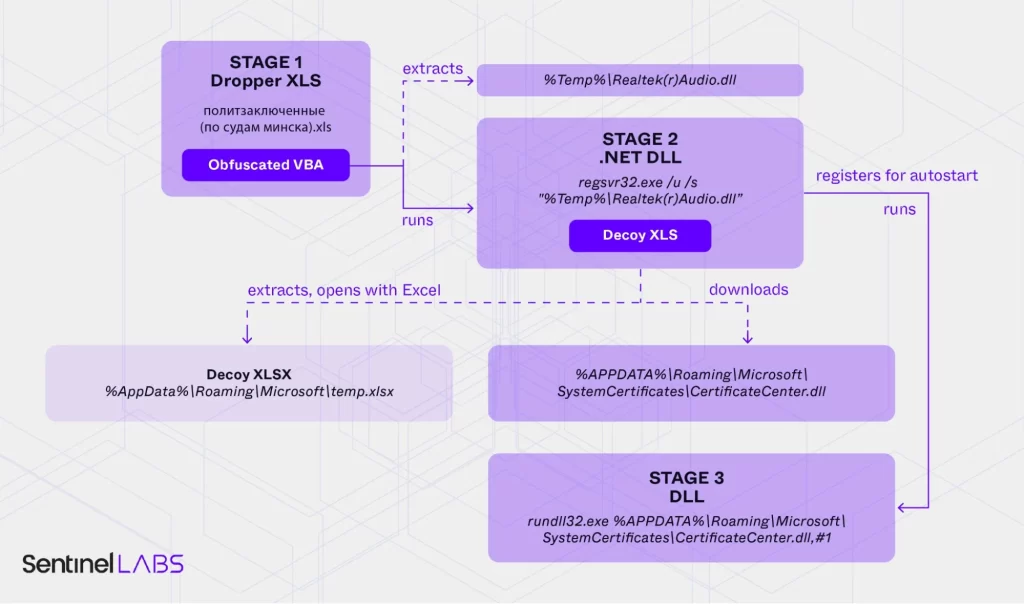
Ghostwriter operators rely heavily on phishing emails containing seemingly legitimate Excel documents to deliver malware. These documents employ obfuscated VBA macros, which execute upon opening and deploy malicious DLL files to the victim’s system.
Ghostwriter’s operators employ advanced evasion methods, such as ConfuserEx and Macropack to shield malware from detection and malicious Excel decoys that mimic legitimate content to trick users, such as court records or anti-corruption initiatives.
Tools with themes like "Anti-Corruption Initiative" and "Supplies for the Armed Forces" targeted Ukrainian recipients to infiltrate governmental systems.
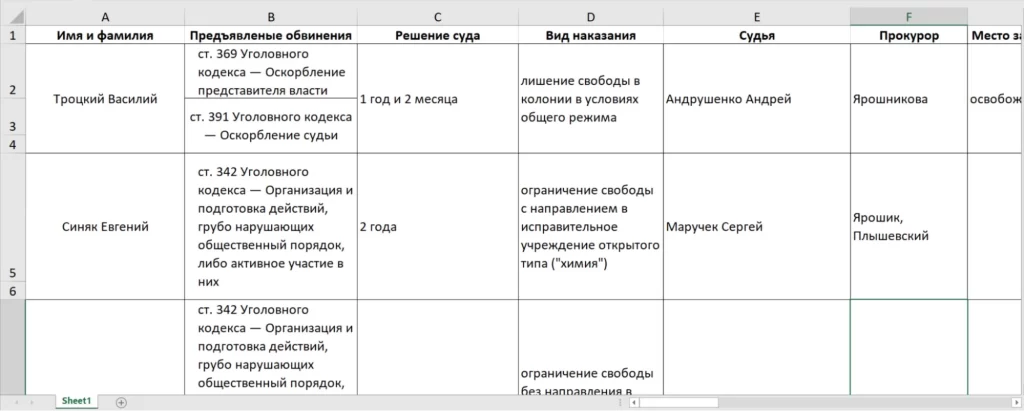
One notable example includes an Excel file titled “Political Prisoners in Minsk Courts,” sent to Belarusian targets. The malware disguised itself as a report on judicial proceedings involving political prisoners in Belarus.
Once opened, the file executes a simplified variant of PicassoLoader, a malware tool linked to Ghostwriter. While analysts note evolving tactics, the consistent use of PicassoLoader malware and ConfuserEx obfuscation tools directly ties these operations to the Ghostwriter group.
These campaigns align closely with Belarusian state objectives, particularly in their pursuit of suppressing domestic opposition and undermining Ukraine’s government.
The Ghostwriter campaign, active since 2016, has transitioned from primarily targeting European political organizations to engaging in cyber espionage tailored to Belarusian activists and the Ukrainian government.
Security researchers have traced the campaign’s roots back to the summer of 2024, with active operations ramping up in late 2024 and continuing into 2025.
Ghostwriter is a sophisticated APT often linked to Belarus and tracked as UNC1151 or UAC-0057. Known for combining disinformation campaigns with cyberattacks, it targets European nations on politically sensitive issues.